智能设备-华为巴龙系路由器固件提取及修改
推荐 原创【智能设备-华为巴龙系路由器固件提取及修改】此文章归类为:智能设备。
有人从HK搞了一批华为定制路由器,可以上SIM卡共用数据流量的。web界面全是日文的,估计是想改成英文版或者中文用。说是需要先提取出其中的固件包,然后改包。
固件存储在一个106点的BAG Flash上,需要热风枪拆下上编程器读,有540M


固件分析binwalk必出 :
DECIMAL HEXADECIMAL DESCRIPTION -------------------------------------------------------------------------------- 735802 0xB3A3A Android bootimg, kernel size: 0 bytes, kernel addr: 0x41564E49, ramdisk size: 541346124 bytes, ramdisk addr: 0x544F4F42, product name: "EAD RAMDISK IMAGE" 33177728 0x1FA4080 Android bootimg, kernel size: 5601232 bytes, kernel addr: 0x46E10000, ramdisk size: 413525 bytes, ramdisk addr: 0x48008000, product name: "" 33182048 0x1FA5160 Linux kernel ARM boot executable zImage (little-endian) 33201222 0x1FA9C46 gzip compressed data, maximum compression, from Unix, last modified: 1970-01-01 00:00:00 (null date) 39091808 0x2547E60 gzip compressed data, from Unix, last modified: 1970-01-01 00:00:00 (null date) 39528128 0x25B26C0 gzip compressed data, maximum compression, from Unix, last modified: 2017-09-22 03:16:36 46448768 0x2C4C080 Android bootimg, kernel size: 5601232 bytes, kernel addr: 0x46E10000, ramdisk size: 413525 bytes, ramdisk addr: 0x48008000, product name: "" 46453088 0x2C4D160 Linux kernel ARM boot executable zImage (little-endian) 46472262 0x2C51C46 gzip compressed data, maximum compression, from Unix, last modified: 1970-01-01 00:00:00 (null date) 52362848 0x31EFE60 gzip compressed data, from Unix, last modified: 1970-01-01 00:00:00 (null date) 52799168 0x325A6C0 gzip compressed data, maximum compression, from Unix, last modified: 2017-09-22 03:16:36 59721940 0x38F48D4 Flattened device tree, size: 73696 bytes, version: 17 59799700 0x3907894 Flattened device tree, size: 79201 bytes, version: 17 77690934 0x4A17836 LZMA compressed data, properties: 0x9A, dictionary size: 1073741824 bytes, uncompressed size: 64 bytes 77691008 0x4A17880 gzip compressed data, maximum compression, has original file name: "balong_modem.bin", last modified: 2017-09-22 03:28:01 123906240 0x762A8C0 ELF, 32-bit LSB shared object, ARM, version 1 (SYSV) ... ... 530241648 0x1F9AD870 ASCII cpio archive (SVR4 with no CRC), file name: "lib/libbhalapi.so", file name length: "0x00000012", file size: "0x00006460" 530268858 0x1F9B42BA ASCII cpio archive (SVR4 with no CRC), file name: "lib/libnvram.so", file name length: "0x00000010", file size: "0x00004438" 530340716 0x1F9C5B6C ASCII cpio archive (SVR4 with no CRC), file name: "lib/libnl_2.so", file name length: "0x0000000F", file size: "0x000033FC" 530354866 0x1F9C92B2 ASCII cpio archive (SVR4 with no CRC), file name: "lib/pptp.so.0.0.0", file name length: "0x00000012", file size: "0x0000A5E8" 531147486 0x1FA8AADE ASCII cpio archive (SVR4 with no CRC), file name: "bin/web", file name length: "0x00000008", file size: "0x00034DE0" 532604500 0x1FBEE654 ASCII cpio archive (SVR4 with no CRC), file name: "bin/ethcmd", file name length: "0x0000000B", file size: "0x000034D4" 532618862 0x1FBF1E6E ASCII cpio archive (SVR4 with no CRC), file name: "bin/upnp", file name length: "0x00000009", file size: "0x00014604"
Android bootimg
前几行就给出了很重要的一些信息,Android bootimg,kernel size: 5601232 bytes, kernel addr: 0x46E10000, ramdisk size: 413525 bytes,"Copyright (c) 2009-2012, ARM Limited "既然是安卓那就想办法把ADB运行起来就方便多了。现在能访问串口,可以看到启动相关信息:
onchip NF id boot! Nand save 0x8A000121 UnSec_boot!mddrc init ok 13 src_addr :0x00080000 dst_addr :0x4FD00000 img_size :0x00031F50 4 sec disable 56 Start mic now ... /proc/power_on open failed start_mode = 0 ifconfig: SIOCGIFFLAGS: No such device ATP_FOM_RET_OTHER_ERR err1 ATP_FOM_RET_OTHER_ERR err1 GlobeMac Init OK NV_Read: Para is Error ... ---------------------------Welcome To Cli--------------------------- --SBA3p, B610s-79aTCPU-V100R001B193D09SP00C643, 7C:A1:77:86:xxx4-- -------------------------------------------------------------------- Login: Login incorrect! Login: supervisor Password: failed 1 times ;10次后会锁住,需要重启
可以通过CLi执行简单的命令,root密码不知道,用普通帐号supervisor先玩玩,进入后输入 ?显示帮助命令
SBA3p#? A_threshold A_Threshold configuration command B_threshold B_Threshold configuration command dns-proxy Set DNS info dump Dump tcp log exit Cli logout lan LAN configuration commands loaddefault Load factory default settings lte LTE command RSRP_check_time TDD check RSRP interval configuration command RSRP_threshold TDD RSRP threshold configuration command uptime_threshold FDD uptime threshold configuration command reboot_counter FDD max reboot counter configuration command nvram nvram command ping Ping provision get provision status random Random reboot configuration command reboot Reboot Command save Save system settings into nvram show show commands simlock Query or unlock simlock syslog syslog command telnet telnet configuration tftp firmware upgrade by tftp server totaluptime Show total uptime traceroute Traceroute upgrade upgrade commands upnp UPnP configuration uptime Show system uptime usb USB status version Display firmware version wan WAN configuration commands wlan wlan command version: OS Version: android 4.4.1 2.4GHz Driver (BCM43217) 5GHz Driver (BCM4352) soft version: 11.193.09.00.643 hard version: WL1B610M
也没用过,随便试几个命令吧
## SBA3p#show cpu ;## SBA3p#show task也差不多内容 User 0%, System 0%, IOW 0%, IRQ 0% User 1 + Nice 0 + Sys 1 + Idle 297 + IOW 0 + IRQ 0 + SIRQ 0 = 299 PID PR CPU% S #THR VSS RSS PCY UID Name 1266 0 0% R 1 1288K 496K root top 2 0 0% S 1 0K 0K root kthreadd 3 0 0% S 1 0K 0K root ksoftirqd/0 4 0 0% S 1 0K 0K root kworker/0:0 5 0 0% S 1 0K 0K root kworker/0:0H 6 0 0% S 1 0K 0K root kworker/u2:0 7 0 0% S 1 0K 0K root rcu_preempt 8 0 0% S 1 0K 0K root rcu_bh 9 0 0% S 1 0K 0K root rcu_sched 10 0 0% S 1 0K 0K root khelper 11 0 0% S 1 0K 0K root netns 12 0 0% S 1 0K 0K root rdr_syserr 14 0 0% S 1 0K 0K root softtimer_wake 15 0 0% S 1 0K 0K root softtimer_nowak 16 0 0% S 1 0K 0K root icc_shared 17 0 0% D 1 0K 0K root dump_ap_save 18 0 0% S 1 0K 0K root writeback 19 0 0% S 1 0K 0K root bioset 20 0 0% S 1 0K 0K root crypto 21 0 0% S 1 0K 0K root kblockd 22 0 0% S 1 0K 0K root lpm3_dump 23 0 0% S 1 0K 0K root led_dr_gpio 24 0 0% S 1 0K 0K root bsp_pmic_irq 25 0 0% S 1 0K 0K root khubd 26 0 0% S 1 0K 0K root NET_LINK_WQ 27 0 0% S 1 0K 0K root kworker/0:1 28 0 0% S 1 0K 0K root kswapd0 29 0 0% S 1 0K 0K root fsnotify_mark 41 0 0% S 1 0K 0K root yaffs-bg-1 42 0 0% S 1 0K 0K root yaffs-bg-1 43 0 0% S 1 0K 0K root rfile 44 0 0% S 1 0K 0K root EncSrc 45 0 0% S 1 0K 0K root EncDst 46 0 0% S 1 0K 0K root DecSrc 47 0 0% S 1 0K 0K root DecDst 48 0 0% S 1 0K 0K root socpProc 49 0 0% S 1 0K 0K root drv_nv 50 0 0% D 1 0K 0K root virtshl_rfunc 51 0 0% D 1 0K 0K root virtshl_sfunc 52 0 0% D 1 0K 0K root uartfile_recv_t 53 0 0% D 1 0K 0K root dump_save 54 0 0% S 1 0K 0K root pmic_exc_om 55 0 0% S 1 0K 0K root kworker/u2:1 56 0 0% D 1 0K 0K root VOS_TIMER 57 0 0% D 1 0K 0K root RTC_TIMER 58 0 0% D 1 0K 0K root AppDS 59 0 0% D 1 0K 0K root AppNdisPppDipc 60 0 0% D 1 0K 0K root RNIC 61 0 0% D 1 0K 0K root ACPU_NFEXT 62 0 0% S 1 0K 0K root F4_I0 1 0 0% S 1 516K 332K root /init 64 0 0% D 1 0K 0K root ADS_DL 65 0 0% D 1 0K 0K root CSD 66 0 0% D 1 0K 0K root TAF_AGENT 67 0 0% D 1 0K 0K root CpuLoadMonitor 68 0 0% D 1 0K 0K root ACpuFlowCtrl 69 0 0% D 1 0K 0K root CBT 70 0 0% D 1 0K 0K root F11_I0 71 0 0% D 1 0K 0K root USIM 72 0 0% D 1 0K 0K root PCVOICE 73 0 0% D 1 0K 0K root PAM_OM 74 0 0% D 1 0K 0K root mspAppDiag 75 0 0% D 1 0K 0K root F15_I0 76 0 0% D 1 0K 0K root F15_I1 77 0 0% S 1 0K 0K root F15_I2 80 0 0% S 1 0K 0K root usb_notify 81 0 0% S 1 0K 0K root usb_notify 82 0 0% S 1 0K 0K root usb_hotplug 83 0 0% S 1 0K 0K root cfinteractive 84 0 0% D 1 0K 0K root RebTask 85 0 0% S 1 0K 0K root deferwq 86 0 0% S 1 0K 0K root kworker/u2:2 87 0 0% S 1 0K 0K root acm_cdev 88 0 0% S 1 0K 0K root acm_mdm 89 0 0% S 1 0K 0K root otg 90 0 0% S 1 500K 196K root /sbin/ueventd 91 0 0% S 1 0K 0K root yaffs-bg-1 92 0 0% S 1 0K 0K root yaffs-bg-1 93 0 0% S 1 0K 0K root yaffs-bg-1 94 0 0% S 1 468K 144K root /sbin/watchdogd 162 0 0% S 1 1148K 560K root mlogserver 187 0 0% S 8 6036K 3160K root mic 242 0 0% S 1 6148K 2936K root /app/bin/cms 243 0 0% S 3 3840K 1148K root /app/bin/atserver 244 0 0% S 1 4572K 1516K root /app/bin/dialup 245 0 0% S 8 2880K 896K root /app/bin/net 246 0 0% S 8 2792K 856K root /app/bin/modeswitch 247 0 0% S 1 1996K 880K root /app/bin/syslog 248 0 0% S 9 3144K 924K root /app/bin/tftpupg 249 0 0% S 14 6028K 1916K root /app/bin/device 251 0 0% S 8 2372K 848K root /app/bin/multiupg 253 0 0% S 1 1624K 616K root /app/bin/sbbRandomReboot 254 0 0% S 1 4612K 1852K root /app/bin/wlan 256 0 0% S 8 4580K 1136K root /app/bin/telnet_server 518 0 0% S 1 4648K 1308K root /app/bin/authconsole 525 0 0% S 1 0K 0K root kworker/0:2 555 0 0% S 1 1904K 772K root /app/bin/dhcps 556 0 0% S 1 1868K 700K root /app/bin/ipcheck 635 0 0% S 1 4148K 1160K root /app/bin/dns 1187 0 0% S 1 1944K 860K root /system/bin/bcm4352/exe/eapd 1190 0 0% S 1 2260K 432K root /system/bin/bcm4352/exe/nas 1206 0 0% S 1 2236K 616K root /system/bin/bcm4352/exe/wps_monitor 1211 0 0% S 1 4820K 856K root acsd 63 0 0% D 1 0K 0K root ADS_UL
/app/bin目录下的内容很显眼,多关注下,有telnet_server?现在不知道用户密码,tftpupg可能是升级时用的,猜测mic是正常启动时第一个开的app,日志中开始有这个出现。去固件中查找mic 相关的字符串,找到类似开机脚本类的
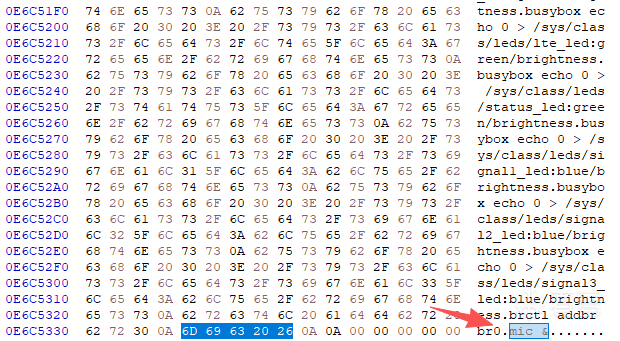
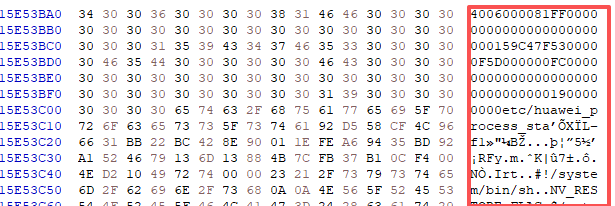
找到两处,第二处可以看到类似分区表相关的,脚本应该是来自/etc/huawei_process_sta,因为是Nand芯片RAW提取的,会有些Nand规范的插入字节,如坏块标志,hash值,一块0x10e0大小的逻辑块会插入几处,具体也不清楚是规范(OOB),尝试手工提取没成功,放弃了。
## OOB 分析 79a OOB分析 Offset -------------------------------------------------- 0x0000 ──────────────┐ │ │ Data0[0:0x408] │ 0x0408 ──────────────┼── ECC / Meta (0x2A bytes) ❌ 0x0432 ──────────────┤ │ DATA1[432:839] 0x0408 ──────────────┼── ECC / Meta (0x2A bytes) ❌ 0x0432 ──────────────┤ │ DATA2[864:C6B] 0x0408 ──────────────┼── ECC / Meta (0x2A bytes) ❌ 0x0432 ──────────────┤ Data #1 │ DATA3[C96:FFF] 0x1000 ──────────────┼── Page Tail OOB (0xE0) ❌ FF FF DATA4[1002:107F] 0x1080 ────────────── 0x10E0 ──────────────┘
简单点直接替换修改原来内容,尽量少改动,mic & 这个app后台运行前还有多处led灯亮的指令“busybox echo 1 > /sys/class/leds/power_led:green/brightness”,真替换这个应该不会有什么大问题。焊接不方便尽量搞成一劳永逸的方式,比如开机脚本中开adb,telnet.
网卡配置是在mic中启用的,之前网络不能用,应该可以在开机脚本中开启。为 了省事,就在mic &后延时再执行脚本吧。
mic & sleep 66 #用busybox 的tftp 传出需要的内容进一步分析,升级的文件一般在/online下 busybox tftp -p -l /online/*.bin 192.168.3.100 PC端接收用Tftpd64: [object Object]
修改raw固件重新写回(这个操作其实执行了多次,中间多次改版脚本),成功提取到需要的升级文件firmward1.bin,后续再修改重新打包就行了,不过那些不需要我处理了。
这是比较简单的一个方法,其实还有多种手段可以实现注入自己的东西,以后再研究吧。
更多【智能设备-华为巴龙系路由器固件提取及修改】相关视频教程:www.yxfzedu.com
相关文章推荐
- CTF对抗-2022MT-CTF Re - 游戏基址二进制漏洞 密码应用智能设备
- 编程技术-逆向IoRegisterPlugPlayNotification获取即插即用回调地址,配图加注释超级详细 - 游戏基址二进制漏洞 密码应用智能设备
- 软件逆向-针对百度旗下的一个会议软件,简单研究其CEF框架 - 游戏基址二进制漏洞 密码应用智能设备
- Android安全-逆向篇三:解决Flutter应用不能点击问题 - 游戏基址二进制漏洞 密码应用智能设备
- Android安全-Android - 系统级源码调试 - 游戏基址二进制漏洞 密码应用智能设备
- Android安全-逆向分析某软件sign算法 - 游戏基址二进制漏洞 密码应用智能设备
- 软件逆向-APT 双尾蝎样本分析 - 游戏基址二进制漏洞 密码应用智能设备
- 编程技术-利用GET请求从微软符号服务器下载PDB - 游戏基址二进制漏洞 密码应用智能设备
- 编程技术-NtSocket的稳定实现,Client与Server的简单封装,以及SocketAsyncSelect的一种APC实现 - 游戏基址二进制漏洞 密码应用智能设备
- 软件逆向-wibu证书 - asn1码流 - 游戏基址二进制漏洞 密码应用智能设备
- 软件逆向-关于USB管控的方案,某某USB管控逆向分析 - 游戏基址二进制漏洞 密码应用智能设备
- 编程技术-谁会不喜欢一个Windows内核键盘记录器呢(详解) - 游戏基址二进制漏洞 密码应用智能设备
- 编程技术-QEMU/KVM虚拟机运行核心流程 - 游戏基址二进制漏洞 密码应用智能设备
- 编程技术-一点小技巧:利用Hook实现内存Dll(Dll数据重定向) - 游戏基址二进制漏洞 密码应用智能设备
- 软件逆向-wibu证书 - 初探 - 游戏基址二进制漏洞 密码应用智能设备
- CTF对抗-【2022 羊城杯】 WP(部分) - 游戏基址二进制漏洞 密码应用智能设备
- 软件逆向-IDA 驱动vmp变异 去花指令 IDC脚本 - 游戏基址二进制漏洞 密码应用智能设备
- 2-某通Vpn V2.2.12 逆向破解Vip线路 - 游戏基址二进制漏洞 密码应用智能设备
- 二进制漏洞- V8 Array.prototype.concat函数出现过的issues和他们的POC们 - 游戏基址二进制漏洞 密码应用智能设备
- CTF对抗-2022-长城杯初赛Write up-by EchoSec安全团队 - 游戏基址二进制漏洞 密码应用智能设备
2):严禁色情、血腥、暴力
3):严禁发布任何形式的广告贴
4):严禁发表关于中国的政治类话题
5):严格遵守中国互联网法律法规
6):有侵权,疑问可发邮件至service@yxfzedu.com
- 网络-各大电商平台API接口调用,对接拼多多开放平台API接口获得商品详情实时数据演示
- r语言-gpt支持json格式的数据返回(response_format: ‘json_object‘)
- pdf-pdf.js不分页渲染(渲染完整内容)
- 自动驾驶-自动驾驶学习笔记(八)——路线规划
- pdf-Word转PDF简单示例,分别在windows和centos中完成转换
- spring boot-java 企业工程管理系统软件源码+Spring Cloud + Spring Boot +二次开发+ MybatisPlus + Redis
- python-利用 Google Artifact Repository 构建maven jar 存储仓库
- python-PyCharm因安装了illuminated Cloud插件导致加载项目失败
- list-list复制出新的list后修改元素,也更改了旧的list?
- 语言模型-论文导读 | 融合大规模语言模型与知识图谱的推理方法